
Getty Images
Thousands of victims apparently hit by ESXiArgs ransomware
A joint security advisory from CISA and the FBI said the ESXiArgs ransomware campaign has claimed over 3,800 servers globally since attacks first emerged last week.
Thousands of victims appear to have been hit by the new ESXiArgs ransomware variant, according to multiple internet scans.
ESXiArgs is the name given to a massive ransomware campaign involving the widespread compromise of VMware ESXi hypervisors. Attacks appeared last Friday, with internet-facing servers in nations like the U.S., Canada, France and Germany falling victim. According to an updated advisory by French agency CERT-FR, threat actors appear to be targeting ESXi's Service Location Protocol (SLP) service via multiple serious flaws, including CVE-2021-21974 and CVE-2020-3992.
In the wake of the campaign, researchers have been tracking ESXiArgs to determine the scope and severity of the new ransomware threat. Attack surface management vendor Onyphe, for example, found the number of infections to include 2,112 compromised IP addresses as of Feb. 5.
Ransomwhere, a crowdsourced ransomware payment tracker, published data on Feb. 6 from attack surface management vendor Censys representing over 3,800 victims in primarily Western countries. Using the same Censys data, Ransomwhere said that over 2,800 ransom payment addresses had at the time been collected, and that threat actors had received just four payments totaling approximately $88,000 in bitcoin.
CISA published a joint cybersecurity advisory with the FBI on Wednesday to provide ransomware recovery guidance to victims and complement a ransomware recovery tool published by CISA on Tuesday. The advisory, like Ransomwhere, cites 3,800 as the approximate number of ESXiArgs victims to date.
In a Wednesday blog post, Censys said that infections peaked on Feb. 3, with 3,551 hosts being impacted.
Other researcher datasets provided additional context. A recent Shodan query found nearly 45,000 internet-facing instances of VMware ESXi versions 6.5 and 6.7. Hosting company Ikoula tweeted on Feb. 3 that 6.5 and 6.7 in particular were falling victim to ransomware.
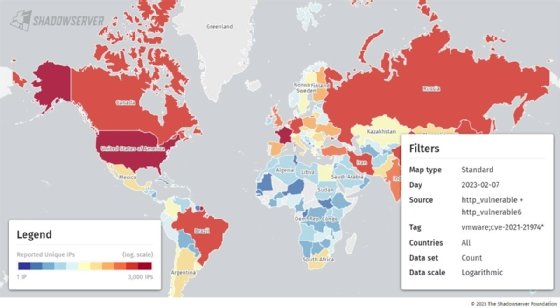
The Shadowserver Foundation, a nonprofit security organization, reported on Tuesday that approximately 27,000 internet-facing ESXi instances were vulnerable to CVE-2021-21974. As of Thursday, that number dropped to 22,653. An updated count is available on the foundation's scanning site.
Additionally, Ransomwhere has published Internet-side scanning data regarding 3,800 victims, courtesy of @censysio.https://t.co/vsWDQzMsLm
— Ransomwhere (@ransomwhere_) February 6, 2023
Shadowserver said on Twitter that the scan, like all internet vulnerability scans, is limited by various factors. For example, Shadowserver's scan does not account for organizations that have applied mitigations but haven't updated.
Shadowserver CEO Piotr Kijewski told TechTarget Editorial via email that the ESXiArgs campaign is "nothing surprising or big" compared to those surrounding infamous flaws like Log4Shell and ProxyShell. But what might be most notable about the campaign is that it is an enterprise-focused ransomware campaign that spread quickly.
"We have a scenario where likely two-year-old or even older exploits were used to target unpatched installations (that, of course, should have been patched long ago)," he said. "So it's to be expected that sooner or later, other types of exposed devices will be attacked by ransomware at scale. Perhaps that is the new thing here: a new ransomware attack spreading relatively fast, with targets being more 'enterprise' style and VMware not being the target of this style of ransomware attack at scale previously."
New variant adds additional complexity
A new variant of EXSiArgs emerged Wednesday that appears to be resistant to existing decryption processes. First reported by BleepingComputer, the new variant apparently uses a new encryption process that renders files above a certain size (128MB) unrecoverable and repels currently-existing EXSiArgs recovery tools.
Censys senior security researcher Emily Austin told TechTarget Editorial that the total number of infected hosts currently remains at just over 3,800, but approximately 900 are hosts that have been reinfected with the new variant. She said that at 2pm ET Wednesday Censys saw indications that the ransomware was being upgraded, "and we’re seeing the results of that today."
Austin shared a Censys scan that showed 968 hosts infected by the new variant as of press time. She added that she felt the timing was a "direct response to CISA's decryptor and observations made by security researchers."
"[Threat actors] likely followed updates from the security community and realized that researchers were tracking their payments, and may have even known before they released the ransomware that the encryption process in the original variant was relatively easy to circumvent," Austin said. "So maybe they took a little time to update and address these things instead of spending more time spreading the original variant."
Asked about whether she anticipates more infections, Austin said that she doesn't think the campaign is going to go away immediately "but we may see more reinfections rather than new hosts affected, based on what we’ve seen thus far."
Alexander Culafi is a writer, journalist and podcaster based in Boston.





