
makspogonii - Fotolia
Gartner: Privileged access management a must in 2020
Gartner's 2020 Security & Risk Management Summit focused on the importance of privileged access management to cybersecurity as threat actors increasingly target admin credentials.
Based on recent threat activity, privileged accounts, not corporate data, might be the most valuable items within enterprise networks.
Several sessions at Gartner's 2020 Security & Risk Management Summit this week focused on the importance of privileged access management to cybersecurity, and how threat actors have increasingly focused efforts to hijack or obtain privileged accounts. In a Monday session titled "Outlook for Identity and Access Management," Gartner senior research director David Mahdi discussed what a successful identity and access management (IAM) program looks like in 2020, as well as the growing importance of privileged access management and other topics.
Mahdi's presentation discussed the concept of speed versus accuracy in a crisis situation; when immediately responding to a crisis, speed of response to "stop the bleeding" is more important than accuracy at the moment. When the crisis moves from "respond" to "recover" and "renew," then it's important to start thinking about how a company can get back up on its feet and how it can build a more effective cybersecurity foundation for the future.
Good IAM, Mahdi said, is like a good pit crew that balances the importance of getting a racer back on the track quickly (speed) with the importance of making sure a wheel doesn't come off mid-race (accuracy). To give an organization "speed for survival," Mahdi recommended prioritizing the enablement of secure remote access, federated SSO and multifactor authentication (MFA) and both fast and "good enough" IAM and customer IAM or CIAM. And then to maintain accuracy, an organization should focus on account takeover protection, fraud detection, privileged access management and converged, cheaper SaaS-delivered IAM.
"If you aren't using privileged access management tools, technology, people and process where you have this embedded in the fabric of your organization, now's the time to do it. Why? Bad guys are going after privileged users. Privileged users have access to your sensitive data, and they have access to the keys to your kingdom. And that's what you really want to protect," Mahdi said.
In another Monday presentation that touched on privileged access management, titled "Deconstructing the Twitter Attack -- The Role of Privileged Accounts," CyberArk principal solutions engineer Matt Tarr discussed the social engineering attack against Twitter from this summer that resulted in approximately $121,000 in bitcoin being scammed from users. He argued "basic user security training" and privileged access management could have slowed or stopped the events from unfolding.
"This attack highlights the dangers of unsecured privileged access. It should remind us how quickly any credential or identity can become privileged under certain conditions. If not properly secured, external attackers and malicious insiders alike can use them to unlock critical assets, whether that's with a domain admin or a simple support account that can make changes with a Twitter profile," he said.
Tarr noted the infamous attack was not necessarily sophisticated either.
"Originally thought to be the work of experienced nation-state attackers, it now appears the social engineering-initiated attack was conducted by a relatively unsophisticated group of hackers motivated by financial gain and/or cool screen names," he said. "Yup, screen names."
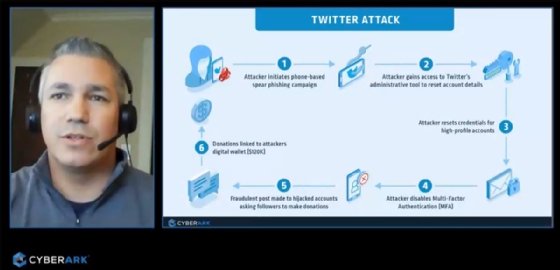
Tarr said the breach demonstrated that it was easier for the attackers to break into Twitter itself than to break into a Twitter account with MFA enabled. The attack began with a phone-based spear phishing or vishing campaign that targeted specific Twitter employees. Once the attackers obtained employee credentials, they gained access to Twitter's administrative tools and disabled the MFA protection on several high-profile accounts. Because Twitter lacked proper security controls around those admin tools, the attackers were able to abuse them while remaining under the radar. Essentially, Twitter had better account protection for users than it did for its own administrators, he said.
Tarr discussed mitigations against these types of social engineering attacks that may happen in the future. He recommended cybersecurity awareness training for employees, using strong passwords, prioritizing privileged access management and creating a conditional policy that mandates multifactor authentication.
In a Tuesday session, titled "Security Leader's Guide to Privileged Access Management," Gartner research director Felix Gaehtgens said privileged access management is a crucial component of any security program because of the increasingly large scope of IT environments, privileged users, administrative tools, and IAM data such as passwords, encryption keys and certificates. Gaehtgens recommended organizations implement strict controls on privileged access such as limiting the total number of personal privileged accounts, creating more shared accounts and reducing the times and durations during which privileged access is granted.








