Vice Society ransomware 'persistent threat' to education sector
New research from Palo Alto Networks supports recent government warnings that Vice Society poses an increased risk to K-12 schools and higher education.
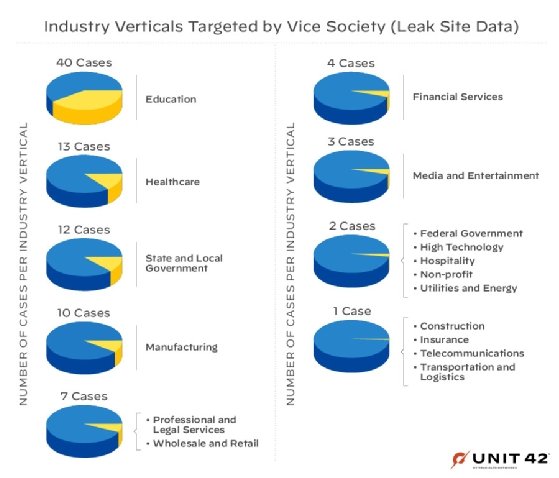
Vice Society is actively targeting the education sector, with 33 schools listed on its public data leak site so far this year, according to new research.
Using information collected from incident response cases and Vice Society's victims list, Palo Alto Networks' Unit 42 threat researcher J.R. Gumarin determined that the ransomware group remains a "persistent threat" to K-12 and higher education institutions. In addition to deploying preexisting ransomware strains such as HelloKitty in attacks, Vice Society stood out for "disproportionately" targeting the education sector compared with operators behind LockBit, Hive, BlackCat and others.
Vice Society poses one of the most significant threats to educational entities, thanks in part to short dwell times. Unit 42 researchers observed threat actors spending up to six days in a targeted environment before being detected, according to a blog post. The median dwell time for ransomware attacks is 28 days, according to the "2022 Unit 42 Incident Response Report," though some ransomware groups such as Black Basta have been seen deploying payloads in as little as 12 hours.
Ryan Olson, vice president of threat intelligence at Unit 42, attributed the group's relatively short dwell times to Vice Society's extensive knowledge of the networks it compromises.
That knowledge comes from the frequent targeting of schools, which Vice Society can do because it doesn't operate like a ransomware-as-a-service outfit with affiliate hackers. It can therefore choose its victims, which in addition to education include the healthcare sector. Once Vice Society gains initial access, operators can move quickly.
"They know what those networks are going to look like, the common applications and the things that will cause harm if they're able to encrypt them," Olson said. "Also, because they aren't using affiliates, there might be a quicker engagement from the ransomware process from the time they intrude the network. Affiliates may intrude a network and not instantaneously pass it off to the ransomware gang they're working with."
Not working with affiliates and writing its own ransomware are two factors that make Vice Society different from other groups.
"Vice Society's use of multiple ransomware payloads across both Windows and Linux hosts shows that they're continually evolving," Gumarin wrote in the blog post.
On the other hand, Vice Society operating as its own organization is helpful from a threat intelligence perspective because it provides a better ability to track the group, Olson said.
Pressure to pay
The new research also detailed ransom demands in incident response cases and the effectiveness of negotiating with Vice Society. While initial demands exceeded $1 million, negotiations brought the number down by as much as 60% in some cases, according to the Unit 42 blog post.
But the threat of Vice Society leaking stolen data to its public site is a big factor when it comes to pressuring victims to pay, Olson said. That pressure only increases for schools because of the sensitive student data involved.
"They will absolutely leak data if people don't pay, and all ransomware actors will," Olson said. "Today, 'professional' ransomware operators are trying to run it as a business. They would rather get paid than leak something prematurely and lose that leverage."
Unit 42 warned schools that Vice Society will likely continue leveraging additional ransomware strains in the future as well as exploiting newly disclosed vulnerabilities. "It's likely they'll maintain use of these tactics to impact the cyberthreat landscape moving forward, as long as their activities continue to be lucrative for them," Gumarin wrote.