
peach_fotolia - stock.adobe.com
Authorization sprawl: Attacking modern access models
Attackers exploit authorization sprawl by using legitimate credentials and SSO tokens to move between systems, bypassing security controls and deploying ransomware undetected.
U.K. retailer Marks & Spencer is dealing with the aftermath of a ransomware attack that began with disruptions to customer orders at the end of April. Marks & Spencer disabled its online ordering platform, customers reported empty shelves in stores, employees were told to stay home from work and the company's valuation plummeted by more than half a billion pounds while the security team worked to recover.
The company has said it could take until July to fully recover from the attack; only in mid-June was it able to resume online orders, at limited capacity and shipping.
Many believe the attack against Marks & Spencer is the action of the Scattered Spider team, a collection of English-speaking attackers from the U.S. and the U.K. Scattered Spider is an effective team that uses ransomware or extortion scams to achieve its financial goals.
While the details behind the Marks & Spencer ransomware attack have only been attributed to "human error," if I were to guess, the attack went something like this:
- Initial access. Phishing or social engineering.
- Discovery. Ticketing systems, internal company documentation and email.
- Privilege escalation. Token disclosure or credential reuse.
- Lateral movement. Cloud and on-premises pivoting.
- Ransomware deployment. Ransomware-as-a-service agent deployment.
The Marks & Spencer ransomware attack highlights a growing trend in cybersecurity: Attackers exploit authorization sprawl to bypass traditional defenses. The public breaches against MGM, Caesars Entertainment, Snowflake and U.S. telecommunications firms all share the same trademarks.
Authorization sprawl
Scattered Spider and other threat actors are adapting their attack techniques. Instead of the conventional chain of initial access, privilege escalation and endpoint bypass, these threat actors are using centralized identity platforms that offer single sign-on (SSO) and integrated authentication and authorization schemes. Rather than creating custom malware, attackers use the resources already available to them as authorized users.
Why spend time evading endpoint controls when you can use the SSO and authorization token already available?
In the past, you had to:
— Florian Roth ⚡️ (@cyb3rops) April 23, 2025
phish a user, drop malware, escalate privileges, pivot to servers, evade EDR, dump creds, move laterally, exfiltrate quietly, clean up, leave a backdoor.
Today, you just:
phish a user, steal an OAuth token, access everything from anywhere.
Cloud… https://t.co/rIri6ovfH9
During the RSAC 2025 Conference keynote panel "Top Five Most Dangerous New Attacks," I spoke about this attack trend, explaining how adversaries use the resources allocated to compromised user accounts to discover data, extract access tokens and pivot to cloud and on-premises systems. By abusing modern authorization sprawl, adversaries can pivot from one system to another, exfiltrating data and deploying ransomware without the need for defense evasion, bespoke exploit tools or other alert-generating tactics. For example, consider the following attack chain:
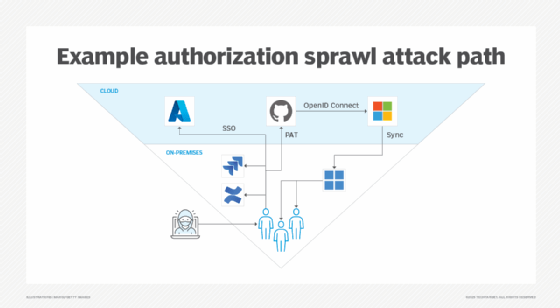
- Attacker buys initial access through an initial access broker.
- Attacker uses logged-in sessions to enumerate ticketing systems or documentation portals for sensitive information.
- Attacker uses SSO to access Microsoft 365 email and document portals, discovering a GitHub personal access token (PAT) in a deleted message.
- Attacker pivots to access GitHub with PAT, enumerating source code, tickets and more documentation.
- Attacker uses PAT to create a GitHub action, accessing Azure resources through Open ID Connect integration.
- From Azure, attacker enumerates resources, identifying Microsoft Entra Connect Sync integrates with on-premises Active Directory (AD).
- Attacker pivots from cloud back to on-premises AD, enumerating users and groups.
- Attacker uses AD privileges to deploy ransomware using Microsoft Endpoint Configuration Manager, Group Policy or PowerShell remoting.
In a world of strong credentials, MFA, endpoint detection and SOC monitoring, attackers face new challenges in accomplishing their goals. They exploit authorization sprawl by using legitimate user access to move seamlessly between on-premises and cloud systems. This attack chain often goes undetected because the attacker sticks to the resources and access already allocated to the user. What's more, the number one tool used by the attacker in an authorization sprawl attack is just the browser on the user's workstation.
The transition to centralized identity platforms, SSO, PATs and interconnected cloud and on-premises platforms has created an opportunity for attackers that evades most existing detection capabilities. Attackers are using this opportunity and modifying their tactics to achieve their goals.
How to mitigate authorization sprawl attacks
To better defend against authorization sprawl attacks, organizations need to improve their defense capabilities in the following three ways:
- Perform cross-platform privilege mapping.
- Require detailed logging capabilities from CSPs during contract negotiations.
- Expand in-browser monitoring and threat detection.
Privilege authorization is complex. Once organizations start to integrate authorization and role-based access controls across multiple platforms, access management becomes exponentially more complex. Few organizations can adequately assess the privileges of a single user across on-premises systems, Microsoft Entra and countless SaaS providers. What organizations need is better privilege discovery and assessment tools that apply graph theory to privilege mapping.
One leader in this space is SpecterOps with its BloodHound product. Well-known for privilege mapping within AD and Azure, recent advancements in BloodHound also perform cross-platform privilege mapping to understand a user's privileges across multiple platforms.
The industry needs more of this integration, taking into consideration the privileges available in source code management systems, such as GitHub; documentation platforms, such as JIRA and Confluence; and other SaaS and IaaS providers.
Alternatively, Microsoft's Security Exposure Management has the benefit of tighter integration with other Microsoft products.
While privilege mapping helps identify potential escalation paths, detailed logging ensures that unusual activity is detected in real time. Some CSPs do an excellent job with logging, giving threat hunting and digital forensics/incident response teams the resources necessary to identify indicators of compromise. However, many CSPs do not provide sufficient resources to identify unusual access patterns, unintended access requests or other activity that could indicate an attack. Notably, many SaaS providers have insufficient logging for threat detection and incident response investigations.
One opportunity to reshape how CSPs provide the logging necessary for effective analysis is to ensure that they comply with a standard for what is needed for threat hunting. The National Security Agency cybersecurity information sheet "Manage Cloud Logs for Effective Threat Hunting" is one such guide, providing well-considered recommendations for CSPs that map to the Mitre ATT&CK and D3FEND frameworks. Requiring that a CSP comply with NSA recommendations for cloud logging can be an effective tool to shape the priorities of providers to meet the requirements needed for effective cloud threat hunting.
Many organizations could also benefit from improved insight into in-browser activity. While many organizations implement web proxy logging for acceptable use compliance and analysis, the logs collected by a proxy server do not provide insight into much of the modern application functionality that happens in the browser, including JavaScript activity and CSS styling and formatting. This creates a visibility gap, where organizations lack insight into activity and use by end users when interacting with on-premises and cloud web applications.
While some vendors have produced browser endpoint detection and response products, these tools are currently limited to defending the browser against attack and do little to identify malicious use of authorized web application resources. More research is needed in this area to identify opportunities to detect anomalous use activity, including suspicious access hours, unusual search activity and out-of-the-ordinary data access.
When we study compromises, we learn that attacker tactics, techniques and procedures change over time. We're seeing the beginning of a trend where attackers sidestep existing detection controls on the endpoint and the network and reuse the access privileges allocated to authorized users. Our ability to adapt our defenses and detection techniques depends on our understanding of privilege escalation paths, our ability to use CSP logging resources for threat hunting and our insight to identify attack patterns using in-browser activity. Failure to do so can lead to catastrophic events that harm our ability to carry out our mission.
Joshua Wright is a SANS Faculty Fellow and Senior Director with Counter Hack Innovations.








