
Flavijus Piliponis â stock.ado
Cisco Talos traps new Lazarus Group RAT
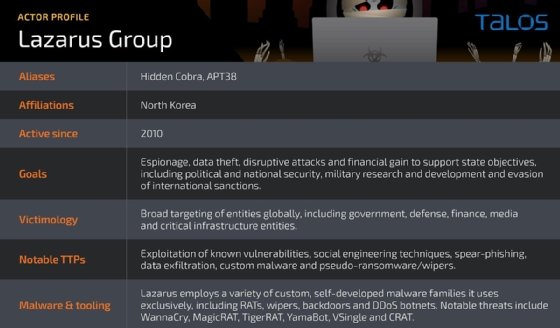
The North Korean-backed Lazarus Group has deployed a new type of remote access Trojan that has already been turned against foreign government networks and private energy companies.
North Korea's Lazarus Group has begun using a new class of remote takeover tools in its efforts to steal data from foreign targets.
Researchers with Cisco Talos uncovered a new malware they have dubbed "MagicRAT." The remote access Trojan has been spotted running through known Lazarus servers and domains and has been targeted against networks and systems in the U.S., Canada and Japan.
According to a two-part report from Cisco Talos researchers Jung soo An, Asheer Malhotra and Vitor Ventura, MagicRAT is a new addition to the Lazarus Group arsenal, being deployed alongside previously known malware packages, including VSingle and Yamabot. All three malware tools are being delivered via a targeted campaign that starts with exploitation of the Log4j vulnerability in VMware Horizon.
As its name would suggest, MagicRAT serves as the remote access portion of the malware payload, allowing the attackers to break into vulnerable servers and set up user accounts for easy access. This eventually leads to the theft of sensitive data and account credentials that Lazarus can use for further attacks and cyber espionage campaigns. While the functions of MagicRAT are nothing new, the research team was surprised at the method used to craft it. Rather than going with a more well-known developer platform, the creators of MagicRAT built with Qt, a relatively obscure framework primarily used to craft graphical interfaces.
By using Qt, the Lazarus crew possibly tried make it harder for security researchers and network defenders to develop easy methods for detecting the deployment of the malware, according to the first part of the Cisco Talos report.
The Talos researchers told TechTarget Editorial that while MagicRAT might not be more complex than other tools, the use of Qt shows that the crew is skilled and dedicated enough to create a new RAT from scratch without much documentation or experience.
"Even though the major purpose of the Qt Framework is the development of graphical user interfaces, the malware authors have only used the network and settings component, simplifying its usage," the team explained. "However, the usage of these components significantly increases the analysis complexity due to its asynchronous characteristics."
In the second part of the report, Cisco Talos detailed a Lazarus Group campaign that used multiple RATs, including MagicRAT, between February and July of this year.
"In this campaign, Lazarus was primarily targeting energy companies in Canada, the U.S. and Japan," the blog post said. "The main goal of these attacks was likely to establish long-term access into victim networks to conduct espionage operations in support of North Korean government objectives."
TigerRAT tags along with update
While MagicRAT made its debut, another previously known RAT tool from Lazarus Group was rolled out with new updates.
TigerRAT, which has been tracked in the wild for around a year now, was found to be using a function known as USB dump. The new capability lets the malware search connected drives and directories on the infected system for specific file extensions and then pack those files up for exfiltration back to attacker-owned systems.
Additionally, the new version of TigerRAT hinted at the coming deployment of webcam-capturing capabilities, as dormant bits of skeleton code for the function were found within the malware. At the same time, TigerRAT's developers turned off support for port forwarding.
"While Lazarus introduced new functionalities in TigerRAT this year, the adversary also removed some existing RAT capabilities," the researchers said. "We have observed Lazarus make such changes to their implants frequently since they started creating bespoke implants."








