
Getty Images/iStockphoto
Proofpoint: 'Hundreds' of Azure accounts compromised
Proofpoint researchers found that the attackers manipulated the MFA of compromised accounts, registering their own methods to maintain persistent access.
Proofpoint issued a security alert on Monday regarding an ongoing threat campaign that has compromised "hundreds" of Microsoft Azure user accounts across dozens of environments.
In a blog post, Proofpoint's Cloud Security Response Team detailed how unknown threat actors were combining spear phishing attacks with cloud account takeover techniques to target a wide range of individuals in different organizations across the globe. The emails contained "individualized phishing lures" in shared documents with malicious links for viewing the documents that redirected users to attacker-controlled domains.
"The affected user base encompasses a wide spectrum of positions, with frequent targets including Sales Directors, Account Managers, and Finance Managers," the blog post read. "Individuals holding executive positions such as 'Vice President, Operations', 'Chief Financial Officer & Treasurer' and 'President & CEO' were also among those targeted."
Proofpoint noted the threat actors used a Linux user agent -- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 -- to access the OfficeHome sign-in application. In a statement to TechTarget Editorial, Proofpoint's Cloud Security Response Team said the use of a Linux user agent indicates a departure for attackers from more traditional methods for account takeovers.
"This user-agent (UA) indicates the usage of Chrome 120 on a Linux system, and was observed in the majority of attacks attributed to this threat. This specific user-agent choice, combined with the targeted sign-in application ('OfficeHome'), provides insights into the tools and techniques employed by threat actors. Specifically, the use of this user-agent signifies a departure from traditional methods, such as legacy email protocols, or commonly observed user-agents, indicating a shift in the attackers' approach to impersonate user behavior and gain unauthorized access to email accounts."
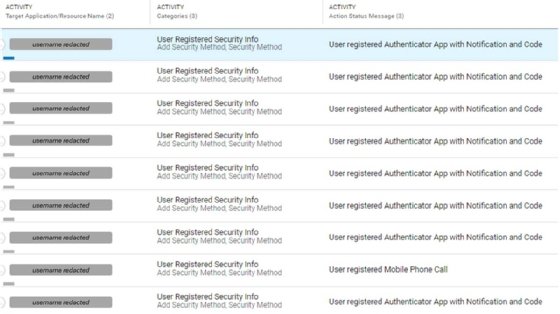
In addition to the Linux user-agent activity, Proofpoint observed unauthorized access to native Microsoft365 apps, including Office365 Shell WCSS-Client, which researchers said indicates browser access to Office365 applications; Office 365 Exchange Online, which indicates post-compromise mailbox abuse; My Signins, which indicates MFA manipulation; and MyApps and My Profile.
Proofpoint warned that following the successful compromise of Azure accounts, the threat actors maintained persistence in the victims' cloud environments by registering their own MFA factors, including alternative phone numbers for authentication via SMS, phone calls or an authenticator app.
The Cloud Security Response Team said the Azure account takeover campaign successfully compromised accounts that had MFA enabled as well as those that lacked such protection.
"In certain instances, compromised user accounts lacking existing MFA methods saw attackers registering new ones, usually opting for an Authenticator app with notification and code. Alternatively, in scenarios where the compromised account already had an MFA method in place, attackers supplemented it with their own," the team told TechTarget Editorial. "For example, our investigation surfaced instances where attacker-owned phone numbers were registered alongside legitimate numbers associated with affected users. These actions allowed attackers to maintain persistent access to hijacked accounts without having to steal their MFA tokens again."
The threat actors' post-compromise activity includes downloading sensitive data, including financial assets, internal security protocols and credentials; abusing mailbox access to launch internal and external phishing attacks with personalized content for targeted individuals; and initiating financial fraud schemes through emails sent to human resources and finance departments.
In addition, Proofpoint observed the threat actors creating new mailbox rules that were intended to obfuscate the compromises and remove any evidence of malicious activity. The attackers also used several proxies and hosting services as well as hijacked domains to cover their tracks.
While Proofpoint did not attribute the campaign to a specific threat actor or group, the research team found some evidence that could identify the attackers.
"Beyond the use of proxy services, we have seen attackers utilize certain local fixed-line ISPs, potentially exposing their geographical locations. Notable among these non-proxy sources are the Russia-based 'Selena Telecom LLC', and Nigerian providers 'Airtel Networks Limited' and 'MTN Nigeria Communication Limited'," the blog post read. "While Proofpoint has not currently attributed this campaign to any known threat actor, there is a possibility that Russian and Nigerian attackers may be involved, drawing parallels to previous cloud attacks."
The blog post included a list of indicators of compromise (IOCs). Proofpoint's recommended mitigations include monitoring for Linux user-agent string and malicious domains contained in the IOCs as well as securing accounts through periodic password changes and other practices.
Rob Wright is a longtime technology reporter who lives in the Boston area.







