
Getty Images
What mobile network security tools should organizations use?
To manage security threats across devices and networks, IT administrators should implement tools and best practices for strong mobile network security.
As mobile threats evolve beyond malware to include network-based attacks, organizations need security tools that protect devices, regardless of location or connection type.
IT teams today must prioritize strong network security to protect sensitive data both at rest and in transit. They also need to address the unique challenges that mobile ecosystems pose, which extend far beyond traditional corporate networks and into the public internet.
To address evolving threats and secure both BYOD and corporate-owned mobile endpoints, IT must strategically deploy specialized network security tools.
Using general network security tools for mobile device security
Most IT teams deploy a range of tools that closely monitor and secure network devices, regardless of whether they're mobile or not. However, the rise of smartphone usage on corporate networks has exposed the limitations of traditional methods. As a result, there's been a shift toward modern architectures and technologies. These newer approaches better address the dynamic, mobile-centric needs of organizations.
General network security tools and frameworks include the following:
- Zero trust.
- Secure access service edge (SASE).
- Identity and access management (IAM).
- VPN.
- Network access control (NAC).
- Intrusion detection and prevention system (IDS/IPS).
- Secure web gateway (SWG).
While these tools can provide a foundation for mobile network protection, many don't fully address mobile threats.
How network security tools support mobile device security
Some of the most effective approaches to apply to both network and mobile security are zero trust, SASE and IAM.
A zero-trust security model ensures granular, application-level access. It's critical for securing mobile devices across corporate LANs, wireless LANs (WLANs) and untrusted networks, such as public Wi-Fi.
SASE can also address network and mobile device security comprehensively. This cloud security framework converges software-defined WAN with security functions such as zero-trust network access (ZTNA), SWG, cloud access security broker and firewall as a service.
IAM is a cornerstone of zero trust and SASE. It manages user authentication and network and application access permissions, which are key for mobile security when paired with multifactor authentication (MFA).
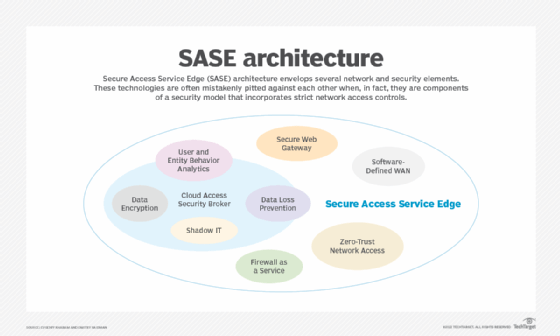
How network security tools fail to address mobile device security
Other network security mechanisms, such as VPN, NAC, IDS/IPS and SWG, are less effective for protecting mobile devices.
VPNs create a secure and encrypted tunnel between remote devices and corporate networks, historically used for remote access. However, VPNs have become outdated for some use cases. This is due to latency issues, as well as poor scalability for mobile-heavy environments. VPNs also present broad network access risks, as they enable lateral movement if compromised. SASE's ZTNA component can replace VPNs by providing secure, app-specific access.
NAC is a cybersecurity practice that restricts network access based on device compliance and user identity. Legacy NAC's static policy enforcement and bolt-on integration complexities hinder its ability to manage mobile devices. Cumbersome configurations are necessary to align with modern security frameworks.
IDS/IPS technologies monitor and block suspicious network activity. These tools can handle known threats but are less effective against mobile risks, such as app-based attacks.
SWGs are network edge security tools that filter web network traffic to identify and block malicious sites. While this capability is useful for mobile users, it's limited to web-only threats.
Mobile-specific network security tools
Although network-focused security tools and frameworks offer broad network protection, they often aren't enough to tackle the unique risks of mobile devices. These risks include app-based threats, untrusted or open network connections, and device theft or loss. Mobile ecosystems need specialized tools for security, both inside and outside the office.
To address mobile device security on enterprise networks, IT can use a few mobile-focused tools. Admins should consider MDM, mobile application management (MAM), mobile threat defense (MTD) and ZTNA for mobile.
MDM
MDM offers centralized management of mobile endpoints. Organizations can use these tools to enforce security policies, such as encryption, and enable remote actions, such as locking or wiping lost devices. MDM providers also ensure compliance with various standards across iOS and Android platforms. Popular platforms include Microsoft Intune and IBM Security MaaS360.
MAM
MAM tools secure specific corporate mobile apps by segmenting them from personal apps. Through features such as app wrapping and restricted data sharing, MAM blocks data leakage and protects user privacy. MAM is especially important for securing BYOD environments, where IT must balance end-user needs with enterprise security requirements. Popular tools with MAM features include Citrix Endpoint Management and ManageEngine Mobile Device Manager Plus.
MTD
MTD technology detects and mitigates both mobile-specific threats, like SMS phishing, and network attacks, like man-in-the-middle exploits. MTD providers, such as Zimperium, track device behavior and network traffic in real time, which ensures proactive protection for mobile vulnerabilities.
ZTNA for mobile
ZTNA enforces zero-trust principles for mobile devices at the network level. The framework verifies user identity, device posture and details such as location and OS version before granting access to specific applications. ZTNA can replace legacy VPNs, ensuring secure connections on corporate LANs, WLANs or public Wi-Fi. IT can integrate ZTNA with SASE platforms, such as Zscaler Private Access, or deploy the strategy on its own through products such as Okta Identity Cloud.
Mobile network security best practices for the enterprise
Enterprise IT must integrate general and mobile-specific network security tools with extensive policies to prevent data breaches. Admins should apply the following best practices to strengthen mobile network security:
- Clearly define mobile security policies. Create policies for BYOD and corporate-owned smartphones. Include details about enforcing encryption, MFA and remote wipe processes.
- Mandate MFA. Enforce MFA for all access. In this process, integrate IAM with zero trust and SASE to validate identities across mobile devices.
- Block insecure Wi-Fi. Configure MDM to block insecure Wi-Fi connections and require ZTNA for secure access. Also, make sure to inform users how to spot and avoid high-risk networks using an MTD tool.
- Integrate MTD with MDM. Combine MTD with MDM for real-time threat detection.
- Perform regular security audits. Conduct third-party audits and penetration tests to verify MDM and SASE configurations.
- Automate device updates. To prevent emerging vulnerabilities, enforce OS and app updates through MDM. In BYOD environments, use a MAM platform to update corporate apps. Additionally, educate users on why software updates are important for security.
- Conduct security awareness training. Educate employees on common attack vectors and best practices for mobile network security. Use online security courses, simulated phishing tests and webinars to reinforce secure mobile device usage practices.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.








