
Getty Images/iStockphoto
Russian cyber attacks on Ukraine driven by government groups
Researchers with Trustwave say the cyber attacks against Ukraine are not the work of enlisted private hacking groups but Russian government intelligence agencies.
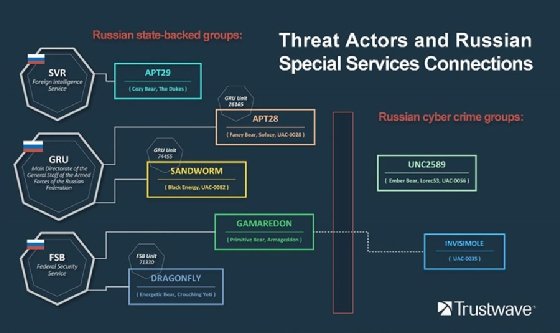
Russian cyber attacks against systems in Ukraine, as part of the former's ongoing invasion attempt, have been almost entirely the work of government-backed intelligence and military agencies.
This is according to a report from security vendor Trustwave, which said that known threat groups from the Russian Federal Security Service (FSB), Foreign Intelligence Service (SVR), and the Main Directorate of the General Staff of the Armed Forces (GRU) are responsible for the vast majority of attacks against both critical industrial infrastructure and data networks in Ukraine. Cyber attacks against public and private sector organizations in Ukraine have increased dramatically since Russia invaded the country in late February.
Researchers from Trustwave's SpiderLabs operation say notorious groups such as APT29, also known as "Fancy Bear," and APT28, or "Cozy Bear," are among the nation-state crews that have been breaking into Ukrainian networks and attempting to disrupt or even destroy vulnerable systems.
Citing both its own research as well as accounts from European government agencies and other cybersecurity vendors like CrowdStrike and SentinelOne, the Trustwave team outlined a bevy of attacks and malware samples that can all be tied back to Kremlin-backed hacking groups. The attacks included a variety of data wipers, DDoS attacks and a multi-layered operation that disrupted satellite internet provider Viasat.
"Reports from Trustwave and other security researchers show that Russian cyber attackers have maintained pressure launching a series of attacks, showing how malware has been used against organizations in Ukraine -- either to destroy or gain control over targeted systems," wrote Trustwave security research manager Pawel Knapczyk in the report.
The report casts doubt on the prospect that the Russian government has been enlisting help from the private hacking sector, as had first been speculated. Rather than trying to enlist or conscript ordinary cybercriminals to do their dirty work, decision-makers in the Kremlin have opted to keep virtually everything in-house and use personnel from its intelligence and military units to carry out attacks.
Karl Sigler, senior security research manager at Trustwave SpiderLabs, told TechTarget Editorial that the decision to use government agencies rather than enlist the aid of Russian cybercrime groups was likely due to the sophistication and preparation of the FSB- and GRU-backed hacking crews.
"They already have those strong connections," Sigler said of the government hackers. "They established connections prior to the conflict, and they have that infrastructure and those channels."
Sigler also notes that the domestic reaction to the conflict -- specifically the internet outages and shifts away from services such as Telegram -- likely made it harder for the government to identify and recruit private cybercrime actors to its cause.
Trustwave's report found the Russian cyber attacks were largely intended to disrupt the normal operation of critical infrastructure, such as energy plants, or create havoc by wiping the data from servers on essential networks. A third category of attacks, meanwhile, focused on intelligence gathering and espionage activity by covertly installing spyware on endpoint systems.
Among the samples collected and analyzed by the Trustwave researchers were a trio of samples employed by the Gamaredon crew, a hacking operation tied to the FSB. Two of those malware samples, HermeticWiper and IsaacWiper, functioned as destructive attacks, while the third was a ransomware infection dubbed HermeticRansom.
Other samples included purpose-built sabotage malware for industrial control systems (ICS), including Industroyer2 from the GRU threat group known as Sandworm and credential-stealing malware known as CredoMap, deployed by the SVR's APT28.
Trustwave found that, apart from the customized ICS malware, nearly all the malware samples in use were previously known hacking tools. The most significant modifications were small changes to the binaries that would allow them to temporarily evade antimalware products.
The aim of the attacks has evolved over the course of the war. Sigler explained that as the Ukraine conflict drags on far longer than the Kremlin anticipated, the tactics of Russian hackers have changed from all-out destruction with wiper tools to information and intelligence gathering.
"We saw that wiper activity at the beginning of the conflict from February to April, but then that approach dried up and we saw a heavier focus on espionage," Sigler said. "At the beginning there was an approach to take things down, but when you have a long, drawn-out conflict like this, information becomes more and more valuable."
Other organizations and vendors have also pointed the finger directly at Russian intelligence and military outfits. During Black Hat USA 2022 last week, Victor Zhora, deputy chairman and chief digital transformation officer of Ukraine's State Service of Special Communications and Information Protection, told reporters the vast majority of cyber attacks against his country were perpetrated by agencies like the GRU. Zhora said that while some cybercriminal groups -- such as the Conti ransomware group, which publicly pledged its support to Russia -- have joined the government's offensive, most appear to be remaining on the sidelines.
Security news editor Rob Wright contributed to this report.





