
Getty Images/iStockphoto
Inside an Alphv/BlackCat ransomware attack
Sygnia researchers investigated an intrusion in a client's network and discovered an Alphv/BlackCat ransomware actor had been lurking in the environment for weeks.
Cybersecurity startup Sygnia shed new light on the notorious Alphv/BlackCat ransomware gang and its tactics after investigating an attempted attack against one of its customers.
In a blog post published Tuesday, the Israeli incident response (IR) firm chronicled the malicious activity conducted against its client as well as the tactics and modus operandi of Alphv/BlackCat. According to the research, the client engaged Sygnia's IR team in 2023 after it detected suspicious network activity.
"Sygnia's preliminary investigation revealed indications of a possible ransomware attack that might result in the encryption of the client's entire environment," wrote Oren Biderman, IR team leader and technical lead, and Amir Sadon, IR research director, in the blog post. "The attack was contained due to immediate actions taken by the client's IT team, principally by blocking all ingress and egress traffic to and from the central network assets."
Sygnia's IR team was able to collect "a unique set of findings" about Alphv/BlackCat, which has emerged as a top ransomware threat in recent years. A joint law enforcement operation seized the gang's infrastructure in December and produced a decryption tool, but the ransomware-as-a-service operation rebounded soon after.
Sygnia said the threat actor was unable to deploy the ransomware payload in the client's network and failed to cover its tracks. However, the threat actor was able to exfiltrate confidential data during the attack, which stretched approximately 30 days and stemmed from the compromised network of a third-party vendor. After repeated data exfiltration attempts, BlackCat contacted the client for an unspecified ransom demand and later published the stolen data to the ransomware gang's leak site.
Initial access and lateral movement
On day 1 of the timeline, BlackCat actors made several attempts to log into two of the client's servers using Microsoft's remote desktop protocol (RDP) and Server Message Block. The attempts, which came from the IP address of a third-party vendor with a host system named "DESKTOP-PSGDD89," resulted in three successful logins to one of the client's servers.
The next day, the threat actor launched a brute-force attack from one of the third-party vendor's servers, which targeted the same client server that the threat actor had successfully logged into the previous day. "This attack involved an attempt to perform authentication by utilizing users from two different AD [Active Directory] domains in the client's environment that have a shared trust," Biderman and Sadon wrote.
On the third day of the attack, the threat actor established an RDP connection from DESKTOP-PSGDD89 to another server in the client's network, which was used as a "pivot server" for lateral movement and network scanning, Sygnia said. The threat actor also began malicious activity inside the network, including issuing PowerShell commands; using a password dumping tool; and deploying Cobalt Strike, a red teaming product widely used by infosec professionals as well as attackers.
"Several Cobalt Strike framework capabilities were utilized by the threat actor throughout the course of the attack, including RDP tunnelling for lateral movement and process injection for the purposes of execution and evasion," the researchers wrote.
The threat actor also executed a Kerberoasting attack inside the network to retrieve password hashes from the client's Active Directory. The blog post included a screenshot of an alert from Microsoft Defender for Identity, which flagged the suspected Kerberoasting activity.
By Day 6 of the attack timeline, the threat actor started moving laterally through the client's environment from the pivot server using Cobalt Strike and different remote connection techniques. During the lateral movement phase of the attack, Day 6 to Day 20 of the timeline, the threat actor's malicious activity generated additional alerts and blocks.
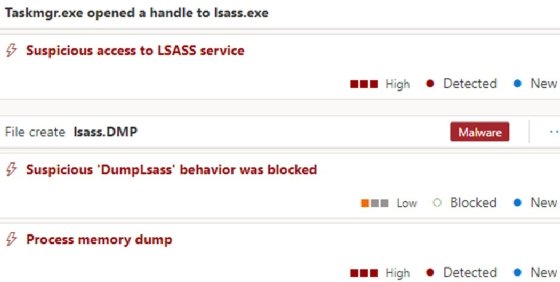
For example, Sygnia said the threat actor attempted to use Windows Task Manager to access credential data in the process memory of the Local Security Authority Subsystem Service, but the action was blocked by Microsoft Defender for Endpoint. Despite these alerts, the threat actor was able to deploy several open-source tools to establish remote connections to move between the on-premise network and the client's Azure environment.
Data exfiltration and extortion attempts
After two weeks of lateral movement, there was a gap in observed malicious activity inside the client's network. The threat actor appeared to be dormant for about a week, according to Sygnia's timeline. Biderman told TechTarget Editorial that Sygnia's IR team isn't sure why there was a gap. "It could be that the threat actor decided to lay low before continuing the activity, or maybe the remediation attempts damaged their ability," he said.
On Day 27 of the timeline, the threat actor began Phase 3 of the attack, which involved data exfiltration and additional lateral movement. Using Rclone, an open source tool for syncing and managing cloud storage, the threat actor attempted to exfiltrate data from several different hosts inside the client's network.
Two such attempts were successful, and the threat actor moved the "high volume" of stolen data to accounts with Wasabi Technologies, a cloud storage provider. Biderman said the client contacted Syngia during this stage of the attack.
"At this point, the client had been 'battling' with the threat actor for about a week. By this I mean the client had alerts, tried to remediate but failed and saw the threat actor returning," he said. "During the scoping call, Sygnia identified this was a ransomware threat actor, and we recommended they shut down traffic. It was difficult to convince the client at this stage that they needed to close off internet access, but they know and trust us from previous IRs. It took them another day to get the internal decision and shut off the internet. The shutdown interrupted the threat actor's exfiltration in the middle."
Additional exfiltration attempts were blocked by the client's firewall. Sygnia said the attack was contained when the client's IT team blocked all traffic to and from the network.
"This action may seem severe, but it was instrumental in stopping further data leakage and preventing the attacker from encrypting the network," Biderman and Sadon wrote. "It requires management courage to take such an action, which directly affects the business, but difficult times call for tough decisions."
After several days of exfiltration attempts, the threat actor began flooding the client with emails that threatened to expose sensitive data, demanding a ransom payment. After approximately two weeks, a representative for the client contacted the threat actor and received a "proof package" with samples of the stolen data. However, Sygnia and the client determined the threat actor was "exaggerating the volume and sensitivity of the stolen information."
As a result, the client did not pay the ransom, and the stolen data was published to Alphv/BlackCat's leak site several weeks later. "Lastly, this is not the first case where attackers overestimate the value of the information they have collected. The mere fact that information was leaked is not a reason to panic and pay," the researchers wrote in the blog post.
Editor's note: Emphasis by Sygnia.
Lessons learned
Sygnia said the IR investigation offered several insights into Alphv/BlackCat's techniques, including the amount of time the threat actor spent inside the client's network before initiating data exfiltration. Biderman and Sadon said the threat actor invested time in orienting his or herself with the environment, and it was this "orientation period" when the attack was at its most vulnerable. Despite the use of legitimate tools and open source programs, the threat actor was flagged in several alerts.
"With the right detection and response infrastructure -- encompassing technology, processes and human capabilities -- victims can stop the attacker in its tracks and totally prevent any damage from the organization," the researchers wrote.
In addition, the IR team found that the lateral movement to the client's cloud environment gave the threat actor a distinct advantage. The researchers noted that while the client's IT team blocked all internet access in its on-premises network, the threat actor used Azure Express Routes to bypass the firewall and maintain access to the client's environment.
Lastly, Biderman and Sadon said the IR case illustrates the risk that third-party partners can sometimes introduce to organizations. "Lately, we have noticed a trend of large companies being exploited via compromises of less security-mature third parties; this demonstrates the importance of organizations carefully mapping network connections with their vendors and limiting vendors' access to the minimum required," they wrote.
Rob Wright is a longtime reporter and senior news director for TechTarget Editorial's security team. He drives breaking infosec news and trends coverage. Have a tip? Email him.






