
Vendors: Threat actor taxonomies are confusing but essential
Despite concern about the proliferation of naming taxonomies used to identify threat groups, vendors say they are crucial their understanding and visibility into threat activity.
The number of unique threat actor taxonomies, which results in overlapping names for the same cyber adversaries, may be confusing to clients. But vendors argue such systems are key to maintaining accurate threat tracking and defense procedures.
Adversary attribution lets security vendors link threat actors to malicious activity and identify the motivations and tactics, techniques and procedures behind a cyber attack. Moreover, profiles for advanced persistent threat (APT) groups equip analysts with knowledge to mitigate future threats.
But the propagation of several vendor-specific taxonomies has led to complaints from the infosec community about the growing number of unique names for a single threat group. For example, the Russian cyber espionage group behind the notorious breach of the Democratic National Committee in 2016 is most commonly known as Fancy Bear, which was coined by CrowdStrike, the vendor that investigated the DNC hack.
But the group is also known at APT28 by Mandiant, Strontium by Microsoft, Sofacy by Palo Alto Networks, Iron Twilight by Secureworks and Pawn Storm by Trend Micro. The various codenames can present challenges for security researchers and enterprise defenders trying to track specific threat activity.
But some vendors argue that tracking cybercriminal activity under their company's own individual naming conventions is essential. Because each security vendor observes the threat landscape through a spectacle of their own collected data and analysis, security teams need an idiosyncratic system of labeling nation-state APTs and cybercriminal gangs.
"It's really important to name those actor groups individually because every single company -- Microsoft, Palo Alto Networks, etc. -- has their own viewpoint into that actor activity," said Kyle Wilhoit, director of threat research of Unit 42 at Palo Alto Networks.
Last month Microsoft announced its new threat actor taxonomy system to make adversary groups easier to identify and follow. Some infosec professionals, such as Dmitri Alperovitch, co-founder and former CTO of CrowdStrike, applauded the move. Others noted that Microsoft's new weather-themed taxonomy could lead to confusion.
Great report with procedure level intel. I just wish @Microsoft would fix their threat actor names… "Volt Typhoon affecting Guam" when there is a LITERAL typhoon hitting Guam!!! https://t.co/RoD4u9NVUL
— Jorge Orchilles (@jorgeorchilles) May 25, 2023
While the irritations make sense to Wilhoit, he indicates that the gripe is one that will not be solved without acceptance of the cybersecurity community.
"I understand the industry probably is tired of hearing new names. But the need for that is distinct," he said. "They're only seeing certain aspects that maybe other companies are not seeing, so visibility into those silos of information differs."
Different nomenclatures, same threat groups
Microsoft has become a juggernaut in the cybersecurity industry. The company announced last January that Microsoft Security surpassed $20 billion in revenue. With over 15,000 partners, the company's updated threat actor taxonomy will have an impact across the industry. Analysts and customers will have to align their databases to match the naming scheme.
According to Sherrod DeGrippo, director of threat intelligence strategy at Microsoft, revamping its nomenclature was crucial. The company's visibility into threats is growing with the complexity of the threat landscape, and the new system works to efficiently communicate the expansion of information.
"Microsoft evolved its naming taxonomy to keep up with these changes, unify around a common taxonomy across all threat types, and enable our customers to more easily recognize specific actors and distinguish between them," DeGrippo said.
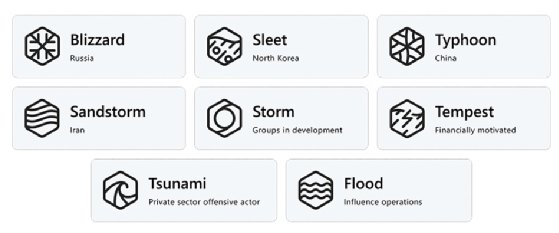
Microsoft's latest blog post employs its new threat group classifications, describing the recent operations of "Mint Sandstorm," an Iranian nation-state actor formerly documented by the company as "Phosphorus." While Microsoft's previous naming catalog assigned groups to chemical elements for identification, similar to cybersecurity vendor Dragos' taxonomy, the company's new system aligns them with the theme of weather.
The threat actors are categorized into five categories, one of them being the attackers' country of origin. For example, Russia is dubbed "Blizzard," represented by a snowflake symbol.
"The purpose behind this new naming method is to bring better context to our customers and security researchers who are already confronted with an overwhelming amount of threat intelligence data," DeGrippo said.
Like Microsoft, Secureworks' Counter Threat Unit (CTU) labels threat actor groups based upon their associated nation-state to provide customers with a greater background on threat groups. In the company's published "Rosetta Stone" of threat profiles, threat group names begin with a metal assigned to their associated nation-state.
Don Smith, vice president of threat intelligence at Secureworks, said that although patterns can be shared among different groups, providing the origin of an attack can give insight on a state's innate geopolitical motivations.
"There's various forms of espionage coming out of China supporting both military objectives and several other objectives," Smith said. "Human rights organizations are a constant target, so it helps you to get a feel for the threat actor."
Categorizing threat groups according to their nation-state of loyalty is where some taxonomies differ. Palo Alto Network's Unit 42 Threat Unit refurbished their naming policy last year with constellations that denote the motivations of the attackers.
According to Wilhoit, researchers at the company focus on threat actors' tracking techniques, tactics and procedures for defense efficiency as well as what provides value to customers.
"What they care about is, 'What is actionable? What can they defend against?'" Wilhoit said. "'What can they stop based on the activity that we're presenting?' That's where we focus our time so we can better protect customers and non-customers alike."
Furthermore, threat analysts amalgamate an immense volume of clustered data every day. Tracking the source of the threat activity may be difficult to confidently pinpoint as researchers sift through the information. It can also be a challenge to attribute familiar activity to a known APT or to assign that activity to a new splinter group. Vendors may have differing views depending on their respective threat intelligence.
"It's oftentimes very difficult to tell where that activity is originating from," Wilhoit said.
Some security vendors dub threat groups according to countries of allegiance, while others generate names based on the intentions behind an attack. The various names and categorizations are derived from the separate lenses through which cyber defenders view the threat landscape.
Members of the infosec community have several taxonomies to keep track of, but vendors emphasize their systems have been made to disseminate accurate information. Despite some of the recent changes and overhauls to improve the clarity, infosec professionals shouldn't expect to see consolidation or a unified system any time soon.
"We're not creating these threat group names because we're trying to make life complicated for defenders. We're doing it in good faith," Smith said. "We're continually trying to deconflict and make sure that we share the understanding, but there will inevitably be differences."








