
Getty Images/iStockphoto
New RAT campaign abusing AWS, Azure cloud services
Cisco Talos discovered threat actors taking advantage of public cloud services to spread remote administration tools such as NanoCore, NetWire and AsyncRAT.
Malware operators are taking advantage of the two most popular public cloud services in AWS and Microsoft Azure to launch a new set of remote administration tool attacks.
A Cisco Talos report Wednesday said an unknown crew of cybercriminals has been spreading a trio of RAT payloads with the aim of stealing data from infected machines. The RAT campaign has been operating since late October, according to Cisco Talos researchers Chetan Raghuprasad and Vanja Svajcer.
"These variants of Remote Administration Tools (RATs) are packed with multiple features to take control over the victim's environment to execute arbitrary commands remotely and steal the victim's information," the researchers explained in a blog post.
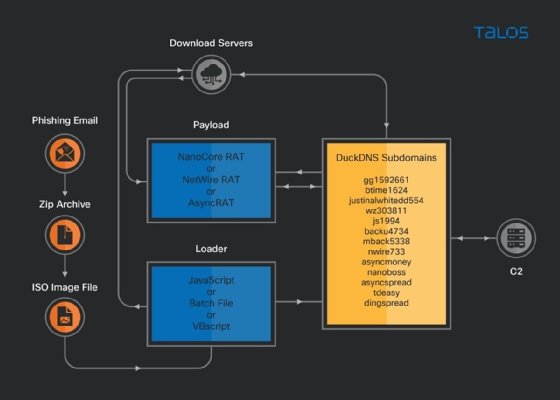
According to the Cisco Talos team, the malware payload can vary, but in each case a known RAT package is disguised as an attachment to a phishing email. The malware has been identified as variants of the NanoCore, NetWire or AsyncRAT families, which have been used in the past for everything from business email compromise attacks to cyberespionage campaigns.
What is common to each of the infections, the researchers said, is the backbone used to manage the malware. Once infected, the malware runs a script that connects to a command-and-control server running on either an Azure cloud-based Windows server or an AWS EC2 instance.
The Cisco Talos researchers found that once the RAT receives the commands from the cloud server, the malware then dials up another server that runs through DuckDNS, a free dynamic DNS service. The threat actors use DuckDNS to change the domain names of the command-and-control servers and route connections to one of several subdomains.
Once it obtains a foothold and establishes contact with its command-and-control network, the Trojan then gives itself persistence on the host machine and then looks to lift data including credentials and credit card numbers.
As with most malware campaigns, the RAT attacks are largely targeting systems in Europe and North America, with the U.S., Canada, and Italy being the most popular targets. Singapore, Spain and South Korea were also among the most commonly infected locations.
Cisco Talos is advising administrators to counter the attack by looking for the scripts and other tell-tale signs of the RAT's activity.
"Defenders should monitor traffic to their organization and implement robust rules around the script execution policies on their endpoints," Raghuprasad and Svajcer said in the blog post. "It is even more important for organizations to improve email security to detect and mitigate malicious email messages and break the infection chain as early as possible."
The abuse of public cloud services by threat actors to manage command-and-control servers has been observed in the past. However, Cisco Talos said this type of activity is becoming more common.
"Threat actors are increasingly using cloud technologies to achieve their objectives without having to resort to hosting their own infrastructure," Raghuprasad and Svajcer said.
"These types of cloud services like Azure and AWS allow attackers to set up their infrastructure and connect to the internet with minimal time or monetary commitments. It also makes it more difficult for defenders to track down the attackers' operations."







