scareware
What is scareware?
Scareware is a type of malware tactic used to manipulate victims into downloading or buying potentially malware-infested software. Scareware attacks are used by scammers and cybercriminals to trick users into thinking they have to buy malware disguised as real cybersecurity software.
The intent of scareware is to frighten the computer user into paying for fake software or to further infect a computer system. To frighten users, scareware presents the user with a variety of pop-up security alerts that appear as warnings from actual antivirus companies, frequently claiming that the user's files have been infected. If the tactic works, the victim downloads fake software that, at best, is just bloatware or, at worst, is harmful malware. If it ends up being malware, then the user's personal data is at risk, which could lead to other issues, such as identity theft.
What is the impact on scareware victims?
If a user falls victim to scareware and downloads the fake software, the best-case scenario is that they just wasted money on useless bloatware. Bloatware is unwanted software that is installed on a computer or device. However, this bloatware could make the user susceptible to other attacks if it is not secure. This sort of scareware is just meant to make money off of the initial purchase.
But often the impact is more malicious. Scareware that installs intentionally malicious software on a victim's device cloud can do the following:
- spy on users;
- steal personally identifiable information;
- steal credit card or bank account details;
- deploy more financial fraud or identity theft software;
- lock up the user's computer and demand a ransom, destroying the files if not paid; and
- even offer fake tech support to con more money out of the victim.
How does scareware work?
Scareware typically follows a specific pattern. Pop-ups will start appearing, warning users of dangerous files that have been detected on the user's device. Those pop-ups will try and replicate the logos and layout of legitimate security software. The pop-ups will continue appearing, prompting the user to remove the detected threats or to register for antivirus software.
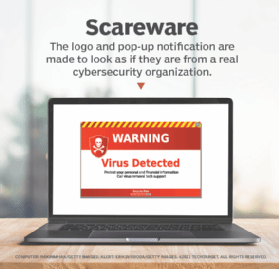
This is where cybercriminals take advantage of social engineering. The concept of social engineering is about manipulating others into taking actions they would not normally take, such as giving up potentially confidential information. In this case, the social engineering tactics use fear to push users into buying potentially malicious software. This can happen on both desktop and mobile platforms.
A link attachment tries to convince the user to pay money for useless bloatware, or to install malware onto their device.
Other ways cybercriminals could scam individuals with scareware, aside from using pop-ups, include using malvertising and phishing emails. Scareware then stays on a user's device for extended periods of time, analyzing their activities.
How do you detect scareware?
There are some common signs potential victims can pick up on to detect if they have been infected by scareware. Some potential signs of scareware include the following:
- Pop-up messages. Real antivirus software will never send messages in a web browser. If a pop-up window notification appears in a browser window, it is not a real notification.
- Malvertising. Real antivirus software will never advertise using similar fear-based notifications that scareware does. The scarier it looks, the more likely it is to be false.
- Inability to access system or files. Users cannot get to real antivirus websites, or error messages and blocked pathways appear when trying to reach other files.
- Upgrade requests. The program tries to manipulate users into upgrading to a better, paid version of their software.
- Decreased performance. Malware can make a computer run slower than usual. A user may experience slowdowns, crashes or freezes.
- Altered settings. Some scareware can alter a computer's internal settings and even change the background wallpaper.
How do you remove scareware?
The easiest way to remove scareware is to use a legitimate antivirus program. These programs run scans and detect threats to remove malware. Users can also remove scareware malware manually.
The process to manually remove scareware is normally straightforward. It involves identifying and uninstalling the malicious download. Scareware typically hides in plain sight as a legitimate antivirus program. To remove this from a Windows PC, perform the following steps:
- Search for "Control Panel" in the Windows search box.
- Select "Programs."
- Right-click on the application, which could be the last antivirus software that was downloaded before the symptoms of scareware started showing up.
- Select "Uninstall."
To remove scareware malware from a Mac, perform the following steps:
- Locate the scareware program in the Applications category of the Finder window.
- Right-click on the program and drag it to the Trash.
- Empty the Trash app.
From here, users can enter safe mode in their computer to install legitimate antivirus software to ensure they do not get another virus before the download.
How can you prevent scareware?
To protect against scareware, computer users should:
- Use trusted security software. Tools such as an antivirus product can scan devices and detect and remove malware such as scareware.
- Use common sense. Do not click on in-browser pop-ups about security. Do not provide personal or financial information to untrusted or unknown websites.
- Use pop-up blockers, firewalls and URL filters. These will help prevent pop-ups from showing up and stop attacks.
- Keep browsers updated. This keeps the browser secure, potentially helping to eliminate any weaknesses to scareware pop-ups.
- Close the browser rather than just the pop-up notification. Some scareware techniques scam users by having a fake Close or X button that installs malware when selected. This is known as clickjacking.
What are examples of scareware?
The classic version of scareware involves fake pop-up notifications that claim the user has multiple infections that need to be removed immediately, although some scareware infections can come from rather unexpected places.
Some past scareware examples include the Office Depot and Support.com Inc. scam. In 2019, Office Depot and Support.com were ordered to pay $35 million in settlements with the Federal Trade Commission after running a tech support scam from 2009 to late 2016. Office Depot had its employees run a fake PC diagnostics check, which enabled the organization to sell unneeded tech repair services.
Learn more about elaborate social engineering attacks and how not to fall victim in this article.
