What is a SYN flood DoS attack?
A SYN flood attack is a type of denial-of-service (DoS) attack on a computer server. This exploit is also known as a half-open attack.
SYN floods are one of several common vulnerabilities that use TCP/IP to overwhelm target systems. SYN flood attacks use a process known as the TCP three-way handshake. As part of the handshake, the client and server exchange messages to establish a communication channel.
The attack involves having a client repeatedly send SYN -- which stands for synchronization -- packets to every port on a server using fake Internet Protocol (IP) addresses. When an attack begins, the targeted server sees the equivalent of multiple attempts to establish communications. In response to each communication attempt, it sends a SYN-ACK -- or synchronization acknowledged -- packet from all the open ports and an RST -- or reset -- packet from all the closed ports.
SYN flood explained: How it exploits the three-way handshake
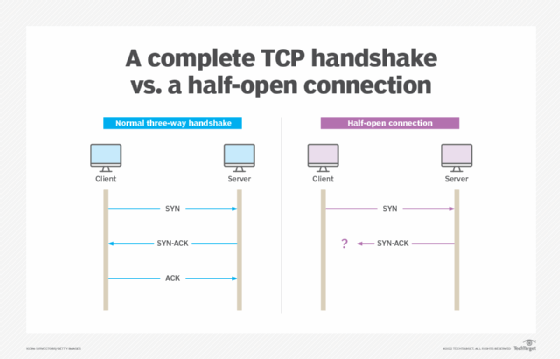
A three-way handshake involves the following steps:
- The client sends a SYN packet to initiate communication with the server.
- The server responds, sending a SYN-ACK packet.
- The client returns a final ACK packet to confirm that the server's SYN-ACK packet was received.
Once those three steps happen, communication can begin between the client and the server. However, in a SYN flood attack, the hostile client does not return an ACK response packet. Instead, the client program sends repeated SYN requests to all the server's ports. A hostile client knows a port is open when the server responds with a SYN-ACK packet.
The hostile client's SYN requests appear valid to the server. However, because the attacker uses fake IP addresses, the server cannot close the connection by sending RST packets to the client.
As a result, the connection stays open, and before a timeout can occur, another SYN packet arrives from the hostile client. This is called a half-open connection. The server becomes so busy with hostile client requests that communication with legitimate traffic is difficult or impossible.
How can a SYN flood attack occur?
The following types of SYN flood attacks can occur:
- Spoofed. In a spoofed attack, the malicious client spoofs the IP address on each SYN packet sent to the server, making it look like the packets are coming from a trusted server. Spoofing makes it hard to trace the packets and mitigate the attack.
- Direct. This type of SYN attack does not use spoofed IP addresses. Instead, the attacker uses one source device with a real IP address to perform the attack. This approach makes it easier to trace where the attack is coming from and shut it down.
- Distributed. A distributed DoS (DDoS) attack uses a botnet that spreads the source of malicious packets over many machines. The sources are real, but the distributed nature of the attack makes it difficult to mitigate. Each device in the botnet can also spoof its IP address, adding to the level of obfuscation. The larger the botnet, the less the need to mask the IP address.
In most cases, a distributed attack is required to take down a host.
How does a SYN flood DoS attack compare to a SYN flood DDoS attack?
SYN flood DoS attacks and SYN flood DDoS attacks differ in the following ways:
- Impact. DoS attacks are generally less severe, as they involve only a single target. DDoS attacks can bring down entire networks.
- Origin. A DoS attack generally originates from a single attacker, while a DDoS attack involves multiple devices.
- Detection. A DoS attack comes from a single IP source, making it easier to detect; it's harder to detect a DDoS attack because it originates from distributed sources.
- Mitigation. DoS attacks are easier to mitigate through rate limiting and SYN cookies. DDoS attacks require more advanced mitigation, such as content delivery network and internet service provider filtering.
How is a SYN flood attack mitigated?
The following techniques can be used to mitigate SYN flood attacks:
- Rate limiting. The number of SYN requests that can be sent to a server at any one time is limited.
- Intrusion detection system. An IDS or firewall can detect and block malicious traffic from a SYN flood attack.
- SYN cookies. This technique assigns each connection request a unique identifier. This approach can block illegitimate requests, though it might also degrade the TCP connection.
- Increasing the backlog queue. A larger backlog queue increases the allowable number of half-opened connections. While the system performance might be affected, DoS attacks are avoided.
- Recycling the oldest half-open connections. When the backlog of connection requests is full, the oldest half-open TCP connections are recycled. This works if legitimate connections can be established faster than malicious half-connections are requested.
Each method has advantages and disadvantages. The best way for an organization to mitigate a TCP SYN flood attack is to configure its systems in accordance with its network security policy and infrastructure.
Why is SYN flood prevention important?
SYN flood prevention is important because these attacks can cause significant damage to networks and systems. SYN floods can cripple servers and networks, making them unavailable to legitimate users, and cause data loss and other damage.
High-profile cyber attacks like the Mirai botnet use SYN flooding to crash servers and inflict damage. Internet of things devices are particularly prone to SYN flooding and DDoS attacks.
Is SYN flooding illegal?
Although threat actors often use this technique, SYN flooding is not always illegal. Security professionals and ethical hackers use SYN flooding as a legitimate way to test or debug a network. The practice of intentionally exploiting a computer system or network to discover and fix flaws is known as penetration testing.
However, when SYN flooding is used to harm another computer system, it is illegal. These attackers can be subject to civil penalties or fines. A DDoS attack that uses SYN flooding is an illegal cybercrime in the U.S. Depending on the context, it could be considered a federal offense under the Computer Fraud and Abuse Act.
SYN flood vs. ping of death attack
At a glance, SYN flood attacks and ping of death (PoD) attacks appear to be similar. Both are DoS attacks -- but beyond that, it's important to note that they exploit different network protocol vulnerabilities in the following ways:
- A SYN flood attack uses TCP; a PoD attack uses the Internet Control Message Protocol.
- A SYN flood attack exploits the TCP handshake using half-open connections; a PoD attack inundates the target system with oversized ping packets.
- A SYN flood attack aims for the TCP backlog queue; a PoD attack wants system memory.
- A SYN flood attack wears its target down by draining resources; a PoD attack crashes the target.
- A SYN flood attack requires that the target respond; a PoD attack doesn't.
DDoS mitigation tools
The following tools are available to help mitigate SYN flood attacks:
- SYN cookies. This technique encodes session information in a SYN-ACK response rather than in memory. SYN cookies are offered in Linux and Cisco devices.
- Stateful firewalls. They filter and limit the rate of incoming SYN packets, dropping excessive requests from suspicious sources. Several vendors offer stateful firewalls, including A10 Networks, F5 Networks, lPFire and Palo Alto Networks.
- Router and load balancer defense. This technology filters SYN flood attacks before they reach the application server. Vendors including Citrix, F5 Networks, HAProxy and Nginx support it.
- TCP Intercept. This feature stops half-open connections from reaching backend servers by intercepting SYN packets and completing the handshake. Vendors including Cisco, Juniper Networks and Palo Alto Networks offer this functionality.
- Intrusion prevention systems. They detect and block SYN flood patterns. Vendors, including Cisco and Suricata, provide IPSes.
- Cloud-based DDos mitigation. This security service absorbs and filters suspicious traffic before network intrusion can occur. Products including Amazon Web Services Shield, Cloudflare, Google Cloud Armor and Microsoft Azure DDoS Protection defend against these attacks.
Providing DDoS protection and deflecting botnets, SYN floods and other exploits require a solid enterprise cybersecurity plan and training. Learn what type of cybersecurity awareness training is needed to maintain excellent cyber hygiene.





