
WavebreakmediaMicro - Fotolia
Combination of new, old tech driving remote access security
The massive shift to home-based workforces left IT vulnerable to unexpected threats, but organizations are combining old and new strategies to maintain remote access security.
It's been several months since the pandemic forced this unprecedented work-from-home situation, but there is still a long way to go when it comes to creating the same level of security when employees are working remotely compared to working from inside the corporate LAN. While most organizations offer a remote access VPN to those that require access to internal resources, an encrypted tunnel between the end user and the corporate network is no longer enough.
Authentication and authorization
One of the most common ways for a bad actor to access protected resources is to simply steal an employee's credentials. A username and password -- with the password being the single form of authentication -- should no longer be considered secure. According to a 2020 Data Breach Investigations Report from Verizon, slightly over 80% of all breaches are due to stolen credentials. This is especially concerning for employees that are working from home, as they tend to not follow their company's unique best practice security guidelines when away from the office.
To remedy this issue, multifactor authentication (MFA) is now recommended by the vast majority of security professionals. With MFA, more than just a password is required to gain access to corporate resources. Other ways to verify users are indeed who they claim to be include one-time passwords, challenge questions, biometrics or physical smart cards/tokens. According to Microsoft, deploying MFA within your organization can reduce credential-based security breaches by 99.9%.
Even once a user is verified through authentication, the data security risks don't end. Limiting what users can access once authenticated is of utmost importance. While there are manual methods to permit or deny what users can access once authenticated, they can become difficult to manage in organizations that have large numbers of users with various responsibilities. Instead, network access control (NAC) tools may be a more elegant approach.
These NAC tools that are deployed in a SaaS architecture can significantly streamline access control management and better protect sensitive data from accidently or intentionally leaking out. SaaS is becoming the preferred deployment method compared to on-premises NAC deployments in work-from-home (WFH) situations, as employees often access public cloud services more than services delivered within private data centers. Thus, a cloud-based NAC can better serve those who have fully migrated apps, data and services to public clouds -- or those in hybrid cloud architectures.
Endpoint management
Client-deployed malware prevention software is one easy way to protect users and their devices from accidentally introducing malware into their devices that can eventually proliferate throughout the entire corporate network. Modern antimalware protection software is deployable from a host of OSes and can be easily managed from a centralized administration interface.
For those seeking to better control the types of endpoint devices that can remotely connect and access corporate resources, unified endpoint management (UEM) tools might prove beneficial in large-scale situations where employees who WFH are also issued corporate endpoint devices. Among the many security features that a unified endpoint security system can offer is the ability to identify which devices are authorized to access corporate network resources and which should be denied. Additionally, corporate-deployed devices can be remotely managed from an OS and application patching perspective. The UEM tools provide a streamlined approach to verifying that devices connecting to sensitive resources are fully compliant from a corporate data security policy perspective.
A network-centric approach to remote access security
As mentioned previously, most enterprise organizations have long relied on a remote access VPN to create a secure tunnel between a remote employees' device and the corporate network. While a VPN is still considered to be secure from an encryption standpoint, it doesn't protect end users from all threats they're likely to encounter while working remotely. Remote access security also requires features commonly found on the edge of corporate networks, including enterprise-grade firewalls, intrusion prevention systems (IPSes), network-based malware prevention, secure web gateways (SWGs) and enterprise-grade Wi-Fi security.
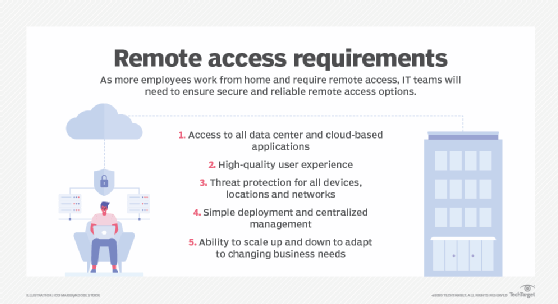
Forward-thinking IT departments have at least considered deploying network-based security tools to employees. These are often referred to as teleworker gateways or virtual branch network appliances. These mini-appliances can be easily deployed at employee homes and provide a host of security benefits, such as always-on VPN tunnels, firewall and IPS filtering, SWGs and the same Wi-Fi Protected Access 2-Enterprise protocols that are commonly offered in corporate facilities. The best part is that all these tools can be remotely and centrally managed by the IT department.
An alternative to hardware-based security tools is to roll out a virtual desktop infrastructure (VDI) that remote employees can use to access all corporate resources. In this architecture, end users utilize their likely unsecure end device to connect to a virtual desktop. This virtual desktop is tightly controlled by the IT department, and it eliminates many of the security risks found in employees using local hardware and software to interact with sensitive data.
Threat intelligence services
No matter what hardware- or software-based security solutions you decide to deploy for remote workers, the ability to push emerging threat protections to WFH-deployed firewalls, IPSes and malware prevention mechanisms should also be considered. The easiest way to do this is to tie security tools into a cloud-based threat intelligence service provider. The purpose of threat intelligence providers is for them to scan large portions of the internet to identify emerging or rapidly growing threats.
While threat intelligence services can be manually reviewed to keep security professionals notified about the latest threats, automating the process of security policy deployment is a better option for remote access security. Many threat intelligence providers will create security policies that protect endpoints and networks from emerging threats. These policies can be automatically pushed to certain security tools without the need for any user or administrator intervention. Doing so provides one of the fastest and most efficient ways to protect remote workers against these emerging risks.








