
Getty Images/iStockphoto
May ransomware activity rises behind 8base, LockBit gangs
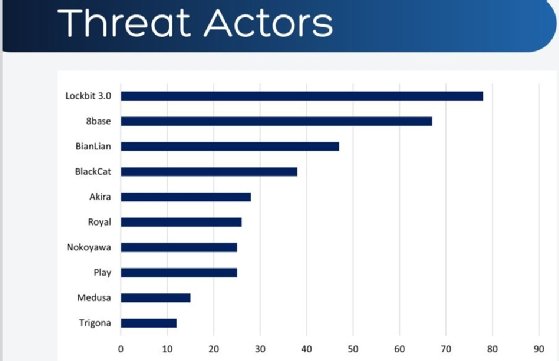
LockBit was the most active group last month, but NCC Group researchers were surprised by 8base, which started listing victims from attacks that occurred beginning in April 2022.
Global ransomware activity escalated last month with a 24% surge compared with April, making it the second-highest number of recorded ransomware attacks so far this year, according to new research by NCC Group.
NCC Group's global threat intelligence team publishes ransomware trends in its monthly report based on public data leak site activity and victim disclosures. Researchers discovered 436 victims in May compared with 352 in April, an increase attributed to the emergence of a new ransomware gang on NCC Group's radar.
Tracked as 8base, the threat group claimed the second-most active position behind LockBit 3.0, collecting a total of 67 victims. While the group isn't new to the threat landscape, as its breaches occurred between April 2022 and May 2023, 8base's public leak site -- which ransomware groups use to pressure victims into paying -- only became active last month.
"The working theory is that they have only recently begun publicizing their victims' data. It's important to note that the data used in the Threat Pulse is based on the date of victim discovery, not the date of initial publication or data breach," NCC Group wrote in the report. "Even when excluding the 8base attacks, May's numbers this year are 56% higher than those in May 2022, and a small 5% higher than April 2023."
So far, each month in 2023 has seen a higher number of victims than its 2022 counterpart, according to NCC Group analysis. Last month, 8base operators contributed to the ongoing trend by carrying out 15% of ransomware attacks recorded.
Like the LockBit ransomware group in May, 8base targeted the industrial sector and leveraged a double extortion technique by stealing and encrypting victims' data. Among 8base's victims, 34% were located in the U.S. and 18% in Brazil, with 52% from the industrial sector.
The report emphasized how 8base must have been actively operating without publicly disclosing its victims for about one year. Typically, ransomware groups breach an organization, give a tight deadline and then increase the pressure to pay by publishing the victim's name along with alleged stolen data on dark web leak sites run by the operators.
For example, NCC Group found that the BianLian ransomware group, which was ranked the third-most active gang in May, offers victims 10 days to pay the required ransom. The report also noted how that group tends to hide its victims' names in posts to extortion sites.
The extended timeline was not the only unique aspect of the 8base threat group.
"It is also interesting that 8base has very specific 'terms of service' with a section focusing on the involvement of any third parties. The terms clearly outline that the involvement of third parties is prohibited," the report said.
NCC Group told TechTarget Editorial that many cybercriminal groups and ransomware operators issue "terms of service" to their victims, but 8base differentiates itself by specifically prohibiting the use of third-party negotiators.
"While NCC Group does not have specific intelligence to support this, there is the possibility that 8base believes professional (third-party) negotiators have greater successes in reducing the potential extortion amount, and the group obviously wants to avoid that," said Matt Hull, global head of threat intelligence at NCC Group, in an email to TechTarget Editorial. "That is not a new concept -- in more 'traditional' criminal enterprise, the individual or group issuing a ransom demand often makes further threats if law enforcement or other intermediaries get involved," he noted.
"While some groups have opted to skip deploying ransomware itself to encrypt data and focus on purely exfiltrating data, the actual use of ransomware has not gone down significantly and is still a widely utilized tool in the cybercriminal arsenal," Hull said.
The fifth-ranked threat group in May, tracked as Akira, also exhibited unusually high activity last month. NCC Group found that attacks by the ransomware group, which claimed the 10th threat group spot in April, increased by 250% last month. In addition to increased activity, its targets also shifted.
While NCC Group did not observe a preferred targeted industry in April, Akira operators hit mainly professional and commercial services in May, followed by the education sector.
"At this point in time, it is difficult to tell whether Akira will continue to increase their activity month on month for the remainder of the year, or if this is temporary momentum," the report read.
Another key contributing factor to May's increased ransomware activity was LockBit 3.0. The ransomware group that was responsible for attacks this year against Managed Care of North America and the Washington County Sheriff's Office maintained its position as the most active threat group in May. Operators claimed 78 victims, with schools, colleges and universities as the second-most targeted industry.
Despite LockBit's top spot last month, May was its second-slowest month activity-wise since the start of 2023. NCC Group determined that the pattern was consistent with the group's fluctuating activity throughout the year. LockBit was most active in February, with 129 out of 240 recorded attacks, and lowest in January, with only 50 out of the 165 attacks in NCC Group's report.
"Regardless of the fluctuation in overall attack numbers, the threat actor is highly likely to continue being relentless in their targeting throughout the remainder of the year," the report said.
The report also highlighted an increase in attacks against the technology sector and the significant risks that poses. Researchers found an alarming 78% attack volume increase between April and May against the sector. Last month, Michigan-based technology company Gentex Corporation disclosed a breach by the Dunghill ransomware gang, and technology distributor ScanSource confirmed that ransomware caused multiday system outages.
"This is a sector which continues to be a focus of attack, given not only the potential to access intellectual property, but also due to single attack vectors which allow criminals who can compromise supply chains to leverage access to multiple organisations," the report read. "This therefore poses a risk of data exfiltration and extortion, making strong security protections a continued priority for businesses within the sector."
Arielle Waldman is a Boston-based reporter covering enterprise security news.





