12 common types of malware attacks and how to prevent them
More than one billion active malware programs exist worldwide. Is your organization prepared to prevent these 12 types of malware attacks?
Malware is one of the biggest security threats enterprises face. An estimated 6.5 billion infections will plague enterprises in 2025, according to penetration services firm DeepStrike -- up from the approximately 6.2 billion infections that struck in 2024.
When it comes to malware, prevention is key. To properly prevent an attack, it is critical to first understand what malware is and its most common types.
The word malware is a portmanteau of malicious software. It is any program designed to intentionally harm and infect devices and networks. Attackers use malware to steal data, credentials, identities and resources; to disrupt networks and services; and for revenge, hacktivism and financial gain.
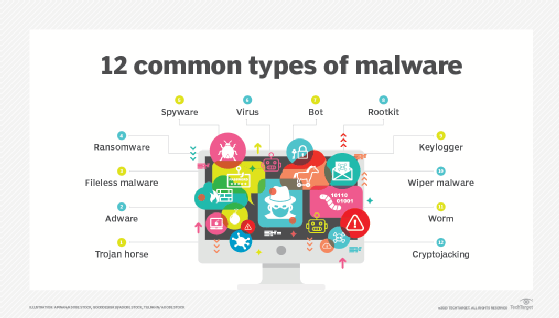
The umbrella term malware encompasses the following subcategories:
- Viruses.
- Worms.
- Ransomware.
- Bots.
- Trojan horses.
- Keyloggers.
- Rootkits.
- Spyware.
- Fileless malware.
- Cryptojacking.
- Wiperware.
- Adware.
Let's explore each type of malware in further detail.
1. Viruses
A computer virus infects devices and replicates itself across systems. Viruses require human intervention to propagate. Once users download the code onto their devices -- often delivered through malicious advertisements or phishing emails -- the virus spreads throughout their systems.
Viruses can modify computer functions and applications; copy, delete and exfiltrate data; encrypt data to perform ransomware attacks; and carry out DDoS attacks.
How to prevent viruses
Install antivirus and antimalware software. Keep the software and definitions up to date, and run regular scans to detect and contain infections.
Virus examples
The Brain virus, developed in 1986, is considered the first MS-DOS PC virus. It spread through infected floppy disks.
The Zeus virus, first detected in 2006, is still used by threat actors today. Attackers use it to create botnets and as a banking Trojan to steal victims' financial data. Zeus's creators released the malware's source code in 2011, enabling threat actors to create updated and more threatening versions of the original virus.
2. Worms
A computer worm self-replicates and infects other computers without human intervention. This malware inserts itself into devices through security vulnerabilities or malicious links or files. Once inside, worms look for networked devices to attack. Worms often go unnoticed by users, usually disguised as legitimate work files.
How to prevent worms
Install OS updates and software patches. Use firewalls to prevent worm intrusions. Run antivirus and antimalware to prevent worms from infecting and propagating across networks.
Worm examples
The Morris worm, released in 1988, is widely acknowledged as the first computer worm distributed across the internet. In less than one day, the worm infected approximately 10% of the 60,000 internet-connected systems across the U.S.
WannaCry, also a form of ransomware, is one of the most well-known worms. The ransomworm took advantage of the EternalBlue vulnerability in outdated versions of Windows' Server Message Block protocol. In 2017, the worm spread to 150 countries. The next year, it infected nearly 5 million devices.
3. Ransomware
Ransomware locks and encrypts files or devices, rendering them inaccessible and unusable until victims pay a ransom to attackers, who often threaten to publicly publish or permanently delete the data until payment is received.
Common types of ransomware include the following:
- Locker ransomware. Completely locks users out of their devices.
- Crypto ransomware. Encrypts all or some files on a device.
- Double extortion ransomware. Encrypts and exports users' files. This way, attackers can potentially receive payments from the ransom and/or the selling of the stolen data.
- Triple extortion ransomware. Adds a third layer to a double extortion attack, for example, a DDoS attack, to potentially demand a third payment.
- Ransomware as a service. Also known as RaaS, enables affiliates or customers to rent ransomware. In this subscription model, the ransomware developer receives a percentage of each ransom paid.
How to prevent ransomware
Data backups were long the go-to defense against ransomware. With a proper backup, victims could restore their files from a known-good version. With the rise of extortion ransomware, however, organizations must follow other measures to protect their assets from ransomware, such as deploying antimalware, advanced protection technologies and strong access controls.
Ransomware examples
The 1989 AIDS Trojan was the first known ransomware campaign. Ransomware became prominent in 2013 with the release of CryptoLocker, a crypto ransomware, in 2013. Other well-known ransomware variants include REvil, WannaCry and the DarkSide RaaS, which was used in the Colonial Pipeline attack.
4. Bots
A bot is a computer program that operates as an agent to simulate human activity. In cybersecurity, a malicious bot is a self-replicating malware that spreads itself to other devices, creating a network of bots, or a botnet. Once infected, devices perform automated tasks commanded by the attacker. Botnets are often used in DDoS attacks. They can also conduct keylogging and send phishing emails.
How to prevent bots
Use antimalware, firewalls and web security tools to prevent bot infections. Advise employees to create strong, hard-to-guess passwords and to never click suspicious links.
Bot example
In 2016, the Mirai botnet DDoS attack affected more than 600,000 IoT devices, including routers and IP cameras, and took down dozens of major websites, including Amazon, Netflix and Airbnb.
5. Trojan horses
A Trojan horse is malicious software that appears legitimate to users. Trojans rely on social engineering techniques to invade devices. Once inside a device or network, the Trojan's payload -- malicious code -- is installed to facilitate the exploit. Trojans give attackers backdoor access to a device, perform keylogging, install viruses or worms, and steal data.
Remote access Trojans (RATs) enable attackers to take control of an infected device. Once inside, attackers can use the infected device to infect other devices with the RAT and create a botnet.
How to prevent Trojans
Never click links or download attachments from untrusted sources. Keep software up to date and advise employees to use strong passwords.
Trojan examples
Zeus is a virus turned Trojan that uses man-in-the-browser attacks to steal banking credentials and conduct unauthorized banking transactions.
The Emotet Trojan was first discovered in 2014. Despite a global takedown at the beginning of 2021, attackers have rebuilt Emotet, and threat actors continue to use it to steal victims' financial information.
6. Keyloggers
A keylogger is surveillance technology that monitors keystroke patterns. Threat actors use keyloggers to obtain victims' usernames, passwords and other sensitive data.
Keyloggers are hardware or software. Hardware keyloggers are manually installed on keyboards. After a victim uses the keyboard, the attacker must physically retrieve the device. Software keyloggers do not require physical access. Victims often download them through malicious links or attachments. Software keyloggers record keystrokes and upload the data to the attacker.
How to prevent keyloggers
Use firewalls to detect and prevent the transfer of keystroke data. Require MFA. Password managers can prevent keylogger attacks because users don't need to physically fill in their usernames and passwords, thus preventing a keylogger from recording them.
Keylogger example
The Agent Tesla keylogger first emerged in 2014. The spyware RAT still plagues users; its latest versions not only log keystrokes but also take screenshots of victims' devices.
7. Rootkits
A rootkit is malicious software that enables threat actors to remotely access and control a device. Rootkits facilitate the spread of other types of malware, including ransomware, viruses and keyloggers.
Rootkits often go undetected because once inside a device, they can deactivate antimalware and antivirus software. Rootkits typically infiltrate devices and systems through phishing emails and malicious attachments.
How to prevent rootkits
Use antivirus and antimalware software, and keep all software patched and up to date.
To detect rootkit attacks, analyze network behavior. Set alerts, for example, if a user who routinely logs on at the same time and in the same location every day suddenly logs on at a different time or location.
Rootkit examples
The first rootkit, NTRootkit, appeared in 1999. Hacker Defender, one of the most widely deployed rootkits of the 2000s, was released in 2003.
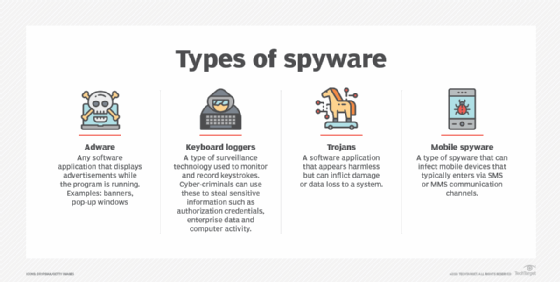
8. Spyware
Spyware is malware that downloads onto a device without the user's knowledge. It steals users' data to sell to advertisers and external users. Spyware can track credentials and obtain bank details and other sensitive data. It infects devices through malicious apps, links, websites and email attachments.
Mobile device spyware, which spreads using SMS and MMS, is particularly damaging because it tracks a user's location and has access to the device's camera and microphone. Adware, keyloggers, Trojans and mobile spyware are all forms of spyware.
How to prevent spyware
Never download files or click links from untrusted senders. Only download known-good software and never click pop-up ads. Use MFA.
Spyware example
Pegasus is a mobile spyware that targets iOS and Android devices. It was first discovered in 2016, at which time it was linked to Israeli technology vendor NSO Group. Apple filed a lawsuit against the vendor in November 2021 for attacking Apple customers and products. Pegasus was also linked to the assassination of Saudi journalist Jamal Khashoggi in 2018.
9. Fileless malware
Fileless malware, unlike traditional malware, does not involve attackers installing code on victims' hard drives. Rather, it uses living-off-the-land (LOTL) techniques to take advantage of legitimate and presumably safe tools -- including PowerShell, Microsoft macros and Windows Management Infrastructure -- to infect a victim's systems. Fileless malware resides in computer memory. Without an executable, it can evade file- and signature-based detection tools, such as antivirus and antimalware.
Note that fileless malware might indeed have files, but the attacks leave no files behind after completing the attack, making attribution difficult.
How to prevent fileless malware
Fileless malware attacks are hard to prevent because they use LOTL techniques. Use MFA and keep systems and software patched and up to date. Use network segmentation.
Fileless malware examples
The first recorded fileless malware attack was the Code Red worm in 2001. It exploited a vulnerability in the Microsoft IIS web server software. Frodo, Emotet and Sorebrect are examples of fileless malware.
10. Cryptojacking
Cryptomining -- the process of verifying transactions within a blockchain -- is highly profitable but requires immense processing power. Miners are rewarded for each blockchain transaction they validate. Malicious cryptomining, known as cryptojacking, enables threat actors to use an infected device's resources -- including electricity and computing power -- to conduct verification. This can lead to performance degradation of the infected device and loss of money due to stolen resources.
How to prevent cryptojacking
Use antimalware and antivirus software. Consider using anticryptojacking browser extensions, which prevent the software from running in web browsers.
Cryptojacking malware examples
The first cryptomining malware strains were detected in mid-2011. Coinhive, a cryptomining service that launched in 2017, at one point controlled 62% of the cryptojacking market and claimed it made $250,000 a month. Coinhive shuttered its services in 2019. Vivin, XMRig Lucifer, WannaMine and RubyMiner are examples of cryptomining malware.
11. Wiperware
Wiper malware, also known as wiperware, is often categorized as a type of ransomware. Like ransomware, it aims to block access to the victim's data. Unlike ransomware, it destroys the data rather than holding it for ransom. The goal of wiperware attacks is not financial gain, but to erase data. Malicious actors often use wiperware to cover their tracks after an attack.
How to prevent wiperware
Use antimalware and antivirus software. Keep systems patched and up to date and create regular backups. Use MFA and zero trust.
Wiperware examples
The first wiperware variants were reported in 2012. The Wiper malware strain was used against Iranian computer systems, and Shamoon wiperware was used against a Saudi oil and gas company. Other wiperware variants include NotPetya, Azov, HermeticWiper and WhisperGate.
12. Adware
Adware is software that displays or downloads unwanted advertisements, typically in the form of banners or pop-ups. It collects web browser history and cookies to target users with specific advertisements.
Not all adware is malicious. Software developers use legitimate adware -- with users' consent -- to offset developer costs. Malicious adware, however, displays ads that might lead to infection if clicked.
Threat actors use vulnerabilities to infect OSes and install malicious adware within preexisting applications. Users might also download applications already corrupted with adware. Adware can also be included in a software bundle when downloading a legitimate application or come pre-installed on a device, also known as bloatware.
How to prevent adware
Use antimalware and antivirus software. Never click links or download attachments from untrusted senders. Read end-user software license agreements before downloading any software.
Adware examples
Fireball, Gator, DollarRevenue and OpenSUpdater are examples of adware.
Key takeaways
As long as malware continues to be successful for attackers, it isn't going anywhere. The following cyber hygiene practices, combined with a strong, regular security awareness training program, are key to mitigating all the aforementioned malware attacks:
- Keep software patched and updated.
- Use firewalls and security software, such as antimalware and antivirus.
- Follow email security best practices.
- Deploy email security gateways.
- Avoid clicking links and downloading attachments.
- Implement strong access control.
- Require MFA.
- Use the principle of least privilege.
- Adopt a zero-trust security strategy.
- Monitor for abnormal or suspicious activity.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.
Isabella Harford previously contributed to writing this article.








