
Getty Images/iStockphoto
Cybereason warns of fast-moving Black Basta campaign
Threat actors with the Black Basta ransomware-as-a-service group are compromising networks in as little as one hour and stealing sensitive data before disabling DNS services.
Black Basta ransomware actors are utilizing extreme speed and a new tactic that makes it increasingly difficult for enterprises to respond to an attack, according to new research by Cybereason.
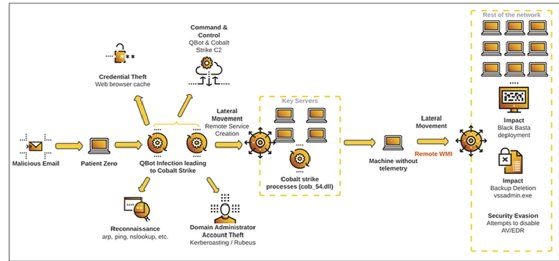
In the latest campaign observed by the Cybereason Managed Services team, threat actors obtained administrative access in less than two hours and deployed Black Basta ransomware in less than 12 hours. A blog post Wednesday detailed the tactics and techniques, including the use of the QakBot banking Trojan to gain initial access and the targeting of domain name system (DNS) services to lock enterprises out of the network.
Deemed a high-level threat due to the potential widespread activity, Cybereason warned the campaign can "quickly lead to severe IT infrastructure damage." The campaign has been active since at least Nov. 14 and largely targets U.S.-based organizations.
The observed threat activity begins with spear phishing emails, followed by the deployment of QakBot to infect an environment and maintain presence on victims' networks. QakBot can be used to steal financial data, including keystrokes and credentials, according to Cybereason.
In the specific incident described in the blog, Cybereason researchers also observed the threat actor using Cobalt Strike during the compromise to gain remote access to the domain controller.
"Once Qakbot has successfully infected an environment, the malware installs a backdoor, allowing the threat actor to drop additional malware -- namely ransomware," Cybereason wrote in the blog post.
The ability to compromise systems so quickly comes down to coordination between the initial access brokers using QakBot and the Black Basta ransomware-as-as-service operation. Previously, Black Basta would buy access from the brokers then leverage it to deploy ransomware. Loic Castel, incident response security analyst at Cybereason, said the transaction in that case would create a slight delay.
Despite the high speed of compromise in the incident, Castel said the threat actor still had time to search for and gather sensitive data. In some cases, Cybereason observed the use of other backdoors such as SystemBC loaded by the threat actor and intended for exfiltration.
"If we look at the data, we saw the threat actor could have launched the ransomware even sooner than when they did. There was a delay. They could have done it in an hour, but they didn't," Castel said. "Did they use that time to do something else that we don't know?"
One possibility, he said, is the threat actor used that time to steal data, which is commonly leveraged in ransom demands.
DNS services disabled
During the past two weeks, Cybereason observed more than 10 customers affected by the recent campaign, according to the blog post. While U.S. companies were most commonly targeted, it is unclear if any other patterns were present, such as specific sectors or industries.
Castel said that most cases, the ransomware activity was detected and prevented. However, he warned that machines that are not well configured or do not have threat detection sensors will be affected by this campaign.
"We definitely see threat actors looking specifically for launching queries on machines, to look for ones that don't have any security products on it," he said.
One new tactic he highlighted was the threat actors disabling DNS services to lock the victim out of the network, which was observed on more than one organization. Shutting down the DNS allows attackers to gain access to Active Directory, which he described as the "central point for any Windows network."
With DNS services offline, administrators and IT support are unable to reach the network, which increases the company's response time while attackers remain in the network to do whatever they want.
"This might be something we see more of in the future. I infer this could be a way for threat actors to add additional arguments to the ransom demand. 'If you pay me, I will resume the service,' for example," Castel said. "For an experienced IT team, it wouldn't be a problem, but for smaller companies or ones that are less experienced, it may be effective."
Cybereason said continual threat hunting, network isolation and endpoint detection and response tools are all important components to combat the new Black Basta campaign.
Castel also emphasized the importance of conducting incident response to ensure that the threat activity is contained and hasn't spread to other systems or parts of the network.
"The reactiveness to this threat is really important," Castel said. "We are talking hours, so anything manual is out of the question."







