Nabugu - stock.adobe.com
Mandiant reveals new backdoors used in Barracuda ESG attacks
Further investigations show threat actors were prepared for Barracuda Networks' remediation efforts, including an action notice to replace all compromised devices.
A threat actor connected to China deployed backdoors to hinder remediation efforts during a campaign against vulnerable Barracuda Networks Email Security Gateway appliances that began last year, according to new research by Mandiant.
In May, Barracuda Networks disclosed a zero-day vulnerability, tracked as CVE-2023-2868, in its Email Security Gateway appliance that was exploited in attacks against customers beginning in October 2022. Incident response investigations by Mandiant, CISA and the FBI later attributed the ongoing campaign to a threat actor supporting the Chinese government and determined that all affected ESG devices were to be replaced immediately, as patches released in May were insufficient.
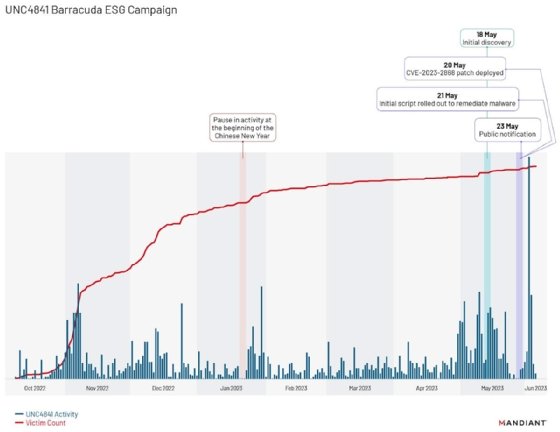
However, Mandiant determined that the group it tracks as UNC4841 anticipated the replacement advisory and other remediation efforts. In a blog post Tuesday, Mandiant researchers highlighted backdoors the attackers used to maintain persistence on targeted organizations. The researchers named the three code families Skipjack, Depthcharge and Foxtrot/Foxglove and noted that they were deployed in case the campaign was compromised, which occurred during the May disclosure.
More notably, the backdoors were part of a "second, previously undisclosed wave" of attacks that began in early June and extended beyond malware variants discovered and disclosed by CISA in late July. Activity observed during the second surge was the highest Mandiant identified across the entire campaign.
"Specifically, UNC4841 deployed new and novel malware designed to maintain presence at a small subset of high priority targets that it compromised either before the patch was released, or shortly following Barracuda's remediation guidance," Mandiant researchers wrote in the blog.
The researchers emphasized the sophistication and adaptability of UNC4841, which was evident by its use of novel malware for high-priority targets. Those targets widely consisted of government entities, which aligns with the cyberespionage attribution.
"Mandiant assesses that, at the time of writing, a limited number of previously impacted victims remain at risk due to this campaign," the vendor wrote.
More backdoors
Mandiant said Skipjack was the most widely deployed backdoor and found that it contained the most variants. It was observed on roughly 5.8% of all compromised ESG appliances and primarily targeted government and technology organizations.
Mandiant first observed the use of Depthcharge, which CISA tracks as Submarine, on May 30. Barracuda initially disclosed the ESG zero-day vulnerability on May 23. On June 6, Barracuda issued an action notice urging customers to replace their devices immediately.
"Mandiant observed UNC4841 rapidly deploy DEPTHCHARGE to select targets following Barracuda's announcement that RMA [return merchandise authorization] was the recommended response action," the blog said. "This capability and its deployment suggests that UNC4841 anticipated and was prepared for remediation efforts with tooling and TTPs [tactics, techniques and procedures] designed to enable them to persist on high value targets."
Researchers noted that victims targeted by Depthcharge were a priority for UNC4841. That included U.S. and foreign government entities as well as the technology sector. Mandiant only observed the deployment of Depthcharge on around 2.64% of compromised ESG appliances. Packaged as a Linux shared object library and pre-loaded into the Barracuda SMTP daemon, Depthcharge was created to disrupt victims' attempts to restore from backups.
The third malware family, known as Foxtrot/Foxglove, was only used against government or government-related organizations that Mandiant said were "high priority targets for the PCR [People's Republic of China]." It was the only malware family that wasn't specifically designed for Barracuda ESG appliances and could be used on other Linux-based devices. Attackers leveraged Foxtrot for lateral movement and credential theft.
Lateral movement to OWA
Mandiant's in-depth analysis of UNC4841's TTPs also shed light on the group's reconnaissance and lateral movement following Barracuda's disclosure of CVE-2023-2868. The investigation revealed that attackers moved laterally to target "mstore," a temporary storage location on ESG devices, to harvest credentials. Some credentials were connected to Outlook Web Access, which was also targeted by a Chinese-nexus actor in separate, recent attacks against Microsoft customers that included U.S. government agencies.
"In multiple instances, Mandiant identified cleartext credentials contained within the contents of messages stored on the ESG that UNC4841 subsequently used to successfully access the account through Outlook Web Access (OWA) on the first attempt," the blog said.
Mandiant assessed that the tactic was used to maintain persistence on compromised victims' mailboxes for information-gathering purposes following Barracuda remediation.
Despite the deployment of backdoors to maintain persistence, the investigation also revealed some good news. Since Barracuda released the patch on May 20, Mandiant said it has not identified evidence of successful exploitation of CVE-2023-2868 resulting in any newly compromised appliances. In addition, only 5% of ESG appliances have been compromised worldwide.
Arielle Waldman is a Boston-based reporter covering enterprise security news.