
Getty Images/iStockphoto
Researchers uncover vulnerabilities in APC Smart-UPS devices
Researchers with Armis found a trio of vulnerabilities in uninterruptible power supply (UPS) devices from APC that could be remotely exploited by threat actors.
A trio of newly-disclosed security vulnerabilities pose serious threats to power backup devices, including possible physical damage.
Researchers with IoT security company Armis discovered and reported three CVE-listed security flaws, dubbed TLStorm, that include remote code execution in uninterruptible power supply (UPS) boxes made by APC.
The bugs are listed as CVE-2022-22806, CVE-2022-22805 and CVE-2022-0715 and address firmware update, authentication bypass and buffer overflow security flaws. The most serious of the flaws could allow for remote takeover of the device and potentially changing hardware settings to create a physical fire hazard.
While UPS devices generally would not be exposed to the open internet, APC's Smart-UPS devices are uniquely vulnerable because they feature a web-based administration portal. Because of this, the Armis researchers say that the bugs are indeed remotely exploitable and can be used for attacks by remote aggressors.
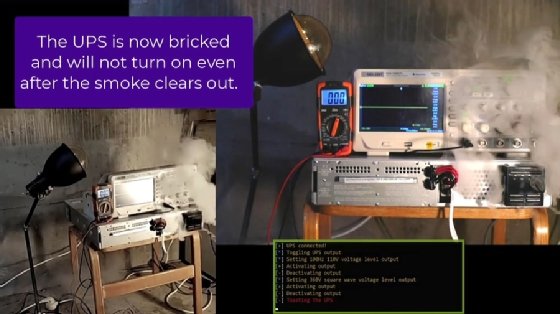
The most serious of the flaws is CVE-2022-0715, a flaw that allows a remote attacker to push firmware updates without authorization. Should the attacker be able to overwrite the firmware on a UPS, they could change critical hardware settings to cause the device to overheat. "Illustrating the cyber-physical effect of the TLStorm attack, Armis researchers were able to damage a Smart-UPS over the network with no user interaction," the TLStorm report said.
Perhaps even more worrying is the ability for the attacker to use the compromised UPS as a foothold to gain further network access. As the UPS boxes are managed over a web interface, the attacker could manipulate the UPS to then contact other systems on the network.
Barak Hadad, head of research at Armis, told SearchSecurity that the risk will depend on how each company has set up its network and the placement of the UPS.
"Since UPS devices are usually responsible for power to mission-critical devices, taking down the UPS also takes down the device that is connected to it and can have severe implications," Hadad explained.
"On top of that, the UPS is often connected to the same internal network as the devices that rely on it, and an attacker can use that to move laterally in the internal network using the UPS as a gateway."
The CVE-2022-22806 and CVE-2022-22805 vulnerabilities, meanwhile, address authentication bypass and buffer overflow vulnerabilities, respectively. In both cases, a specially-crafted TLS packet could allow the attacker to gain remote code execution on the UPS device.
Researchers with Armis noted that the flaws illustrate how UPS boxes, which are generally not seen as a security risk or update priority, can become attack vectors, thanks to the introduction of remote management features.
The team even referenced Hollywood in its report.
"The fact that UPS devices regulate high voltage power, combined with their Internet connectivity makes them a high-value cyber-physical target. In the television series Mr. Robot, bad actors cause an explosion using an APC UPS device," the report said. "However, this is no longer a fictional attack. By exploiting these vulnerabilities in the lab, Armis researchers were able to remotely ignite a Smart-UPS device and make it literally go up in smoke."
Armis said it disclosed the TLStorm vulnerabilities to APC parent company Schneider Electric on Oct. 31, 2021, and worked with the company to create patches for Smart-UPS devices, which are now available. Schneider Electric published a security advisory Tuesday detailing the affected products and security updates.
Armis recommended that administrators connect with Schneider Electric to make sure their UPS systems are updated with the latest firmware. In addition to patching the TLStorm flaws, Armis also urged users to change any default passwords for network management cars in Smart-UPS devices and double-check their network access policies to ward off potential attackers.





