jro-grafik - Fotolia
Tips and tricks to integrate IT and OT teams securely
IT and operational teams can work in tandem to support IoT projects, but their separate roles and responsibilities to one another must be clearly defined.
Successful IoT initiatives can save companies millions of dollars, generate millions in new revenue and improve business processes. Research from my firm, Nemertes, found that the enterprises with the most fruitful IoT deployments launched them in the recent past.
However, there's a price for this prosperity: Most IoT projects are deployed by operational technology (OT) teams without early engagement by IT teams. This ensures that projects are solidly aligned with business objectives, but it means that they may not implement best practices for cybersecurity, architecture or integration with legacy systems.
This price is acceptable in the short term, but over time, it will create complexity and increase the cost of operations thanks to the duplication of resources. Moreover, it creates an incredible amount of vulnerabilities. Many IoT implementations are woefully insecure, due largely to lack of integration with cybersecurity standards and best practices. For starters, enterprises often transport unencrypted IoT data across unprotected networks, and passwords for IoT controllers are often hardcoded by vendors and thus well-known and hackable by perpetrators.
How can IT and OT work more successfully -- and securely -- together? Here are a few tips and tricks to make that happen.
- Engage an IoT evangelist. According to our research at Nemertes, successful organizations are 29% more likely to have a visionary executive sponsor -- someone who sees the transformational potential of IoT and has the ability to encourage the company to embrace it.
- Engage IT early in the process, even before an IoT initiative is launched. You can't protect, secure and support an initiative if you don't know it's happening in the first place. Successful organizations are 23% more likely to have engaged IT in the planning process.
- Have an IoT architecture. Define how IoT should integrate into the organization's existing standards for security, networking, storage, computing, data management and analytics. In addition, specify where and under what circumstances IoT may deviate from the general-purpose IT architecture.
- Have a plan for integrating IoT data into existing systems. Too often, organizations focus on the new and shiny: "We can capture all this data via IoT and analyze it to generate the following information. …"Although the data-capture portion may be new, chances are organizations have an existing set of systems to analyze data; IoT data is one data source, but it shouldn't be its own system.
- Develop subject-matter expertise in key areas. These, in particular, should include cybersecurity, integration and networking. Having individuals who focus on IoT security, IoT integration and IoT network design correlates positively with success.
- Plan for scale. Successful organizations are 69% more likely to anticipate hypergrowth over the next few years. Achieving success and hypergrowth requires effective automation and smooth operational processes. Focus particularly on the handoffs between IT and OT during operations. In general, IT should handle issues pertaining to infrastructure, while OT focuses on business-specific operational issues.
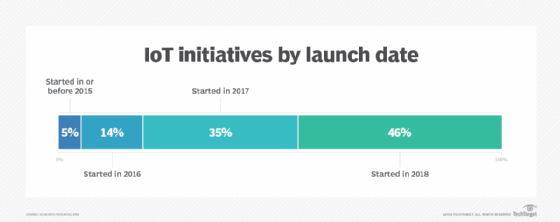
To sum it all up: Where OT teams need the most support tends to be in having a defined architecture and set of best practices, particularly around IoT infrastructure. Where IT teams can generate the greatest value is showing OT how their systems can quickly and reliably be secured and networked; how and where data can be stored and managed, and how to integrate project-specific data into companywide analytics.
Operationally, IT and OT can work in tandem to support IoT projects, if roles and responsibilities are clearly defined.