
Check Point classifies Azov as wiper, not ransomware
While Azov was initially considered ransomware, Check Point researchers warned the polymorphic malware is designed to inflict maximum damage to targeted systems.
Azov ransomware is actually a data wiper designed to "inflict impeccable damage," according to new research.
Check Point Software Technologies researchers analyzed thousands of Azov samples uploaded to VirusTotal and discovered the malware was crafted with more advanced techniques than initially thought. Jiri Vinopal, threat researcher at Check Point, published the findings in a blog post Monday, which showed an intermittent wiping tactic, manually crafted assembly and the injection of payloads into executables to create backdoors.
While Azov is disguised as ransomware, Check Point determined that the malware is a wiper intended for maximum data destruction. There were no signs of data exfiltration, network activity or monetary motive as with traditional ransomware groups.
"The only thing we can say with certainty, and what has been confirmed by all this analysis, is that Azov is an advanced malware designed to destroy the compromised system," Vinopal wrote in the blog.
Other factors that make the malware different from traditional ransomware include its ability to modify specific 64-bit executables on victims' systems to execute the malicious code. Vinopal said such modifications are achieved through the use of polymorphic code that bypasses static signature detections, which he said "the average malware author would not have bothered with."
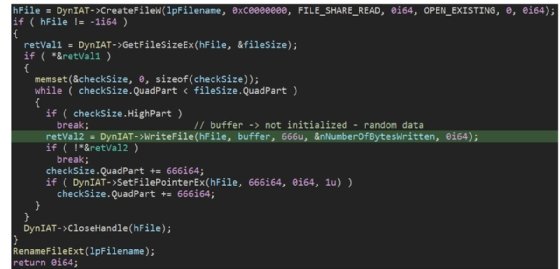
The most significant aspect of Azov is the data wiping technique, which uses a trigger time set to overwrite files.
"A block of 666 bytes is overwritten with random noise, then an identically-sized block is left intact, then a block is overwritten again, and so on -- until the hard limit of 4GB is reached, at which point all further data is left intact," Vinopal wrote.
Eli Smadja, head of research at Check Point, told TechTarget Editorial that the tactic is very useful in rendering data unrecoverable quickly.
"The downside is that it leaves chunks of data intact, allowing the target to restore some original data -- for example, from text files," Smadja said.
Another upside for targets is how the encryption and decryption algorithm -- used during the unpacking and backdooring stages of the attack -- remains consistent and can be used for Azov detection, Vinopal noted in the blog.
While Smadja said the attacks are spread across many geographic regions with no particular targeting, thousands of new samples are uploaded to VirusTotal every day from all over the world.
"This aggressive polymorphic infection of victim executables has led to a deluge of publicly available files infected with Azov," Vinopal wrote.
While analyzing the abundance of samples on VirusTotal -- 17,000 as of November -- researchers noticed there were two versions of Azov. Though functionality was relatively the same for both, the ransom notes differed. In the newer version, the threat actor claimed to be a Polish security expert.
In lieu of a bitcoin ransom demand present in most ransomware attacks, the threat actor pleaded for help for Ukraine and wrongly directed the victim to the Twitter handles of security researchers and infosec reporters to recover the encrypted files. Ukrainian organizations have been hit with data wipers since the onset of Russia's invasion of the country earlier this year.
Check Point said the motive for Azov remains unclear, though Vinopal said it was clear that none of the people mentioned in the latest ransom note had any involvement with the wiper.
"The number of already detected Azov-related samples is so large that if there was ever an original target, it has long since been lost in the noise of indiscriminate infections," the blog post read.







