
Askhat - stock.adobe.com
For cyber insurance, some technology leads to higher premiums
Though cyber insurance demand is exceeding supply and companies might receive less coverage with higher premiums, experts say there are ways enterprises can reduce risk.
With increasing demand and dangerous third-party risks, cyber insurance carriers are taking a much harder look at enterprises' security postures -- to the point where they're limiting or denying coverage based on the presence of certain technologies.
Cyber insurance premiums and payouts have risen significantly over the past three years as attack surfaces and adversary techniques have expanded. Insurance carriers struggling to keep pace with the rapid evolution of cybersecurity risks have required customers to comply with a growing list of requirements, such as implementing multifactor authentication (MFA). But the costs of cyber attacks have climbed so sharply that cyber insurance companies are going a step further.
While work to improve security postures continues from both sides, there are specific technologies and software that can affect coverage for enterprises. Payal Chakravarty, head of product at cyber insurance provider Coalition, said rates are based on the root causes that lead to claims. Examples include remote desktop protocol (RDP), which continues to be a problem for SMBs, as well as supply chain issues and third-party partner risks.
While rates have increased, she said enterprises can control the costs by being more intelligent about risk selection regarding the products and technologies in their environment. Coalition rates are based on certain technologies, which means it's not a flat rate increase for every renewal, according to Chakravarty. Renewal rates are determined by a technology-based rating and user behavior, including how they responded to Coalition alerts and whether they fixed the issues.
For example, Chakravarty said the presence of SonicWall products in a customer's network can lead to higher premiums because of the number of vulnerabilities and even zero-day flaws that have been exploited by threat actors recently. Costs can be especially high if an organization fails to patch those vulnerabilities in a timely manner.
"You had SonicWall, [and] we know SonicWall is an issue. We told you to upgrade, and if you aren't doing it, we have to charge you," Chakravarty said.
Flagged products
Nathan Smolenski, head of cyber intelligence strategy at Netskope and former CISO at Corvus Insurance, said that if all of a sudden a whole bunch of claims come in for a software provider, rates for using that product will increase. This was highlighted during the pandemic and a rapid move to remote work that increased the attack surface for adversaries. Threat actors increasingly took advantage of misconfigurations and vulnerabilities in technologies such as VPNs that enabled the work-from-home transition.
The ways that companies configured their employees to work remotely became a huge factor for cyber insurance companies, Smolenski said. Because many companies couldn't afford to buy more VPN licenses, they opened RDP instead.
"The bad guys go, 'I can just log on to Shodan and see all the RDP sessions that are available and try to hack it,' and that's free," he said. "That goes back to configuration, but vulnerabilities were huge too. We saw during the pandemic, it was like every month -- Pulse Secure VPN, SonicWall, a different one every month. And the cyber insurance companies looked at clients and said, 'You have that problem, you need to fix it now.'"
More recent examples Chakravarty provided included Kaseya, which suffered an attack last year that affected managed service providers, as well as NPM packages. In February, threat actors hid more than 1,000 malicious JavaScript packages on the NPM Registry.
"[NPM] had no provisions for MFA, so they had a massive issue, and that had an impact on everyone -- small, medium and large businesses," she said. "Log4j impacts everyone, but from what we've observed, it's mainly VMware Horizon [instances] we saw claims from."
When it comes to products with a lot of vulnerabilities that carry high risk, Ismael Valenzuela, vice president of threat research and intelligence at BlackBerry, cited Microsoft. When looking at the effect of buggy products on cyber insurance coverage, he said it's important to look at the 2021 top exploited vulnerabilities.
"If we see that report from U.S. CERT, we'll see various vendors in the list, but Microsoft's vulnerabilities continue to be prevalent and also the most exploited in data breaches," Valenzuela said.
On the other hand, Andreas Wuchner, field CISO at cybersecurity vendor Panaseer, said it's network designs and configurations that will be flagged more than products, especially when it comes to the cloud. Insurers will raise architectural questions, such as which containerization a company is using and if they implemented microsegmentation, he said, rather than product questions.
In its "2022 Cyber Insurance Market Trends Report," Panaseer surveyed 400 insurers across the globe; respondents cited cloud security as the top factor when assessing security postures because of the growing hybrid workforce.
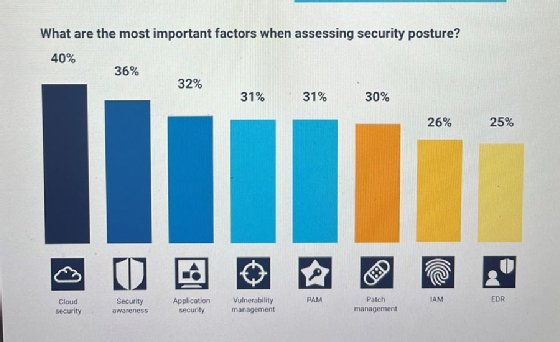
The report also cited patch management as an important factor in assessments. Wuchner said most organizations are struggling to get enough time to patch the increasing influx of common vulnerabilities and exposures, and it doesn't eliminate other attack techniques.
"It would be too easy to blame application or legacy problems," Wuchner said. "There will always be a time when something is unpatched. There's always a chance for a zero-day exploit or the possibility of social engineering ransomware, where people click on something."
Risks extend to everyone
At times it appears enterprises rely too heavily on cyber insurance, rather than improving their security postures or enacting controls. For example, infosec experts say it plays a role in ransomware payments because a company knows it will be reimbursed if it gives in to the demand.
Now, the cyber insurance market is shifting more risks to carriers.
Jennifer Rothstein, cyber insurance and legal expert at BlueVoyant, discussed a new concept of co-insurance where for a ransomware claim, the insured organization might have to contribute out of pocket to any kind of ransom payment or for investigations.
Rothstein also said insurance carriers are still grappling with how to factor in the security of a client's third-party business partners or vendors. Third-party risks pose one of the biggest challenges for underwriting, and questions remain on how to handle it.
"The coverage may or may not include their vendors, so that's something we're trying to figure out," she said.
Another area that's complicated to insure is operational technology (OT) and industrial control systems (ICS) environments. Ian Bramson, global head of industrial cybersecurity for ABS Group, has observed an increased focus in the beginning stages of cyber insurance assessments. Initially, there was just a questionnaire to be filled out. Now, insurers expect senior management to be present to go through the types of questions in much more detail.
However, he also said most OT and ICS customers cannot even answer the first question: What do you need to protect? Another problem is that ICS or OT environments have legacy issues because the systems were designed to function for decades. One example Bramson cited was legacy wind turbines, which can last 50 years, but weren't designed with security and software patching in mind.
"The question is, do I pay a lot of money for my cyber insurance to cover very, very little with lots of exceptions?" he said.
More urgently, OT and ICS environments support critical infrastructures, so Bramson said insurance carriers have to consider more than just a threat actor stealing confidential data.
"Attacking OT can cause cyber-physical events that have much larger impacts." he said. "The challenge there is, they don't have a good way to underwrite it."








