
Getty Images/iStockphoto
Why image-based phishing emails are difficult to detect
Image-based phishing emails are becoming increasingly popular with attackers. Learn how these hard-to-detect scams bypass email filters to infiltrate victims' systems.
Amateur phishing emails are still making the rounds, but these low-tech scams don't pose the same threat they once did. Sophisticated phishing attempts with high levels of obfuscation -- including image manipulation techniques -- are taking their place and wreaking havoc on employees, IT departments and companies alike.
How image-based phishing threats work
Image-based phishing scams use images in several ways. The entirety of the visual content of an email can be stored in a PNG or JPG file. This image can be easily identified by computing a cryptographic hash of the file. If the image was detected in a previous phishing attempt, any future email containing the same exact image would be blocked due to the cryptographic hash.
To bypass signature filtering, cybercriminals manipulate images in a number of ways:
- stretching the image
- changing the color or tone
- compressing the image
- adding some noise
These techniques are often visually insignificant by design and too slight for the naked eye to see. For a signature filter, however, the change is significant and consequential. The image's hash has completely changed and is no longer associated with a phishing email and, therefore, no longer a recognizable threat. This is one reason why users continue to receive the same phishing email, even after IT has blocked it.
To make things even harder, images are not embedded into an email, but rather hosted remotely, typically on a reputable domain, such as Wikipedia, GitHub or Google. This gives hackers a couple of advantages. First, the user sees an image in the email, but the filter only sees the link. If the URL is hosted on a reputable website -- which it often is -- the link can bypass the filter's reputation scan. Second, the filter can't analyze textual content placed on the image. This enables hackers to conceal textual signs of phishing, such as suspicious keywords or language.
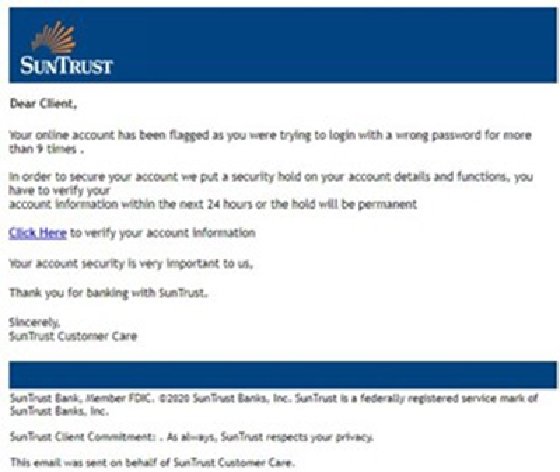
An example of image-based phishing
Here is an example of an image-based phishing email impersonating SunTrust Bank. Interestingly, the email is not an HTML combination of text and images, but rather a screenshot. Recipients wouldn't know they're looking at a screenshot. An email filter wouldn't know the content of the image either.
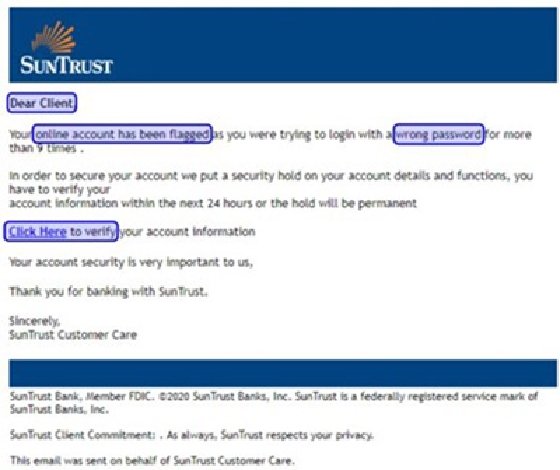
If the email filter could analyze the text in the above screenshot, it would flag several words that indicate phishing. The suspicious words are highlighted in this image.
This technique is also commonly used in sextortion emails, a form of phishing that typically includes a link for the victim to submit a bitcoin payment.
About the author
Sébastien Goutal is chief science officer at Vade Secure, where he directs scientific research operations. He leads a team of research scientists and research engineers developing supervised learning, unsupervised learning, natural language processing and computer vision technologies to detect advanced threats in email communications.





