
kras99 - stock.adobe.com
Cyber insurers adapting to data-centric ransomware threats
Cyber insurance carriers and infosec vendors weigh in on how the shift in ransomware tactics is affecting policies and coverage, presenting challenges for enterprises.
Cyber insurance carriers are attempting to adapt to an evolving ransomware landscape where attackers rely less on encryption and more on data theft and extortion threats to pressure victims into paying.
Recently, ransomware groups have escalated their extortion threats by leaking highly sensitive data, including stolen photos and videos, if victim organizations don't adhere to the payment clock countdown. While data threats have become more brazen, the presence of actual ransomware in these attacks has dwindled as threat actors increasingly focus on stealing sensitive data instead of encrypting it.
This trend was most recently illustrated on a massive scale with the exploitation of a zero-day vulnerability in Progress Software's MoveIt Transfer managed file transfer (MFT) product. Around Memorial Day weekend, a threat actor associated with the Clop ransomware gang used the vulnerability to access and steal confidential data within organizations MoveIt Transfer instances, though the attacker did not encrypt the data. Since then, Clop has listed hundreds of MoveIT victim organizations on its dark web data leak site, including U.S. state governments.
A similar campaign occurred in January when by the Clop ransomware gang exploited a zero-day vulnerability in Fortra's GoAnywhere MFT software that was not patched until February. The attacks affected a approximately 130 customers including healthcare organizations and technology vendors such as Rubrik and Hitachi Energy. Again, the attacks relied on data extortion rather than encryption to pressure victims into paying.
However, Crowdstrike's 2023 Global Threat Report published in February shows the shift in extortion tactics started last year. Over the course of 2022, CrowdStrike discovered that 71% of all recorded attacks were malware free. When it came to ransomware activity, the cybersecurity vendor observed a 20% increase in the number of threat actors using data theft and extortion without deploying ransomware.
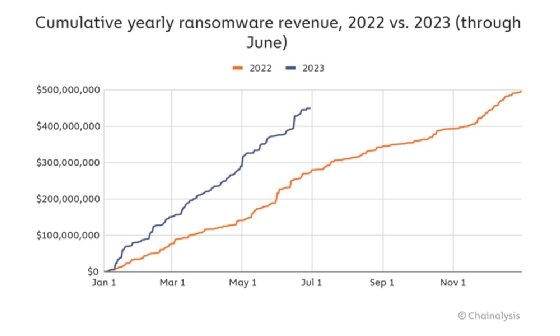
Whether ransomware gangs are encrypting data, it appears their recent attacks have been fruitful. Research this month by cryptocurrency analytics firm Chainalysis showed a sharp increase in ransomware payments for the first half of 2023. The most profitable group was Clop, which pulled in $1,730,486 compared to the median payment of $1,946,335.
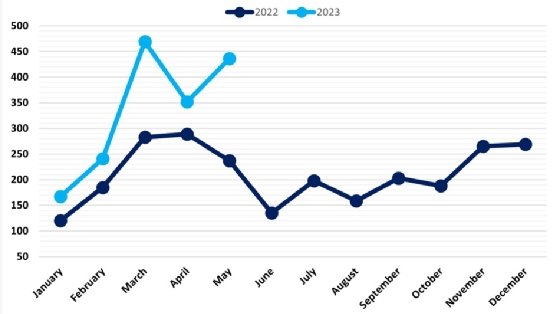
Despite a decline in encryption for these attacks, ransomware activity remains high. NCC Group analysis determined that so far this year, each month has seen a higher number of victims than its 2022 counterpart. May saw the second-highest number of recorded ransomware attacks in 2023 and June's incidents increased by 221% compared to June 2022.
As the ransomware landscape has shifted, data security has become a top priority. For cyber insurance carriers that play a significant role in ransomware response, that means re-examining policy requirements and the incident response process as well as applying increased focus on data security. Even though ransomware attacks that see no encrypted systems are generally less disruptive and costly, enterprises are facing further reductions in coverage and increased costs amid this shift.
Consequences for enterprises
Prior to the shift, insured organizations already faced increased premium costs and reductions in coverage. Fawaz Rasheed, field CISO at VMware, said the number one cyber insurance concern for enterprises is that coverage is contracting while premiums are expanding.
"By the same token, the other concern they have is around the level of scrutiny that's being applied towards them and the level of demands," Rasheed said. "One client said their insurer gave them 90 days to get endpoint detection and response in place; otherwise they'd be dropped. And it's not just having it in place. It's implementing it, operationalizing it and demonstrating that it's working."
Now enterprises may experience further challenges amid the shift to malware-free extortion attacks, even though it's a preferable outcome to an encrypted network. Cysurance CEO Kirsten Bay said the increased data breach element is affecting coverage and accelerating costs. She added that enterprises may also see more rigorous requirements for coverage going forward.
"We're seeing reductions around how much coverage an organization can get inside their policies. In many policies, they're cutting the total limit available if you have $1 million in total; they're cutting that down to $500,000, as an example," Bay said.
Catherine Lyle, head of claims at Coalition, said that while she's observed companies are less inclined to pay ransoms and have implemented better data backup processes, threat actors are banking on the implications of what happens once data exfiltration occurs. That's because the minute data leaves the door of an organization, enterprises are required to notify affected parties, including customers and vendors, even if no network disruption occurred.
"This is usually driven by the nature of the private data itself. For example, some companies may be concerned that their competitors will see the data, and some will be concerned that the nature of the private data is so important it deservers 'purchasing back' from the threat actor," Lyle said in an email to TechTarget Editorial.
Theresa Le, chief claims officer at cyber insurance provider Cowbell, also observed an uptick in the severity and frequency of classic ransomware and extortion attacks. "Particularly the extortion tactic of only exfiltrating the data and, therefore, the extortion price is not for a decryptor but only for the suppression of stolen data," she said in an email to TechTarget Editorial.
Joseph Carson, chief security scientist and advisory CISO at access management vendor Delinea, was not surprised by how cybercriminals have evolved from data encryption to data theft. However, he noted the evolution has left many insurance policies exposed to a change in ransomware tactics.
When ransomware became a top threat and held many organizations to financial ransoms to retrieve their data and business operations back, he said many organizations quickly turned to cyber insurance as a safety net. Policies included ransomware protection that focused on data recovery and incident response, but the needs are expanding.
"The cyber insurance industry is learning fast that the cyber threat landscape changes so frequently," Carson said in an email to TechTarget Editorial.
What can be done?
Implementing products that limit the risk of data extortion is a major area of focus for Cysurance. The company recently formed partnerships with Sophos and IT management vendor Kaseya, which itself experienced a significant ransomware attack in 2021. REvil ransomware actors used a zero-day vulnerability in Kaseya's VSA remote management product to send malicious updates to managed service provider customers, which then allowed the attackers to deploy ransomware on approximately 1,500 customers of the MSPs.
But the company recently teamed with Cysurance to launch the Kaseya Cyber Insurance Fast Track Program, which provides discounted coverage for customers that implement Kaseya's security products. Cysurance launched a similar partnership this month with Sophos that provides fixed-price coverage for customers that use the cybersecurity vendor's managed detection and response offering. The use of those certified products, combined with other factors, can aid in policy cost reductions for Cysurance customers.
Bay said establishing broader perimeter security postures and implementing privileged access management are also crucial to adapting to the ransomware evolution. "How do we manage escalation of privileges? Because that's really where [ransomware groups] are getting to those databases. It's difficult for insurers because for many of them, they're not imbedded into that network, and there's only so much they can require. The enforcement of the policies is becoming a very significant factor."
Le agreed that broader security postures are necessary, especially around securing sensitive data. Key strategies should focus on segregating the most impactful data inside an organization, she said. "Relatedly, organizations should carefully manage and secure the data they have that is of potential value to others because a threat actor may leverage or exploit those commercial relationships to create pressure to pay."
Cybersecurity vendors have reported that ransomware groups will contact competitors directly in addition to family members to increase the pressure on the victim organizations.
Another factor affected by the data-theft-only tactic is comprehensive insurance language, which Lyle said has evolved to include the desire to pay for deletion of data as a type of "recovery," which used to pertain to network and/or operational disruptions and downtime.
"Though this coverage would be implicated in light of the company's specific obligations or needs, and it not guaranteed, it's a way in which cyber insurance has adapted by leveling up to the attention to detail we're seeing amongst threat actors," Lyle said.
Many ransomware groups will promise to delete data if the ransom is paid, but Lyle said there is no guarantee that happens. Another problem Carson highlighted is that if the victim doesn't pay, someone who finds the data valuable may purchase that data. That provides cybercriminals with multiple ways to turn a financial profit.
"Cyber insurance will need to change the way it covers ransomware incidents to data loss and the tangible value and impact that the data has on the business, changing the way risk is measured and impacted," Carson said.






