
arthead - stock.adobe.com
Cybercriminals launching more MFA bypass attacks
New research from Okta shows that cybercrime groups have stepped up their attacks on multifactor authentication systems in an effort to thwart account security measures.
Cybercrime groups are stepping up their efforts to target multifactor authentication methods in order to compromise accounts.
This is according to a report from Auth0, a subsidiary of identity and access management vendor Okta. The report said that MFA codes such as one-time passwords are the hot new item for cybercriminals looking to break into networks.
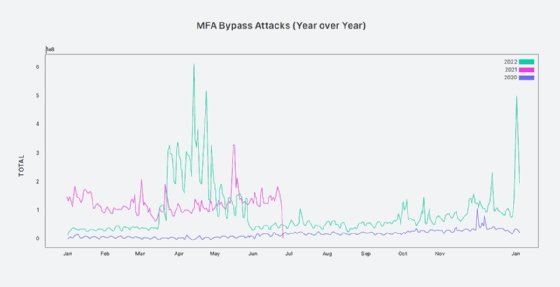
On the year, MFA attacks are at their highest levels ever, up significantly from 2021 and far exceeding levels seen in 2020, Okta said. In the first 90 days of this year alone, its network logged roughly 113 million attacks targeting MFA.
"Because of its proven merits, more application and service providers are recommending or requiring MFA," Okta's Auth0 team said in the report. "Consequently, the first half of 2022 has seen a higher baseline of attacks against MFA than any previous year in our dataset."
The researchers focused on MFA bypass techniques and found that they fell into one of two categories: either brute-forcing the two-factor process and attempting to guess the code, or using social engineering to trick a targeted user into generating the code and approving a fraudulent access request.
In the latter case, Okta said many attackers have been relying on fatigue tactics that involve bombarding the user with repeated code requests -- often claiming to be from IT or support staff -- via SMS or other messaging tools. Eventually, the user relents and approves the valid MFA challenge, allowing the attacker to gain access to the device.
Such a scenario arose earlier this month when a hacker associated with the Lapsus$ cybercrime group broke into Uber's corporate network. The ride-sharing company was eventually able to trace the breach back to a single contractor account that had two-factor authentication (2FA) enabled. The attacker generated repeated 2FA requests to the contractor in an attack technique also known as MFA bombing, and the contractor eventually approved one of the requests, unaware that a threat actor was generating the alerts.
Okta principal threat intelligence researcher Mathew Woodyard told TechTarget Editorial that the Uber break-in was a clear example of the social engineering attacks that Okta's researchers have seen in the wild.
"Applying brute force to either guess the authentication code or create alert fatigue is the most common attack vector we see in MFA bypass attempts," Woodyard said in an email. "In this case, the attacker combined an element of social engineering -- impersonating an Uber IT person on WhatsApp -- with alert fatigue."
The Auth0 report noted that the success of such attacks depends on targets being unaware that an attack is in progress. As an example, the research team cited a monthlong campaign against a travel site in Europe that targeted 50 phone numbers with more than 100 MFA-related SMS messages each.
"Consider how a user might behave in that situation: Would they recognize the onslaught of MFA requests as the signs of an attack, or would they think that the service was simply being 'buggy'?" the report said. "Would they approve a request or perhaps change their configuration to turn off MFA?"
The increased use of social engineering to bypass MFA protections will pose yet another threat to network defenders and administrators who have long considered MFA to be a solid means of guarding against account compromises and credential theft. While passwords remain static and can be stolen from third parties or lifted in data breaches, MFA codes have been far harder to steal and extract because they require direct interaction from the user at the time of login.
Woodyard said the fatigue factor is what makes these attacks particularly insidious. While users can be educated on the tricks attackers use, they might still wear down and be caught off guard by social engineering tricks.
"We can provide the guidance to our users that if they receive an endless wave of MFA push notifications, they should not approve the MFA request, and not talk to unknown people claiming to be from your organization," Woodyard noted. "But this is not enough, and we are still placing a heavy burden on our users who are just trying to get their jobs done or buy something online."
The rise in MFA bypass attacks was not the only trend the researchers observed over the last year. The Auth0 team also noted that sign-up fraud -- in which attackers create fake accounts on a large, automated scale -- was also up on the year. This includes cases such as registering fake accounts to take advantage of giveaways or creating sock puppet accounts to resell for spam or disinformation campaigns.
Credential stuffing also remains a favored tactic, even as MFA attacks rise. The researchers found that in the first 90 days of the year, some 10 billion events were logged on the Okta network, accounting for 34 percent of all login events.
In those cases, e-commerce sites were the most likely targets, as attackers sought to nab shopper accounts by testing for reused passwords and usernames. Financial services and entertainment platforms were also popular stuffing targets.







