SolarWinds hackers still active, using new techniques
CrowdStrike has tracked the latest threat activity and novel techniques from the SolarWinds hackers, a Russian state-sponsored group known as Cozy Bear.
Threat actors behind the SolarWinds supply chain attacks actively targeted organizations throughout 2021 and used two new techniques to access its targets, according to CrowdStrike.
The cybersecurity vendor published a blog post Thursday that detailed the latest information about what it dubbed the "StellarParticle" campaign, which relates cyberespionage activity from the Russian state-sponsored threat group Cozy Bear -- the same group that breached breached SolarWinds in 2020. CrowdStrike said the SolarWinds hackers remained active in 2021 using familiar tactics as well as new techniques.
The blog delved into the techniques that enabled the actors to "stay undetected for months -- and in some cases, years." Two novel techniques were highlighted in the campaign that affected multiple organizations: browser cookie theft and Microsoft service principal manipulation.
After examining StellarParticle-related investigations, the security vendor determined that threat actors had a significant knowledge of Windows and Linux OSes, as well as Microsoft Azure, Office 365 and Active Directory. CrowdStrike also found a majority of adversary action observed in the investigations originated from hacking into a victim's O365 environment.
That opened an array of questions, which led to the discovery of credential hopping "where the threat actor leveraged different credentials for each step while moving laterally through the victim's network." CrowdStrike noted it's not necessarily a tactic unique to this campaign, but it does "indicate a more advanced threat actor and may go unnoticed by a victim."
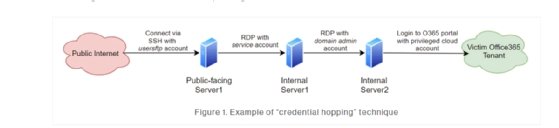
New techniques
While credential hopping may not be new, it raised the question of how the threat actor averted the multifactor authentication (MFA) protocols, which CrowdStrike said it had enabled for every O365 user account at each victim organization it investigated.
Many organizations have embraced MFA to improve account security; however, the StellarParticle campaign reveals its weaknesses and the danger of hackers gaining admin access. Threat actors bypassed MFA, even though it was required to access cloud resources from all locations, including on premise, by stealing Chrome browser cookies. This was accomplished by using the admin access hackers already had to log into other users' systems via Server Message Block protocol and then copying their Chrome browser data.
"The cookies were then added to a new session using a 'Cookie Editor' Chrome extension that the threat actor installed on victim systems and removed after using," according to the blog post.
Even changing passwords did not resolve the issue. CrowdStrike noted that in some cases, the "threat actor was able to quickly return to the environment and essentially pick up where they left off, even though the organization had performed an enterprise-wide password reset." In some of those cases, admin users had reset using a previously used password, which is not usually allowed by the system. Normally, CrowdStrike said Active Directory (AD) requires users to enter a password different from the previous five passwords.
"Unfortunately, this check only applies when a user is changing their password via the 'password change' method -- but if a 'password reset' is performed (changing the password without knowing the previous password), this check is bypassed for an administrative user or a Windows account that has Reset Password permission on a user's account object," the blog authors wrote.
The second novel technique detailed in the blog highlighted yet again the risk of hackers who gain admin control. In this case, the SolarWinds hackers were able to gain access and control to critical applications, including AD. This was done by manipulating Microsoft service principals and application hijacking. After establishing admin accounts, threat actors were able to create their own service principals in Windows or Azure. The new service principals granted company admin privileges, according to the blog.
"From there, the threat actor added a credential to this Service Principal so that they could access the Service Principal directly, without use of an O365 user account," the blog authors wrote.
Though the SolarWinds hackers already had O365 access through a compromised admin account, they created a service principal for O365 because it can be used as another form of persistence and reconnaissance for reading email, CrowdStrike told SearchSecurity. The blog post provided another example of how it was used. Actors abused the mail.read service principal, which enabled them to read emails of several different users in the company's environment.
Even more alarming than the crucial access gained by SolarWinds hackers during the StellarParticle campaigns was their dwell time, which CrowdStrike said spanned years.
"At one victim, CrowdStrike identified multiple instances of domain credential theft months apart, each time with a different credential theft technique," the blog authors wrote.
CrowdStrike also noted the threat actors had targeted corporate wikis in several attacks. "Across multiple StellarParticle investigations, CrowdStrike identified unique reconnaissance activities performed by the threat actor: access of victims' internal knowledge repositories," the blog post authors wrote. "Wikis are commonly used across industries to facilitate knowledge sharing and as a source of reference for a variety of topics."
While the SolarWinds hackers successfully bypassed MFA in several cases, CrowdStrike recommended organizations enable MFA for wikis and internal information repositories. The cybersecurity vendor also recommended organizations enable detailed, centralized logging and store the logs for at least 180 days.







