CASB vs. SASE: What's the difference?
CASB and SASE enhance network and SaaS application security. CASB acts as a security layer for cloud services, while SASE integrates networking and security into one framework.
In the rapidly evolving domain of cloud security, the integration of cloud access security brokers and secure access service edge offers a holistic approach for how organizations protect cloud-based resources and ensure network management. Enterprises can use both technologies to strengthen their security postures, but the distinctions between the two might not be so clear.
CASB functions as a security layer between the cloud service and users as it continuously secures access to an organization's cloud resources. CASB is especially useful to help secure SaaS applications because it can provide organizations with visibility and control of the systems. SASE, on the other hand, is a framework that consolidates networking and security functions into a single architecture.
While CASB and SASE are different services, CASB is often included as part of a SASE framework.
What is CASB?
CASB is a security policy enforcement point located between cloud service users and providers to enforce security policies. Enterprises use CASB to gain visibility and detect unusual behavior of cloud applications, regardless of whether resources reside on premises or within the cloud. CASB is crucial to ensure data protection and keep data in compliance with regulatory requirements.
Gartner coined the term CASB in 2012 when organizations began to adopt API-based cloud services after the emergence of SaaS business models and increased concerns of shadow IT. CASBs were initially designed to provide visibility and discover cloud application usage. CASBs have since evolved to provide controls over data security threat protection, which puts organizations in compliance with standards beyond traditional enterprise boundaries.
The shift to remote and hybrid work, as well as the adoption of SaaS, has created new visibility challenges for how organizations manage employee access to resources. These resources, when publicly accessible, require enterprises to have enhanced control over SaaS and user identities.
As SaaS reliance expands, CASBs have evolved to manage unsanctioned app usage and integrate identity within SaaS applications. These changes address the increasing complexity of SaaS and the need for advanced, adaptive security measures.
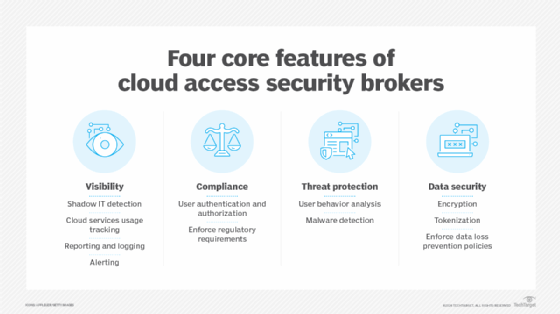
CASB features
CASB features include the following:
- Data loss prevention. CASB prohibits SaaS applications from storing sensitive information without proper authentication and authorization, which mitigates potential data loss.
- Threat protection. CASB monitors and analyzes user activities and transactions across SaaS applications, detecting and protecting against threats.
- User behavior analytics. CASB analyzes patterns of user behavior to identify potentially malicious activities and alert suspicious events.
- Encryption. CASB offers enhanced encryption capabilities beyond those of SaaS functions, which gives organizations control over data security at rest and in transit. Cryptographic keys protect sensitive information and safeguard it from unauthorized access.
- Access control. CASB regulates who can access specific SaaS resources under certain conditions and manages the permissions associated with their access.
- Compliance monitoring. CASB tools continuously monitor data stored in SaaS applications to ensure compliance with regulatory frameworks, like GDPR, HIPAA and others.
CASB cons
Despite its comprehensive security capabilities, CASB also has limitations. Challenges of CASB include the following:
- Complex integration. To provide comprehensive protection, CASB needs to integrate with other security tools, which can add complexity and additional costs, especially when tools are from different vendors.
- No network performance gain. While CASB supports SaaS application security and operates on the application layer, it doesn't address broader network performance challenges and route optimization issues.
- Limited scope of protection. CASB protection primarily applies to SaaS applications, which could leave other areas of the IT environment uncovered unless it integrates with other tools that are part of the overall security architecture.
What is SASE?
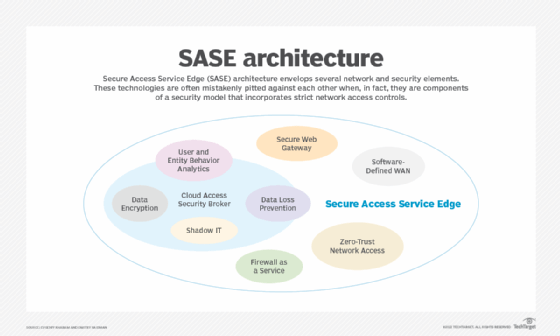
SASE is a cloud-delivered framework that combines networking and security services into a single architecture. Gartner coined the term in 2019 to describe the integration of software-defined WAN (SD-WAN) with a cloud-based security stack to support zero-trust network access (ZTNA) and replace traditional traffic backhaul with secure direct access.
The consolidation of networking and security features provides organizations with greater visibility and control of their network infrastructure. SASE enables enterprises to provide secure connectivity to branch office locations and remote users in a simplistic, flexible and scalable manner.
Gartner later coined the term security service edge, which describes the consolidation of security into a single vendor framework. SSE eliminates the networking component of SASE, which means it only includes security functions, such as CASB, secure web gateway (SWG) and firewalls. The key difference between SASE and SSE is SASE's inclusion of the SD-WAN component.
SASE features
SASE's benefits are compelling, particularly its ability to simplify network architecture, increase performance and enhance security management. SASE's features cater to the dynamic needs of modern enterprises, which enables it to support a distributed workforce and manage complex, multi-cloud environments.
SASE features include the following:
- CASB. Protects cloud data and improves network visibility.
- SWG. Controls internet access and blocks web-based threats, such as URL filtering and content inspection.
- ZTNA. Adheres to the zero-trust principles that dictate no entity should be automatically trusted, regardless of location, until authenticated and verified, which enhances security against unauthorized access.
- Firewalls. Provide network security as they filter incoming and outgoing network traffic based on predetermined security rules.
- Advanced threat protection. Protects against complex threats that traditional security measures might miss, such as ransomware or advanced persistent threats.
- Posture checks. Performs posture checks as part of its ZTNA approach to ensure that only compliant and secure devices and users gain access to network resources.
SASE cons
Despite the benefits of SASE, its adoption could create challenges for enterprises. Drawbacks of SASE include the following:
- Implementation challenges. The transition to a SASE architecture could require significant physical and virtual network infrastructure changes.
- Risk of vendor lock-in. The integrated nature of SASE could lead to dependency on a single vendor, which limits the flexibility of choosing different technology offerings.
- Emerging technology. Because SASE is a relatively new approach, standards and practices around the technology continue to develop, which might lead to growing pains and organizational resistance to change.
CASB and SASE integration
The integration of CASB and SASE combines the strengths of both technologies. While CASB focuses on cloud-specific security, SASE provides a broader, network-centric security framework. This combination is particularly effective for organizations with aims to secure their cloud environments and ensure seamless connectivity and comprehensive security across all network endpoints.
Organizations might want to consider an integrated approach to address their cloud security challenges. They should tailor the approach to their specific operational needs, cloud adoption strategies and overall IT security requirements.
For example, most modern infrastructure relies on internet browsers to access enterprise systems. The use of browser security services is a trend that has emerged in the SASE, CASB and SSE markets. Browser security services provide inline security capabilities, data leak prevention and remote access. While they are still far from full maturity, the potential exists for these domains to converge in the future.
CASB vs. SASE: Which one is better?
CASB and SASE both help secure an enterprise's cloud resources. SASE goes one step further than CASB because it includes networking functions in addition to security features. Neither tool is better than the other, and the choice to adopt one over the other depends on an organization's needs.
Enterprises that want to facilitate compliance requirements, improve threat protection and have greater visibility into the cloud might prefer CASB. Enterprises that want a comprehensive networking and security approach might prefer to adopt SASE. Nevertheless, the decision to implement CASB or SASE should occur once enterprises have a thorough understanding of each tool and how they align with the organization's specific network, security and business requirements.
The use of CASB or SASE enables organizations to safeguard their cloud and network resources effectively with powerful, policy-based enforcement and increased visibility. Moreover, enterprises can support dynamic business processes and distributed work environments.
Evgeniy Kharam is founder of EK Cyber and Media Consulting, where he combines industry knowledge and media expertise to guide clients through cybersecurity.
Dmitry Raidman is co-founder of Cybeats Technologies, where he focuses on software supply bills of materials and develops security integration platforms.







