
tashatuvango - Fotolia
Editor's picks: Top cybersecurity articles of 2020
As the year no one could have predicted comes to a close, SearchSecurity takes a 30,000-foot view of the cybersecurity trends and challenges that defined the last 12 months.
Many 2020 cybersecurity predictions were thrown out of orbit when coronavirus cases emerged and COVID-19 was declared a global pandemic by the World Health Organization in March. This year, security teams faced an uphill battle to provide remote access to enterprise networks while simultaneously protecting sensitive data from emerging, pandemic-related cyber attacks in an already volatile threat landscape.
As the year wraps up, some people experiencing "2020 fatigue" may jump at the chance to embrace a new year and never look back. But there are lessons to be learned from the challenges we survived in the last 12 months, whether expected or not.
Below, explore some of the most popular stories among SearchSecurity readers this year that dive deep into data security methods, zero trust, ransomware and the future of the cloud.
Data security and protection top IT priorities
Securing sensitive data, maintaining customer privacy and achieving regulatory compliance are top of mind for organizations in any given year but especially in 2020. The scale of these responsibilities -- most of which are shouldered by IT and infosec teams -- can be enormous.
The importance of data security and protection was reflected in the top cybersecurity articles of 2020. Among the most widely read stories was our ultimate guide to data security. This comprehensive resource explains the importance of securing data and compiles industry best practices, data privacy standards and expert advice on how to develop a data security strategy.
But not all data is created equally. Data classification, the process of determining the sensitivity levels -- and, thus, security protocols -- of data, varies from one organization to another. In this article, network security expert Andrew Froehlich detailed best practices for securing sensitive data at rest, in use and in motion.
Intrinsic to any data security program is encryption. Because scrambling plaintext into ciphertext prevents data from being read or used by malicious actors, it is critical for IT leaders to grasp cryptography basics. In this excerpt from Computer Security Fundamentals published by Pearson, author Chuck Easttom covered the fundamentals of symmetric key encryption algorithms to keep sensitive information safe.
CISO strategies reflect rising zero-trust trend
Every security team faced unique challenges this year, depending on factors such as the organization's size, industry, IT budget and more. Broadly speaking, however, many security leaders have certain -- and persistent -- obstacles in common. In this top cybersecurity article of 2020, security leaders and CISOs discussed their biggest challenges, including ransomware, politics and zero trust.
While the guilty-until-proven-innocent zero-trust philosophy has taken off, it's easier said than done. In practice, rolling out a zero-trust security model requires far more resources than traditional perimeter-based security models. In this article, read a firsthand account of zero-trust implementation from pros who detail their experiences with business interruptions, vendor offerings and more.
Many security leaders view PCI DSS as an outdated framework for protecting payment card transactions. PCI DSS compliance continues to decline as some larger organizations would sooner pay noncompliance penalties than overhaul their entire security program. Learn more about the future of the standard and why some CISOs view zero trust as a PCI DSS alternative.
Sign of the ransomware times
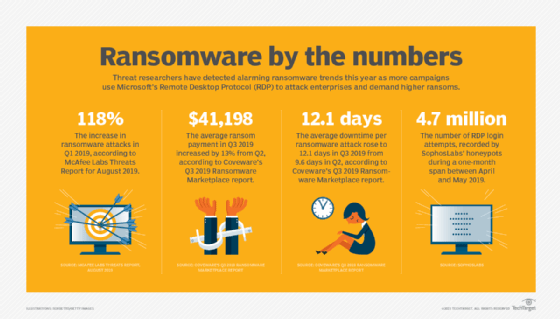
It wouldn't be 2020 without ransomware attacks hitting the headlines in rapid succession. It was a big year for ransomware gangs, which took advantage of the COVID-19 pandemic, heavily targeting healthcare, pharmaceutical and manufacturing industries, as well as educational institutions and government municipalities.
In response to the ransomware spikes, organizations scrambled to bolster data backup and recovery processes, network security and remote access. Examine examples of pandemic-related cyber attacks, and read expert advice on disaster recovery in this comprehensive guide to preventing phishing and ransomware.
Cloud security tools, controls and techniques evolve
Managing and securing cloud environments -- be they private, public, hybrid or multi-cloud -- is a massive undertaking. Many of the top cybersecurity articles of 2020 explored tools and best practices to improve visibility and apply security policies across cloud infrastructure.
Though the concept of a cloud security silver bullet product is wishful thinking, Gartner researchers argued three tools will be essential to secure cloud going forward: cloud access security brokers, cloud security posture management and cloud workload protection platforms. Read up on these tools and how they're changing the cloud landscape.
The most secure data is no data. For this reason, sensitive data must be destroyed when it is no longer needed in order to prevent unauthorized access. When evaluating cloud service providers (CSPs), IT leaders need to question what happens to stored data once it is deleted. In this article, certified SANS Institute instructor Kenneth Hartman compared how data destruction is handled by Azure, AWS and Google Cloud Platform.
Another cloud security challenge top of mind for readers this year was the shared responsibility model. Since CSPs are responsible for securing cloud infrastructure and customers for securing cloud contents, much data security in the cloud is what the customer makes of it. To limit attack and breach opportunities, organizations should conduct penetration testing to identify misconfigurations and flaws. In this excerpt of Hands-On AWS Penetration Testing with Kali Linux published by Packt Publishing, authors Benjamin Caudill and Karl Gilbert provided instructions on how to configure and secure S3 buckets.








