
Getty Images/iStockphoto
Eclypsium calls out Microsoft over bootloader security woes
At DEF CON 30, Eclypsium researchers detailed three new vulnerabilities in third-party Windows bootloaders that were signed with Microsoft's UEFI certificates.
LAS VEGAS -- Eclypsium researchers criticized Microsoft for its response to the discovery of three new bootloader vulnerabilities that could be exploited to gain control of systems during the boot process.
During a DEF CON 30 session Friday, security platform provider Eclypsium's researchers delved into the vulnerabilities, which were disclosed in Microsoft's Patch Tuesday release this week.
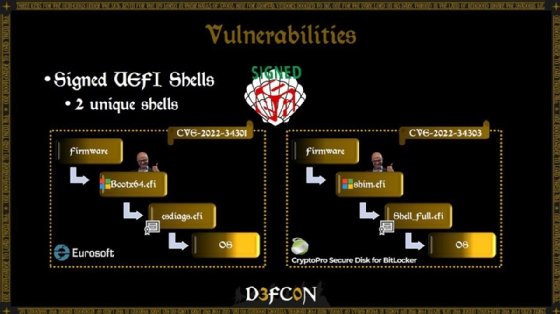
The three vulnerabilities exist in third-party bootloaders: Eurosoft (CVE-2022-34301), New Horizon DataSys (CVE-2022-34302) and Kidan's CryptoPro Secure Disk for BitLocker (CVE-2022-34303).
By exploiting the vulnerabilities, threat actors could bypass Secure Boot, a security protocol used by OEMs and operating system vendors to ensure bootloaders and Unified Extensible Firmware Interface (UEFI) drivers are authenticated through valid digital signatures. Bypassing the Secure Boot checks would allow threat actors to commit attacks, such as modifying the OS, disabling security controls and installing backdoors.
While the bootloaders in question are not Microsoft products, they are cryptographically signed by the software giant's UEFI third-party certificate authority (CA). The issue, according to Eclypsium principal researchers Jesse Michael and Mickey Shkatov, is that Microsoft signs bootloaders without a complete code analysis.
"These third-party vendors will submit their bootloaders for review to Microsoft, but different vendors have different levels of security maturity," Michael told SearchSecurity.
As a result, a bootloader that threat actors have tampered with would still pass the Secure Boot check. "It's only verifying that it's the code you expect on the system. It's not verifying that the code is good or bug-free," Michael said, adding that vulnerable bootloaders can create supply chain threats.
Even though Microsoft has a huge presence in the UEFI Secure Boot ecosystem since it established its own CA in 2011, Shkatov said the company hasn't provided much visibility of its bootloaders to the infosec community.
"There are X amount of bootloaders in the world signed by Microsoft since 2011. There's only one organization that knows how many bootloaders and which versions are out there," he said. "And there are exactly zero external organizations that they're willing to share that information with."
If there's any company that can own the ecosystem and is in a position to verify the bootloaders, Shkatov said, it's Microsoft. "But all you hear from them is crickets."
The bootloader vulnerabilities
During the DEF CON presentation, Michael and Shkatov detailed the three bootloader vulnerabilities, which they likened to the BootHole vulnerability Eclypsium discovered in the GRUB2 Linux bootloader in 2020. Two of the flaws, CVE-2022-34301 and CVE-2022-34303, are similar because the respective vendors, Eurosoft and Kidan, use signed UEFI shells in their bootloaders.
The researchers explained that an attacker could use the shells to evade Secure Boot checks. "They're not good if you want security," Shkatov said during the presentation.
The malicious shell activity involves visual elements that could potentially be detected by users on workstation monitors during the boot process; however, the vulnerabilities are especially dangerous for servers and industrial control systems that lack displays.
The third vulnerability, CVE-2022-34302, is even harder to detect, as exploitation would remain virtually invisible to system owners. The researchers discovered that the New Horizon DataSys bootloader contains a small file that acts as a built-in bypass for Secure Boot; the 73 KB file disables the Secure Boot check without turning the protocol off completely, and it also has the ability to execute additional bypasses for security handlers.
The discovery of the Horizon DataSys built-in Secure Boot bypass was definitely a "holy crap moment," Shkatov told SearchSecurity.
The researchers said admin access is required for full exploitation, but they demonstrated an exploit during the presentation that used a phishing email and a malicious Word document that elevated their privileges to admin. "Going from user [access] to admin is not exactly difficult," Michael told the audience.
In a blog post about the flaws, Eclypsium noted that CVE-2022-34302 is likely to be used in the wild because exploitation is relatively simple.
The researchers said during the presentation that none of the bootloader vendors responded to the vulnerability reports.
Microsoft's response
Microsoft issued Windows updates on Tuesday to address the three bootloader vulnerabilities. In previous cases with bootloader vulnerabilities, the software giant did not issue updates, Shkatov said.
"I think they freaked out enough to do something about it," he said.
However, getting to that point was difficult, the researchers said. Having dealt with Microsoft before on bootloader security issues, they anticipated that they weren't going to get any information from the company about the bootloader vendors and the specific versions that were affected. Instead, they reported the flaws directly to Microsoft and asked the company to lead the response.
Michael and Shkatov asked for CVE numbers, but Microsoft at first declined because, according to the researchers, the company's policy is to assign CVE numbers only for Microsoft products, not third-party code.
Eclypsium argued that because Microsoft authorized these bootloaders with its UEFI Secure Boot CA, it had a responsibility to address the issues. "Effectively, the reason these are important vulnerabilities is because Microsoft signed the code," Michael said.
The researchers asked the CERT Coordination Center for assistance, and the organization helped coordinate the response and assigned CVEs to the flaws.
The researchers weren't made aware that the three bootloader vulnerabilities would be disclosed on Tuesday. Originally, Microsoft had planned to reveal them in July, but postponed the disclosure. "The lack of transparency has been very frustrating," Michael said.
Microsoft did not respond to request for comment at press time.
UPDATE: A Microsoft spokesperson sent the following statement to SearchSecurity: "These bootloaders are not owned by Microsoft and we do not own the code so it would not be appropriate for us to handle the CVEs for them. They were coordinated by CERT/CC, the appropriate group to coordinate disclosure across multiple groups."
Despite those frustrations, Michael acknowledged the positive changes Microsoft has made to the Secure Boot ecosystem over the last 10 years.
"I think, in general, the security posture of the system has been getting better," he said, adding that a recent Eclypsium blog post gave credit to Microsoft for spearheading many initiatives to strengthen security.
But those efforts aren't enough, according to the researchers -- especially with the rise of firmware attacks and malicious bootloaders, as well as growing threats to the software supply chain.
"If we had the ability to enumerate all of the bootloaders and do some kind of verification, I'd feel a little bit better," Michael said.






