
kentoh - Fotolia
3 DevSecOps trends to keep an eye on
The future of DevSecOps isn't set, but these trends are shaping its course. Learn what changes -- and risks -- your IT organization should prepare for.
2020 became one of the most monumental years in modern history with consequences that continue to echo across society. However, it was also a period wherein IT played an outsized role in the disruption's mitigation.
Most organizations' work environments look nothing like they did at the beginning of the 2010s, and the ramifications for IT departments and security professionals have been profound. DevSecOps is a movement to improve data and application security that was well underway pre-pandemic, but one that the cascade of crises will both accelerate and reshape.
CIOs and CISOs lay the groundwork for a DevSecOps team by creating a consistent security culture shared across their organizations -- but that culture must also extend to app development teams. To institute DevSecOps requires leadership to consider -- and operate -- IT systems, apps and security as a unified, interconnected system, rather than a collection thereof. Additionally, IT leaders and their teams must adopt systems analysis practices to analyze performance, functionality and security more holistically.
DevSecOps primarily concerns culture and process, not products and technology, but it does create a market for software and services. The limited data available indicates that DevSecOps remains a niche. But it's a fast-growing one with a compound annual growth rate of around 32%, to reach 34% through mid-decade: Spending primarily goes to automation tools that embed security into the development process and reduce the overhead of security-related tasks, such as threat modeling, code audits, vulnerability analysis and application instrumentation.
The sudden shift to work-from-home environments catalyzed equally significant changes in how IT delivers business applications, collaboration services and connectivity. All three have profound implications on security, and hence DevSecOps organizations. We see the following DevSecOps trends leading these changes.
IT looks to the cloud
The two biggest trends in post-pandemic IT combine the sharp increase in cloud services with the disintegration of the enterprise network. Once employees vacated office buildings and IT decamped from data centers, many of the benefits of private infrastructure became handicaps.
As shown in Figure 1, data from Flexera shows that most IT organizations plan to increase -- rather than cut -- spending on SaaS applications and cloud infrastructure by notable margins. Consequently, the response has been widespread abandonment of private data centers. And 55% of surveyed IT organizations said they plan to reduce their data center footprint within two years.
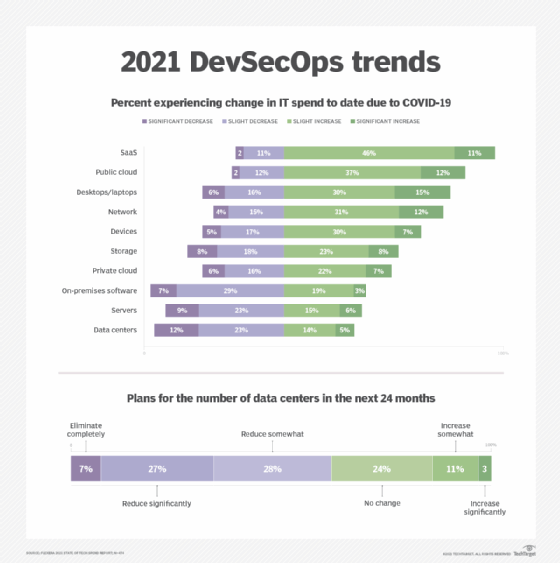
The trend is significant for DevSecOps -- and IT at large -- because once organizations successfully incorporate cloud services like AWS, Microsoft 365, Zoom, Slack and Google Meet into their environments, few will go back to a fully on-premises workforce. A January 2021 PwC survey finds that most employees will likely work remotely more than half the time.
Cloud services are most valuable when developers redesign applications around microservices architectures that use containers, serverless functions and cloud-native services. In turn, cloud-native applications require DevSecOps practices to incorporate cloud development and deployment -- such as infrastructure as code -- services and security tools that can scan cloud environments.
Work moves to the edge
To move to a distributed nature of work demands the same degree of persistence. Employees scattered across myriad broadband and wireless networks often find that internal servers are harder to reach -- and yield slower performance -- than cloud services delivered from hyperscale facilities with massive fiber links to one another and major exchange points. With IT staff also remote, it makes internal systems and cloud service maintenance exercises in remote administration. However, it also breaks security protocols that were designed for internal infrastructure.
Similarly, remote employees who use broadband and wireless networks require new approaches to corporate network reliability and security, including client SD-WAN and secure access service edge.
DevSecOps teams are both administrators and users of these new capabilities. For example, DevSecOps professionals can build zero-trust network access and two-factor authentication into toolchains to strengthen control over source code, CI/CD event triggers and application or cloud resource deployments.
Distributed supply chains, users pose new security threats
The SolarWinds incident in 2020 entailed exploited vulnerabilities in the software supply chain -- namely SolarWinds' internal network and its update server -- to deliver an advanced persistent threat that executed a multi-stage attack on SolarWinds Orion monitoring server installations. FireEye discovered the breach using its own software, but not before the attackers exfiltrated an unknowable amount of sensitive data from thousands of customers, including major U.S. government agencies.
Heterogeneous IT environments that consist of a multitude of equipment and software suppliers, microservice applications and cloud services are more likely to face supply chain attacks. DevSecOps teams must bolster their security architecture, policies and checks to detect and contain such attacks.
Open source project repositories are an insidious form of supply chain compromise, as they encourage contributions from anyone, which can, unfortunately, include attackers using bogus identities. In February 2021, security researcher Alex Birsan documented a tactic exploiting so-called dependency confusion that tricks the software's users to download tainted packages into their projects automatically.
Birsan claims the infected code enabled him to breach 35 large companies, including tech giants like Apple and Microsoft, which paid him bug bounties of $30,000 and $40,000, respectively. Microsoft has since issued a white paper that documents techniques to limit the scopes or namespaces of pull requests and use a secure private repository, such as Azure Artifacts, that adds "protections to prevent public packages from unexpectedly replacing or merging with private packages."
Other trends, risks
Changes in work and IT environments create several other risks and opportunities that DevSecOps teams should address, such as:
- an increase in the number and sophistication of phishing and ransomware attacks that exploit remote employees with weaker security controls on home systems yet have privileged access to company data;
- significant threats from insiders, who are often motivated by money and represent about 35% of all breaches;
- increased regulatory, political and media attention to data privacy and protection, including an increase in the number and severity of fines for law and regulation violations; and
- the proliferation of AI and machine learning technologies throughout the IT management and automation toolchain.
Remote work and other insider threats underscore the need for DevSecOps to embed security processes and control throughout the organization's toolchain. The advanced capabilities in AIOps tools increase the effectiveness and efficiency of automation and security tools significantly, which makes it easier to detect and eliminate security threats before they infect other systems or are deployed into production applications.
The overriding theme for DevSecOps teams is a world with larger attack surfaces, more sophisticated adversaries and greater scrutiny -- but with better tools and services to meet security requirements.








