
Getty Images
How ransomware gangs are engaging -- and using -- the media
New Sophos research shows that ransomware groups are not only attacking technical systems, but taking advantage of information systems as well to pressure victims into paying.
Listen to this article. This audio was generated by AI.
As ransomware gangs continue to market themselves as legitimate businesses complete with customer service representatives, new research from Sophos showed that threat actors are expanding public relations efforts to further pressure victims into paying a ransom.
In a threat report published Wednesday, Sophos X-Ops researchers examined how the rocky relationship between ransomware gangs and the media has evolved as the threat continues to escalate. Ransomware operators leverage the media to publicly spotlight victim organizations amid a rise in brazen data extortion threats. However, operators will also promote their own public relations material by crafting what they call "press releases" and electronic magazines, as well as disputing media attack coverage or inviting reporters for interviews to "control the narrative."
"Media engagement provides ransomware gangs with both tactical and strategic advantages; it allows them to apply pressure to their victims, while also enabling them to shape the narrative, inflate their own notoriety and egos, and further 'mythologize' themselves," Sophos X-Ops wrote in the report.
Sophos observed newer initiatives including dedicated Telegram channels for PR and a FAQ section for journalists posted on ransomware leak sites. However, the security vendor warned that groups' PR tactics will not only increase, but "may grow and evolve."
Ongoing media engagement has put some ransomware actors on track to becoming public figures, Sophos also warned. The threat detection vendor observed that ransomware gangs have devoted more and more time to "managing the media," publicly correcting alleged inaccuracies, encouraging questions and providing interviews.
The report highlighted several ransomware gangs including RansomHouse, Alphv/BlackCat, Karakurt, Vice Society, Snatch and the infamous LockBit gang.
"It may be a way off, but it's not unfeasible that in the future, ransomware groups may have dedicated full-time PR teams: copywriters, spokespeople, even image consultants," Sophos wrote.
Recently, some threat actors have shifted away from ransomware deployment to relying solely on data extortion threats to pressure victim organizations to pay. The evolution relied heavily on ransomware groups' public data leak sites, which list victim organizations next to a payment countdown. Not only does the tactic publicly spotlight victims, but removal suggests the organization paid the demand.
Following the shift away from encryption, ransomware activity skyrocketed. The number of ransomware attacks reached historic highs in 2023, according to some threat reports.
After investigating several ransomware leak sites and underground criminal forums, Sophos X-Ops researchers determined that ransomware gangs know their leak sites are frequented by journalists. The media activity can draw additional public attention to victims, which threat actors leverage to increase pressure on the organizations to pay the ransom.
In other cases, Sophos observed threat actors insulting media publications and individual journalists in response to coverage they deemed inaccurate. One example was the Alphv/BlackCat ransomware gang's rebuttal to coverage on the disruptive MGM Resorts attack in September. The 1,300-word statement criticized several media outlets for reporting incorrect information.
Christopher Budd, director of threat research at Sophos, told TechTarget Editorial that BlackCat's MGM rebuttal inspired the research into ransomware gangs and the media. The statement highlighted an important transition in the ransomware landscape; Budd noticed that attackers are not only operating in the technical sphere, but some are moving into the information space as well.
Budd was impressed by how BlackCat operators structured the write-up, which featured fluent English. "Objectively speaking, from an industry point of view, it was a decent threat research write-up. I'm reading it and I'm like, 'This looks familiar,'" he said.
Regarding accuracy of the ransomware gang posts, Budd said only the attackers and victims will truly know what happened. However, he also said it's certainly possible that there is a degree of accuracy. An important aspect to consider is that ransomware actors are criminals who have a vested interest in not telling the truth.
Analyzing press releases
Whether communications with the media are positive or negative, ransomware gangs' goal is to expand attack coverage to apply pressure on victims to pay the ransom.
Being aware of and leveraging media outlets to accomplish their objective is "in some ways, unique to ransomware gangs," Sophos noted in the report. Operators have shown increased professionalism when it comes to media relations to improve their reputation and appear as a legitimate business. Examples include the press releases and eye-catching branding that decorates public data leak sites, Sophos said.
Increased professionalization and commoditization are two recent developments to emerge on the threat landscape, the report emphasized.
"These factors, and the explosive growth of the ransomware threat, have led to a situation where threat actors, far from shunning the increasingly bright glare of the media spotlight, recognize the potential to reflect and redirect it for their own ends," Sophos wrote. "They can leverage opportunities to directly and indirectly apply pressure to victims; attract potential recruits; increase their own notoriety; manage their public image; and shape the narrative of attacks."
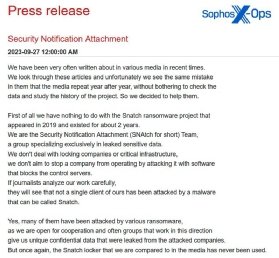
During an investigation, Sophos X-Ops researchers viewed a press release from the Snatch ransomware group in which operators highlighted "mistakes" in various media articles. For example, the press release stated that the group does not encrypt victims' files or attempt to disrupt operations as other ransomware groups do. Sophos revealed that the last line of the press release invited "cooperation and communication" through a Telegram channel.
"Here, the threat actor is arguably inviting a comparison between their own proactive action to 'protect' against the leak (for which they're responsible) and the mishandling of ransomware incidents and sensitive data by some organizations -- thereby aiming to portray itself as more responsible and professional than some of its victims," the report said.
Snatch is not the only ransomware gang to produce so-called press releases. Sophos noted that a handful of ransomware groups use the tactic, including Karakurt, which dedicated a separate page of its site just for its press releases. Public announcements are used to recruit members, detail specific attacks and shame victims.
"In both these latter cases, according to Karakurt, negotiations broke down, and the so-called 'press releases' are in fact thinly-veiled attacks on both organizations in an attempt to pressure them into paying and/or cause reputational damage," the report said.
Ransomware negotiations have become increasingly effective for victim organizations, which are often able to negotiate lower ransom payments. Dark web chatter shows that attackers are becoming frustrated with negotiators, with some ransomware gangs altering their approach to such discussions.
Sophos also emphasized that ransomware groups are becoming public figures, which can complicate matters for reporters. "In the same way, many journalists will recognize the feeling of having qualms about the activities, ethics, and motivations of many public figures, while also knowing that reporting on those figures is in the public interest," the report said.
Following a focus on PR communications, Budd said ransomware groups' next innovation might involve regulatory actions. Alphv/BlackCat recently claimed that it breached digital lending technology vendor MeridianLink, and then reported the organization to the U.S. Securities and Exchange Commission for failing to disclose the breach in a timely manner.
"There's talk about how attackers may be looking to bring regulatory pressure to bear," Budd said.
In response to ransomware groups' increased focus on managing the media, Sophos recommended not engaging with or crediting threat actors unless doing so provides actionable insight for defenders. In addition, the vendor pushed for support of journalists and researchers targeted by attackers.
Arielle Waldman is a Boston-based reporter covering enterprise security news.






