
Sergey Galushko - Fotolia
Zero-trust initiatives rely on incremental security improvements
Despite implementation challenges, enterprise security leaders see zero trust as the security model of the future and are moving forward with adoption plans.
How can IT know, without a doubt, the identity of those individuals and devices connecting to the enterprise network?
This was the critical question Raj Chandrasekar, COO at Consilio, an e-discovery firm based in Washington, D.C., posed before beginning a zero-trust initiative and implementation project.
"We want to be sure we know who's connecting from a people standpoint and from a device standpoint, and we want to make sure the applications are trustworthy and that only the right people have the right access to the right data at the right time," he said.
The best way to do that, Chandrasekar told his company, is a zero-trust security model.
Chandrasekar, who oversees Consilio's security operations, kicked off the zero-trust project in late 2017. In the months since, he and his security team have implemented measures -- among them multifactor authentication (MFA) and, soon, token-based authentication and biometrics -- designed to move the company toward an environment where no connection is trusted until it's verified.
"It's an incremental build on what we had," Chandrasekar said of his zero-trust implementation strategy. "We don't see a particular endpoint. It's a journey, and it will evolve as newer technologies and newer tools come into play."
Consilio's approach to zero trust mirrors the tack taken by many other organizations, according to surveys and security experts. Both indicated that more CISOs are adding processes and tools to move their security programs away from those heavily reliant on traditional perimeter defenses to models capable of defending data and systems that enable business to be conducted from anywhere.
"There's no perimeter to protect anymore, so you have to protect these smaller pieces of data wherever they might be, whether that data is at rest or being transmitted," said Kory Patrick, risk and security practice leader at TEKsystems Inc. "And you have to ensure that only the right people, services or partners have access to the right information."
Zero-trust initiatives on the rise
Research found a growing number of CISOs pursuing zero trust.
Consider, for example, the findings published in "The State of Zero Trust Security in Global Organizations: Identity and access management maturity in 2020" from Okta, an identity and access management vendor based in San Francisco. Its survey of 500 security leaders found the number of North American organizations that either have or plan to have a zero-trust initiative in the next 12 to 18 months had almost tripled in the past year. Geographically, 60% of organizations in North America and 40% globally were already working on zero-trust projects.
The events of 2020 have spurred adoption even further.
In a July 2020 poll by Deloitte of nearly 600 organizations that either already implemented zero trust or had plans to do so, 37% of respondents said COVID-19 accelerated their plans. Some 35% said the pandemic did not affect the pace of their zero-trust programs, while only 18% indicated the pandemic slowed their work in this area.
Top reasons for implementing zero trust included the model's ability to manage risks associated with remote work and insider threats, third-party risk and cloud risk, the study found.
Top challenges included finding appropriately skilled professionals, funding, not knowing how to get started, and the difficulties in differentiating among technologies and vendors in the market.
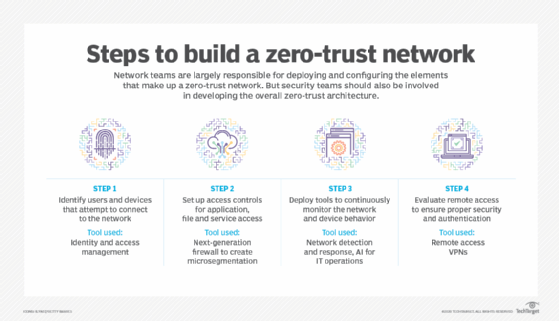
Incremental steps to full zero trust
Despite such obstacles, security experts said they continue to see a majority of organizations moving ahead with zero trust, motivated by both the expectation that the model offers better security and its flexibility that enables companies to make incremental steps forward.
"For most organizations, zero trust is an aspiration, not an absolute," Patrick said.
The concept of zero trust dates back to 2009 when Forrester analyst John Kindervag declared that trust was a vulnerability for organizations and, as a consequence, security should be designed with that in mind. The resulting "never trust, always verify" mindset emerged as the central tenet of the zero-trust framework.
The model upended the longstanding security strategy that focused on perimeter defenses, which were becoming more vulnerable as cloud computing, mobile access and other technologies gained traction.
Zero trust's adoption was further helped by its underlying framework; companies don't have to scrap their existing security foundation. Instead, new processes and tools can be layered in, according to Curt Dalton, managing director and global leader for the security and privacy practice at Protiviti, a consulting firm based in Menlo Park, Calif.
"It's not a solution you can buy; it's a principle. It's about applying context to make risk-based decisions about access," he said.
Many organizations are thinking about how to implement zero-trust principles and apply them more broadly through their enterprise, Dalton said. These organizations typically use a mix of technologies -- among them MFA, behavioral analytics, cloud access security brokers and microsegmentation -- to create an environment ruled by the principle of least privilege.
Yet, foundational challenges remain, Dalton said -- among them data mapping and classification. Companies must also implement adequate identity and access management programs that no longer rely on such technology staples as firewalls, passwords and other older security tools.
Although many organizations are still fine-tuning their zero-trust initiatives, Patrick said he has seen plenty of progress this year and expects that momentum to continue.
"Most companies might not get to a pure zero-trust environment," he added, "but it should be a goal you continue to move toward."







