operational technology (OT)
What is operational technology?
Operational technology (OT) is a category of hardware and software that monitors and controls how physical devices perform.
In the past, OT was used primarily in industrial control systems for manufacturing, transportation and utilities. Unlike IT, the technology that controlled operations in those industries wasn't networked. Many of the tools for monitoring or adjusting physical devices were mechanical, and those that had digital controls used closed, proprietary communication protocols.
However, as physical devices are becoming smart, there is an increasing trend toward IT/OT convergence. Wireless connectivity has provided administrators in charge of OT with better monitoring systems and the ability to control physical devices remotely. Advances in machine-to-machine communication and machine learning have created a notable change, enabling the data that physical devices produce to be analyzed in real time to facilitate autonomy, preventive maintenance and improved uptime.
Internet-capable technology has moved into industrial control systems (ICS) and supervisory control and data acquisitions (SCADA) networks. However, operations technology faces the same malware, identity management and access control security challenges that IT faces. The difference is that vulnerabilities in an OT system can leave critical infrastructure at risk of sabotage that can result in life-or-death situations.
Why is operational technology important?
OT is critical for businesses and society at large. At the organizational level, OT is usually tied to core business processes. In a factory, OT is often the tool that makes manufacturing goods possible. Likewise, hospitals depend on OT devices to diagnose patients. For a business or other organization that relies on OT, downtime caused by service outages can severely impair or even halt the organization's core business activities.
This article is part of
What is IT/OT convergence? Everything you need to know
On a broader level, society depends on OT to keep critical infrastructure functioning. For example, in May 2021, a ransomware attack caused the Colonial Pipeline to be shut down. The pipeline, which itself is considered an OT, transports 2.5 million barrels of fuel each day. The shutdown resulted in a major East Coast fuel shortage. This is just one example of how critical some operational technologies can be.
Examples of OT environments
Many industries rely on critical OT infrastructure. Some OT environments include the following:
- Factories. OT controls the machinery used in manufacturing environments to power assembly lines and other processes.
- Power plants. OT systems monitor both the performance and resource use of equipment used in power plants.
- Oil and gas refineries and pipelines. The oil and gas industry requires critical OT infrastructure for upstream, midstream and downstream operations. OT monitors rigs, pumps and other extraction methods within upstream operations. It also performs remote asset management when oil and gas is transported, refined and stored during operations.
- Transportation and aviation facilities. Supply chain management, commuter transport and aviation all rely on OT to keep transport operations running smoothly.
- Water treatment facilities. OT controls processes involved with wastewater treatment.
Examples of OT systems
It's easy to think of operational technology systems as closely associated with industrial equipment and, indeed, they are heavily used on factory floors and power plants. However, they aren't limited to industrial processes. An OT system can be any special purpose, computerized equipment. For example, ATMs, safety systems and traffic lights are all such systems that aren't part of traditional IT infrastructure and are considered OT systems.
Other examples of OT systems include the following:
- Robots. Industrial robotics, such as cobots, are considered OT systems, as are robots that are increasingly used in retail for stocking shelves or mopping floors.
- Medical devices. Certain medical devices, such as magnetic resonance imaging machines and other types of radiology equipment, are considered OT devices.
- Distributed control systems. A DCS is used to control the automation of industrial operations. Controller devices are spread across a factory or plant floor to manage each process individually.
- Human-machine interfaces. HMIs help operators monitor OT environments visually with visual displays of data, a control panel for interaction and typically a notification setup for important alerts.
- ICS. These systems manage and monitor OT networks, including the infrastructure and processes they encompass. They use network-connected hardware and software components.
- Industrial internet of things. IIoT systems connect physical devices and objects to IT networks, letting them collect data and perform predictive maintenance on them. IIoT is a subset of internet of things. IoT and industrial IoT are both relevant to OT environments, but IIoT is specific to industrial environments.
- Programmable logic controllers. A PLC automates various industrial processes and can function in harsh environments, such as extreme heat, cold or vibration.
- Remote terminal units. RTUs are used for data collection and management in OT environments.
- SCADA. These systems capture real-time data from OT, through both software and hardware components, for the purpose of monitoring performance.
- Smart buildings. These facilities are enterprise, commercial and residential buildings equipped with automated IoT technology for various reasons, such as operating efficiency, safety and security.
- Smart transportation. IT networks are used to monitor the performance of various modes of transportation. Connected devices on vehicles can provide data traffic, weather conditions and other factors to create more efficient routes and improve vehicle efficiency.
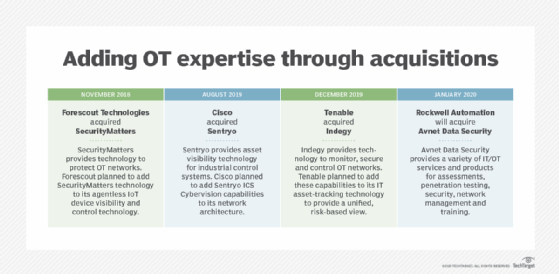
Operational technology challenges
As organizations work to converge IT and OT systems, they must be aware of the inherent challenges of doing so. Many of these challenges stem from the nature of the OT systems being used. They include these four.
Legacy issues
Although some OT systems are modern and complex, it's also common -- particularly in industrial settings -- for OT equipment to be several decades old. When you consider such a device's age and its proprietary design, it can be difficult and costly to connect the device to modern IT systems.
Cybersecurity risks
Another challenge associated with these combinations is that they can introduce OT cybersecurity risks. This is especially true for legacy OT systems. Such systems were likely never intended to be connected to an organization's IT systems. In most cases, they were intended to operate in an isolated environment and didn't need protection against cyberthreats.
Instead, the design process likely focused on making the device as reliable as possible, rather than addressing security threats. Connecting such systems to traditional IT infrastructure can make them vulnerable to cyberattacks, because hackers have a direct communications path through which to access the device. Organizations looking to converge their IT/OT infrastructure must put OT security measures at the forefront.
Knowledge gaps
Another challenge is addressing any knowledge gaps. OT engineers are unlikely to be experts in IT. Similarly, few IT pros have a strong working knowledge of OT systems.
Update and patch management
Finally, OT devices might not fit neatly into an organization's normal IT protocols for software updates and patch management. For example, patch management is often regarded as a critical IT task. However, patches for OT devices might be released on an infrequent basis or not at all.
Even if an OT device manufacturer releases a patch, there will likely be some pushback over installing the patch. At best, installing the patch will cause a service interruption while the device is taken offline and rebooted, which affects the organization's revenue. At worst, the patch can introduce problems into a device that was previously reliable, again, adversely affecting the organization's bottom line.
OT vs. IT: What are the differences?
IT environments have traditionally focused on compute, networking and storage resources. These resources include servers, storage arrays and network switches in the data center or the cloud as well as desktop computers, smart phones and supporting hardware. Enterprise IT is also responsible for managing software at the infrastructure and application levels. This means deploying and maintaining operating systems, IT security controls and monitoring tools, and the applications users rely on to do their jobs.
Conversely, OT encompasses the machines associated with physical processes. These processes can be anything from the manufacturing of goods to medical imaging. Like IT, they revolve around the use of digital systems. However, these systems tend to be proprietary and don't generally fall into the scope of traditional IT assets.
IT/OT convergence
IT/OT convergence involves linking operational technologies to traditional IT systems. Bringing these systems together can make it easier for an organization to meet its compliance mandates, while also breaking down data silos. However, there can also be other, more compelling benefits.
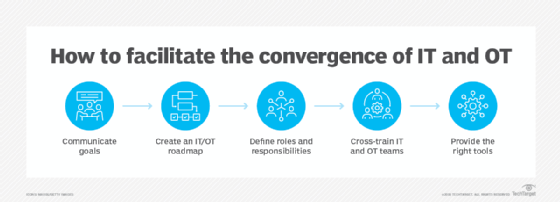
Linking IT systems to OT devices brings intelligence to various business processes. In a factory setting, a converged IT/OT system can analyze the entire manufacturing process to spot inefficiencies. Detecting and eliminating these inefficiencies, ultimately, makes the business more profitable.
Likewise, IT systems can monitor OT equipment use to see when the devices will need maintenance based on their use. This prevents machines from breaking down and saves the business money.
The role of edge computing in IT/OT convergence
Edge computing involves deploying computing devices much closer to sources of data to reduce challenges associated with distributed systems where computing capabilities are further away from the data sources. Edge computing complements OT systems in multiple ways, such as the following:
- Real-time analytics. Edge computing reaches data sources in remote locations and analyzes it from those locations so not as many IT and OT resources are expended.
- Security. Edge computing systems sit in between OT devices and IT networks, using intrusion detection capabilities to identify cyberattacks. They also can reduce the amount of data transmitted between OT and IT devices and networks so that only essential data is sent and secured. This reduces unnecessary opportunities for data breaches and other security incidents.
- Decentralization. Edge computing often moves IT and OT resources to the cloud so there's less reliance on centralized physical infrastructure that can be prone to problems. This results in more reliable systems as well.
- Reduced latency. Data is processed and analyzed closer to the source, reducing the time and resources IT must devote to doing so.
- Lower bandwidth. By minimizing the amount of data that's transferred to only essential data, edge computing reduces the amount of bandwidth that would otherwise be required to transmit large data volumes.
Businesses that rely heavily on OT networks and infrastructure should be aware of five potential OT threats and security challenges and know how to respond when they arise. Learn what these challenges are to be proactive in securing OT.