
Getty Images/iStockphoto
Cybereason warns of rapid increase in Royal ransomware
Enterprises need to be aware of the group's partial encryption technique because the less data it encrypts, the less chance the activity will be detected by a security product.
Royal ransomware is on the rise as operators have embraced partial encryption to evade detection, a newer technique that's becoming a trend among other ransomware gangs.
The evasion tactics of Royal ransomware were detailed in new research Wednesday by Cybereason security operations analyst Mark Tsipershtein; Eli Salem, security and malware researcher; and Alon Laufer, senior security analyst. Active since early 2022, Royal operators behind the strain were observed using multi-threaded ransomware to accelerate the encryption process, as well as a "unique approach" to evade detection.
Though it is one of the newer gangs to emerge, Royal ransomware is quickly becoming a prolific threat that's only gaining momentum. The group even garnered a government warning to the healthcare sector earlier this month, "due to the historical nature of ransomware victimizing the healthcare community."
Although Cybereason did not observe Royal ransomware targeting specific sectors or countries during its research, it also rated it a high severity threat.
"Cybereason assesses the threat level from Royal ransomware to be high, given the rapid increase in attacks coming from this group over the past 60-90 days," Tsipershtein, Salem and Laufer wrote in the blog.
One reason for its success is due to the partial or intermittent encryption technique, which enables attackers to choose a percentage of the data to encrypt from the file. Operators can then choose to eliminate applications or services that may interfere with their goal.
"Before starting the encryption process, Royal ransomware uses the Windows Restart Manager to check if any of the targeted files to be encrypted are being used to blocked by other applications or services," the blog read.
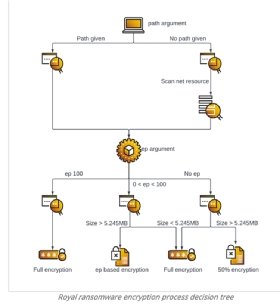
Salem told TechTarget Editorial that partial encryption effectively evades security products because encrypting only a small amount of data will likely fly under the radar of antimalware and threat detection products. Such a small change may not be relevant or big enough for products to detect the presence of ransomware, so it's an advantage to Royal ransomware operators, who can choose how much data to encrypt before they start the attack, he said.
It always makes the ransomware encryption process faster, too.
"If you encrypt less data, it will be faster because you need to make fewer changes when you manipulate the files," Salem said. "If an operator starts to encrypt 50% of data from a file but then he fails because some product stopped him, he can say 'I only want to encrypt 10% to evade detection.'"
Cybereason began observing this trend in the past year and a half, and Salem said the researchers expect to see more and more groups adopt the method because it is more efficient and evasive.
When it comes to enterprises defending against partial encryption, Salem warned that tools relevant in the anti-ransomware landscape three years ago would be practically useless when it comes to the new methods. Awareness is one important step in combatting the threat.
Additionally, Cybereason recommended enabling application control to block the execution of malicious files.
Similarities to Conti
In the short time since its emergence, Royal ransomware operations have greatly evolved. Initially, threat actors used third-party strains such as BlackCat and custom Zeon ransomware, Cybereason discovered. By September the group had developed its own ransomware, dubbed Royal.
Salem emphasized how experienced the operators were in writing the strain, despite it being a relatively new group.
"The ransomware was written efficiently and looked like methods we've seen other groups use in the past. We saw some similarities or inspiration from Conti in some cases," he said.
While he can't say for sure, Salem said it's possible that members of the disbanded Conti ransomware group may now be involved with the Royal ransomware group. Conti was one of the more active and notorious ransomware groups in the threat landscape, but the group apparently shut down earlier this year following several leaks of source code and private communications by an anonymous security researcher.
The blog post noted that other groups including Conti, Babuk and LockBit, used the Restart Manager during the partial encryption process for the same purpose it observed Royal ransomware operators using. The authors also highlighted the fact that Royal ransomware encrypts 50% of all files larger than 5.24 MB, which is the same threshold used by Conti ransomware.






