Malware vs. ransomware: What's the difference?
Ransomware is malware, but malware isn't always ransomware. It can be confusing, and the terms are sometimes used interchangeably, but the threats have distinct characteristics.
Confronting the myriad threats in cybersecurity is difficult enough. Confusing terminology sometimes adds to the challenge.
With malware and ransomware, for example, the terms seemingly overlap. Ransomware is malware, after all. But it is only one form of malware. Let's break down the definitions to avoid unnecessary confusion.
What is malware?
Malware is an umbrella term for any malicious software that enables an attacker to perform unauthorized activity on a device or in a system. Threat actors often deliver malware through social engineering attacks, such as phishing, or by taking advantage of unpatched software vulnerabilities.
Once they infect a system with malware, cybercriminals can access information they intend to somehow exploit. Typically, they are motivated by profit, demanding payment in exchange for data they've illegally encrypted, for example, or selling stolen data on the dark web.
How does malware work?
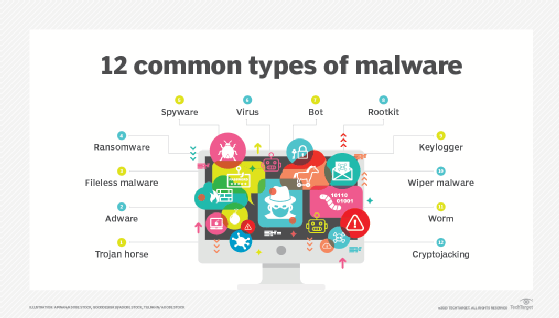
Malware comes in many forms. Let's look at the types and how each accomplishes its goal:
- Adware. Legitimate adware shows advertisements to consenting users while they interact with a given application. Malicious adware aims to trick viewers into downloading other types of malware, such as spyware, to their devices.
- Ransomware. This type of malware holds private digital resources for ransom. Attackers demand payment in exchange for returning access to victims' systems and data.
- Malicious rootkits. A rootkit is software that enables remote administrative control over a device's OS. In the hands of a cybercriminal, a rootkit can steal data or surreptitiously pull a computer into a botnet. Threat actors also use rootkits to deliver other types of malware, such as keyloggers and spyware.
- Scareware. Scareware is a type of malware that tries to frighten victims into falsely believing threat actors have already compromised their devices. Scareware tactics often include pop-up windows or phishing emails that urge users to download -- and often pay for -- corrective security software, which is actually dummy software or malware in disguise. The goal of a scareware attack could be to steal financial credentials, infect devices with additional malware or both.
- Spammers. If attackers seize control of an account or device, they can deploy malicious code that pumps out thousands of spam emails. This type of malware hijacks a victim's system to use it as an email blast platform, or spambot.
- Spyware. Spyware records the activities of unwitting users, such as websites they visit, and information about their computer systems. Spyware that records keystrokes is called a keylogger. It is designed to steal credit card numbers, passwords, bank account numbers and other sensitive data.
- Trojans. Trojan horse malware looks like an innocuous file or program, but it secretly delivers a malicious payload. Ransomware that attackers deliver through phishing emails is also a kind of Trojan, in that the malicious payloads hide within seemingly harmless attachments or links.
- Worms. A worm is malicious software that can self-replicate once inside a system and spread laterally, infecting multiple devices across a network. Unlike a virus, a worm can propagate automatically without requiring additional victims to click links or download files.
What is ransomware?
Ransomware is malware that locks down someone's digital resources and demands payment. It comes in a variety of forms, ranging from crypto ransomware to double extortion ransomware to locker ransomware.
Cybercriminals typically conceal ransomware in an infected attachment or malicious link and deliver it via a phishing attack. Alternatively, they can exploit software vulnerabilities or unsecured Remote Desktop Protocol (RDP) environments. Cybercriminals usually demand ransoms in bitcoin or other cryptocurrencies because they are easier than traditional currency to send and receive anonymously, without interference from law enforcement or banks.
How ransomware works
Once ransomware has successfully infected a system, threat actors scour the system for files containing sensitive data, such as personally identifiable information, financial data and health records. They then might encrypt the data, exfiltrate it or both.
In increasingly common double extortion ransomware cases, attackers both block users' access to their own resources and threaten to publish stolen data online. In a triple extortion ransomware attack, malicious actors add a third threat, such as launching a DDoS attack or extorting the victim's employees, partners or customers.
To decrypt files and regain system access, an organization needs a decryption key, which it can theoretically obtain by paying the ransom. But not all victims who pay ransoms are able to recover from a ransomware attack. In some cases, attackers install secret backdoors in systems so that they can repeatedly attack the same targets. Or attackers simply might not follow through with their side of the deal.
What are the differences between malware and ransomware?
This is somewhat of a trick question, as ransomware is a type of malware.
Some ransomware even qualifies as multiple types of malware. The notorious WannaCry malware, for example, is both ransomware and a worm -- also known as a cryptoworm. Many ransomware programs are also Trojans, with attackers disguising them in apparently innocuous email attachments.
| Malware | Ransomware | |
| Goal | Any malicious code designed to perform a variety of unauthorized actions, including damaging digital resources, stealing data and disrupting IT services. | Malicious code specifically designed to lock victims out of their own systems until they make ransom payments. Can also involve extortion, in which attackers exfiltrate data and threaten to publish it online. |
| Delivery | Delivered in many ways, including via email, USB drives, network worms, Trojans and malicious websites. | Primarily delivered via targeted phishing attacks, RDP attacks or exploited software vulnerabilities. |
| Removal | Some types of malware can be stopped or removed by antivirus software. | Hard to remove once an infection has occurred and the system has been locked or encrypted. |
| Motive | Motives for malware vary, ranging from idle criminal mischief to financial gain to nation-state espionage. | The motive in a ransomware attack is financial gain. As such, ransomware qualifies as serious criminal activity. |
| Technical effects | Range from mild performance degradation on a single device to total destruction of an enterprise network. | Often brings all digital activity to a halt until users pay the ransom, restore the system from backup or rebuild the system from scratch. |
How are malware and ransomware different from a virus?
Virus is a generic term for malware that can damage devices; copy, encrypt, steal and delete data; hijack devices for use in botnets; and more. In a general sense, a virus is a form of malware.
Viruses infect a system when users inadvertently download them, often by clicking malicious links or opening suspicious email attachments. As the name implies, a virus can spread widely into other systems and devices once it gets past cybersecurity defenses.
How can organizations protect against ransomware and other malware?
Because ransomware often spreads through phishing attacks, many experts agree that an organization's most important defense is an educated, cautious user base. Security awareness training is an essential element in a cybersecurity strategy.
Ransomware-specific security awareness training should educate users to never open email attachments or click links from unknown senders, and to regard messages even from known senders with healthy skepticism. If an email from an existing contact seems at all unusual, the recipient should confirm using another communication channel that the other person's account has not been compromised.
Another way businesses can protect themselves from ransomware attacks is to create offline data backups. Reliable backups should ideally enable them to restore their data without paying ransoms. Note that this will not protect against extortion-based ransomware attacks in which bad actors threaten to leak or publicly share stolen data.
Enterprises should also employ defense-in-depth security strategies that include some combination of the following:
- Allowlists/blocklists.
- Antimalware.
- Antivirus.
- Email security gateways.
- Endpoint detection and response.
- Endpoint protection.
- Extended detection and response.
- Firewalls.
- Intrusion detection and prevention.
- Least-privilege access control.
- Managed detection and response.
- Multifactor authentication.
- Network traffic analysis.
- Zero-trust security.
Editor's note: This article was updated in August 2025 to add new information.
Phil Sweeney is an industry editor and writer focused on cybersecurity topics.
Andy Patrizio is a technology journalist with almost 30 years' experience covering Silicon Valley who has worked for a variety of publications on staff or as a freelancer, including Network World, InfoWorld, Business Insider, Ars Technica and InformationWeek.






