
Getty Images
RSAC speaker offers ransomware victims unconventional advice
Triton Tech Consulting CEO Brandon Clark advised organizations to set aside the stigma of 'negotiating with terrorists' when deciding whether to pay a ransomware gang.
An RSA Conference speaker argued that despite the stigma associated with paying ransomware gangs, it's sometimes better to "negotiate with terrorists."
In his session at the 2023 RSA Conference on Monday, Brandon Clark, CEO of Triton Tech Consulting in Denver, proposed a ransomware response process that works to squeeze out emotive instincts that are often tangled in the decision-making.
"It is absolutely critical that you do take as much of the emotion out of this as possible by looking at some of this ahead of time," Clark said during the session, titled "Negotiating with Terrorists: The High Stakes Game of Ransomware Response."
Clark suggested that ransomware victims often make detrimental decisions based upon emotional and moral instincts. He prefaced his response plan with a reference to the 1973 hostage crisis at the Saudi Arabian Embassy.
In that incident, three Western diplomats, among 10 others, were taken hostage at the embassy by the Black September group. Former President Richard Nixon refused to negotiate with the terrorists and publicly announced the U.S. would not pay the demanded ransom. The terrorists later killed the Western hostages. The remaining hostages were released and returned to their home in Sudan, which had negotiated with the group.
Clark related this piece of history to the life-threatening events that follow a ransomware attack on a hospital or an air traffic controller or other critical infrastructure targets. He stated that aversion to negotiate with terrorists was a polarizing mindset, "entrenched in our mental framework," that has induced poor decision-making.
"If I'm not able to understand a patient's history, if I can't see what their allergic to, and they're given medication that sends them into anaphylactic shock, I would argue that's probably worse and more evil than me paying $50,000 to get our systems back and running," Clark said.
There's also a financial component to the equation. Clark used the 2018 ransomware attack on the city of Atlanta as "a great example of what not to do," because the city government refused to pay a $50,000 ransom and ended up paying more than $3 million in remediation and recovery costs.
"It doesn't make sense for us to go in and spend a million dollars for a $50,000 problem," he said.
Incident response experts, however, often caution ransomware victims that decryptors regularly fail to restore all data and systems -- which Clark acknowledged during his session -- and advise even organizations that pay ransoms to do a full forensic investigation and remediation following an attack.
The FBI and many cybersecurity companies have long argued that compensating ransomware actors will only incentivize more malicious activity. Clark, however, disagreed with that belief; he argued that with the several ways threat actors can monetize the attack, such as selling stolen personal information online, ransomware will continue to hit organizations regardless.
"There's the argument of 'If we pay, then we're just going to encourage more [attacks].' I would honestly argue that they're already encouraged to do more just by the nature of these attacks," he said.
Clark's statements appeared to contradict the advice from another RSA Conference speaker: Deputy Attorney General Lisa Monaco. In her keynote on Monday, Monaco discussed the importance of victims coming forward to work with the FBI and the Department of Justice and commended organizations like Colonial Pipeline Company and Kaseya for contacting law enforcement.
While Colonial Pipeline made the decision to pay a multi-million-dollar ransom, Monaco said coming forward to report attacks is "good for America, because you're helping us prevent that next attack."
But Clark encouraged ransomware victims to put aside the obligations to society and risks posed to others when deciding whether to pay a ransom.
"It's important for us to recognize that at some point, whether or not we pay is kind of irrelevant," he said. "These guys are going to be doing this more anyway."
Negotiating with ransomware actors
Clark offered an approach of trusting threat actors within a ransomware group, arguing that the reputation and track record of a ransomware gang lets people make an informed decision on whether to pay a ransom.
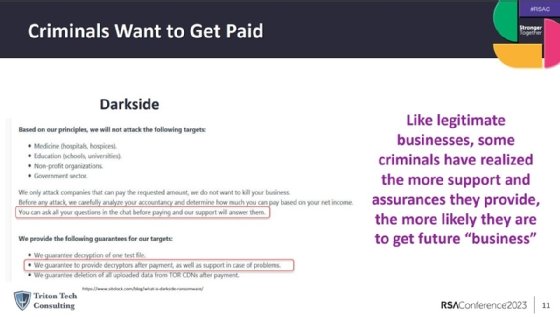
He used the now-defunct DarkSide ransomware gang, which hacked Colonial Pipeline in May 2021, as an example of a certain cybercriminal groups that operate more as business and engage in civil negotiations.
"Just like in traditional business, certain organizations are better at serving their customers than others," said Clark. "For us, that means there are certain organizations that if we work with them, if we negotiate with them, we are more likely to get our data back or operations back."
DarkSide offered customer support lines and guarantees of decryption upon payment, making the gang more trustworthy in the event an organization makes a transaction, according to Clark.
"There's some level of assurance there that they will help you if you pay," he said.







