
Getty Images/iStockphoto
NCC Group: Ransomware attacks increased 41% in November
In addition to a month full of unexpected trends in both threat group activity and targeted sectors, NCC Group warned organizations to be aware of an increase in DDoS attacks.
Ransomware attacks rose 41% last month as groups shifted among the top spots and increasingly leveraged DDoS attacks, according to new research from NCC Group.
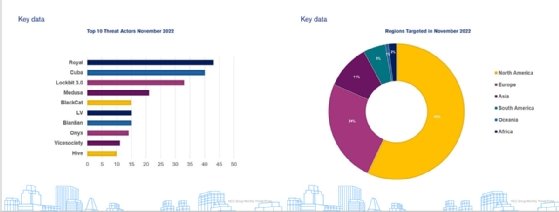
A common thread of NCC Group's November Threat Pulse was a "month full of surprises," particularly related to unexpected shifts in threat actor behavior. The Cuba ransomware gang resurged with its highest number of attacks recorded by NCC Group. Royal replaced LockBit 3.0 as the most active strain -- a first since September of last year.
These factors and more contributed to the significant jump in November attacks, which rose from 188 in October to 265.
"For 2022, this increase represents the most reported incidents in one month since that of April, when there were 289 incidents, and is also the largest month-on-month increase since June-July's marginally larger increase of 47%," NCC Group wrote in the report.
Operators behind Royal ransomware -- a strain that emerged earlier this year, operates without affiliates and utilizes intermittent encryption to evade detection-- surpassed LockBit 3.0 for the number one spot, accounting for 16% of hack and leak incidents last month.
While Cuba ransomware took the second spot, NCC Group described its November activity as "alarming," "uncharacteristic" and "unexpected." Since its emergence on the threat landscape in 2019, Cuba ransomware attacks have fluctuated from zero in a month up to a maximum of seven, which NCC Group observed in January 2022. However, in November, the number of Cuba ransomware attacks rose to a record-breaking 40.
Whether Cuba will remain a permanent fixture in the top three variant rankings remains to be seen.
"We certainly anticipate spikes and fluctuations in threat actor behaviors however, the significant jump observed here may signal a more frequent, higher level of targeting,"
Though LockBit 3.0 remained in the top three and accounted for 12% of November activity, NCC Group noted its attacks were "substantially less" than normally expected. It was the first time since September of 2021 that LockBit 3.0 did not pose the greatest ransomware threat to organizations, according to the report.
In a separate press release, Matt Hull -- global head of threat intelligence at NCC Group -- said the decrease in activity may suggest the group is disbanding.
Healthcare sector leaves top three
In addition to a shift among the top ransomware groups, NCC Group also observed a change in targeted sectors between October and November. Industrials, consumer cyclicals and technology filled the top three spots, with attacks on technology organizations surging a massive 75% last month.
In October, healthcare replaced technology for the third most-targeted sector. However, because healthcare only experienced one less attack in November, NCC Group noted it doesn't mean the sector has become less targeted. Earlier this month, a government alert warned healthcare organizations of an increase in attacks from the Royal ransomware strain.
"Therefore, it is justified to assume that healthcare's burst of targeting in October was simply an anomaly, and technology will return to the top 3 for the foreseeable future, though healthcare may remain an industry of interest to extortive threat actors," the report read.
DDoS attacks also increased last month to over 3,000 -- a trend that continues from October's Threat Pulse. However, the report noted that NCC Group's DDoS data collection has broadened, which may affect an increase in the overall figures.
Hull told TechTarget Editorial that several ransomware groups are using DDoS attacks to further disrupt their victims and pressure them into paying ransoms.
"DDoS is not a new technique, but like other tactics, it continues to evolve, becoming more effective and intensive. It is often used as a distraction technique, but in some cases, it's now being used to leverage larger payouts from victims of ransomware operators," Hull said. "For most organizations, DDoS attacks are a nuisance, causing short periods of downtime. But for some, they can be the straw that breaks the camel's back, because they've already been impacted by ransomware and the theft of sensitive data."
Hull said NCC Group's analysis indicates a rising trend in DDoS attacks.
"Based on the statistics we have this year, the suggestion is that the trend will continue upwards," he said. "But as we well know, the cybercrime landscape is very dynamic -- DDoS could just as easily fall out of favor again, as it has done in the past."






