computer worm
What is a computer worm?
A computer worm is a type of malware whose primary function is to self-replicate and infect other computers while remaining active on infected systems.
A computer worm duplicates itself to spread to uninfected computers. It often does this by exploiting parts of an operating system that are automatic and invisible to the user.
Typically, a user only notices a worm when its uncontrolled replication consumes system resources and slows or halts other tasks. A computer worm is not to be confused with WORM, or write once, read many.
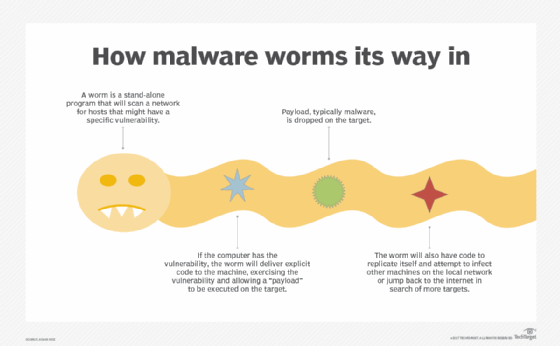
How do computer worms work?
Computer worms often rely on vulnerabilities in networking protocols, such as File Transfer Protocol, to propagate.
After a computer worm loads and begins running on a newly infected system, it will typically follow its prime directive: to remain active on an infected system for as long as possible and spread to as many other vulnerable systems as possible.
For example, the WannaCry ransomware worm exploited a vulnerability in the first version of the Windows Server Message Block (SMBv1) resource sharing protocol.
Once active on a newly infected computer, the WannaCry malware initiates a network search for new potential victims: systems that respond to SMBv1 requests made by the worm. The worm then continues to propagate within a network through these clients.
Malicious attackers can disguise a worm as a nonthreatening resource -- such as a work file or link, which a user clicks on or downloads -- that's only later revealed as a worm. Worms can contain malicious attachments, or payloads, that can delete files or let bad actors remotely control users' computers.
What's the difference between a worm and a virus?
As defined in the "Security of the Internet" report released in 1996 by the CERT Division of the Software Engineering Institute at Carnegie Mellon University, computer worms are "self-replicating programs that spread with no human intervention after they are started."
In contrast, the report noted that computer viruses are also "self-replicating programs, but usually require some action on the part of the user to spread inadvertently to other programs or systems."
What types of computer worms exist?
There are several types of malicious computer worms:
Email worms
Email worms work by creating and sending outbound messages to all the addresses in a user's contact list. The messages include a malicious executable file that infects the new system when the recipient opens it.

Successful email worms usually employ social engineering and phishing techniques to encourage users to open the attached file.
File-sharing worms
File-sharing worms copy themselves into shared folders and spread through peer-to-peer file-sharing networks. Worm authors often disguise these malicious programs as media files.
Stuxnet, one of the most notorious computer worms to date, consists of two components: a worm to propagate malware through USB devices infected with the host file, and malware that targets supervisory control and data acquisition systems.
File-sharing worms often target industrial environments, including power utilities, water supply services and sewage plants.
Cryptoworms
Cryptoworms work by encrypting data on the victim's system. Perpetrators can use this type of worm in ransomware attacks, where they follow up with the victim and demand payment in exchange for a key to decrypt the files.
Internet worms
Some computer worms specifically target popular websites with poor security. If they can infect the site, they can infect a computer accessing the site.
From there, internet worms spread to other devices that the infected computer connects to through the internet and private network connections.
Instant messaging worms
Like email worms, instant messaging worms are masked by attachments or links, which the worm continues to spread to the infected user's contact list. The only difference is that instead of arriving in an email, it comes as an instant message on a chat service.
If the worm hasn't had time to replicate itself onto the computer, the user can change their password on the chat service account to prevent its spread.
How do computer worms spread?
While some computer worms require user action to initially propagate, such as clicking on a link, others can easily spread without user interaction. All that's necessary is for the computer worm to become active on an infected system. Once active, the worm can spread over a network through its internet or local area network.
Before the widespread use of networks, computer worms spread through infected storage media, such as floppy disks, which, when mounted on a system, would infect other storage devices connected to the victim system.
Today, USB drives are a common vector for computer worms, as are internet activities such as email, chat and web surfing.
Computer worm examples
Worms have existed since the beginning of the internet. Several notable cases spread so far that they caused major network and business disruptions.
The Morris worm
The Morris worm was released in 1988 and is widely considered the first computer worm. However, it is better characterized as the first worm to propagate widely on the then-nascent internet.
The Morris worm was the work of Robert Tappan Morris Jr., a Cornell graduate student who was reportedly attempting to enumerate all the systems connected to the internet precursor network, ARPANET.
Targeting vulnerabilities in several different Unix programs, the Morris worm was capable of infecting a system more than once, making it difficult to eradicate before it produced a denial-of-service condition on the infected host. The worm affected as many as 10% of the 60,000 systems believed to be connected to ARPANET.
The ILOVEYOU worm
One of the most damaging computer worms ever was the ILOVEYOU worm. It was launched in 2000 and propagated malware through email attachments that appeared to be text files, scripts run in instant messaging chat sessions and executables renamed with the names of common system files.
ILOVEYOU primarily spread when targeted victims opened an email attachment, and the malware re-sent itself to all the victim's contacts in Microsoft Outlook.
The malware reportedly affected as many as 45 million users after it was released on May 4, 2000, spreading so rapidly that some enterprises, including Ford Motor Company, were forced to shut down their email services temporarily. The worm caused billions of dollars in damages.
Stuxnet
Stuxnet, first identified in 2010, spreads through file-sharing services. Security researchers determined that U.S. and Israeli intelligence agencies created the worm to interfere with Iranian nuclear weapons production.
Stuxnet was introduced via USB drives and took advantage of flaws in the Windows operating system to spread, ultimately causing nuclear centrifuges to malfunction.
WannaCry
WannaCry ransomware uses a worm to infect Windows computers and encrypt files on PC hard drives. It began spreading in May 2017 and affected hundreds of thousands of computers in up to 150 countries worldwide. Targets included large corporations such as FedEx, banks and hospitals. Once the worm locked a PC's files, hackers contacted the owner demanding payment for a key to decrypt the files. However, even after payment, only a few victims were given the key.
Security researchers connected the hack to the Lazarus Group, a nation-state group affiliated with North Korea. While WannaCry caused a significant financial loss for targeted victims, security researcher Marcus Hutchins halted its spread after discovering a kill switch that prevented it from propagating further.
How to prevent computer worm infections
Good cybersecurity hygiene is essential to protect systems from computer worms. The following measures can help prevent the threat of computer worm infections:
- Install operating system updates and software patches.
- Use firewalls to protect systems from malicious software.
- Use antivirus software to prevent malicious software from running.
- Never click on attachments or links in emails or other messaging applications that might expose systems to malicious software.
- Use encryption to protect sensitive data stored on computers, servers and mobile devices.
Although some worms do nothing more than propagate to new victim systems, most worms are associated with computer viruses, rootkits or other malicious software that can cause additional damage and risk.
How to detect a computer worm
Business leaders might struggle to detect the presence of a security incident such as a worm. Signs that indicate a worm might be present include the following symptoms:
- computer performance issues over time, or limited computing bandwidth with no apparent explanation;
- the system freezing or crashing unexpectedly;
- unusual system behavior, including programs that execute or terminate without user interaction;
- unusual sounds, images or messages;
- the sudden appearance of unfamiliar files or icons, or the unexpected disappearance of files or icons;
- warning messages from the operating system or antivirus software; and
- email messages sent to contacts that the user didn't send.
How to remove a computer worm
Removing a computer worm can be difficult. In extreme cases, the system might need to be reformatted, requiring a user to reinstall all software.
When beginning an incident response, security teams should use a known safe computer to download any required updates or programs to an external storage device and install them on the affected machine.
If it is possible to identify the computer worm infecting the system, specific instructions or tools might be available to remove it without having to wipe the system entirely.
Disconnect the system from the internet or any wired or wireless network before attempting to remove the computer worm. Also, remove nonpermanent storage devices, such as a USB or external hard drive, and scan them separately for infection.
Once the system is disconnected, do the following:
- Update all antivirus signatures.
- Scan the computer with the up-to-date antivirus software.
- Use the antivirus software to remove any malware, malicious code and worms it finds, and clean infected files.
- Confirm that the operating system and all applications are up to date and patched.
Organizations must protect their computer systems from worms because these programs can damage systems and compromise sensitive information. Security teams can regularly update antivirus software, use firewalls and encrypt sensitive information to reduce their organizations' worm infection risk. In addition, business leaders can train employees on security best practices to create a human firewall.







