
Getty Images
How to detect and fix a rooted Android phone
Rooting is a unique threat for enterprise mobile devices, but there are signs Android administrators and users can look for to detect it and steps they can take to fix it.
Rooted smartphones in the enterprise can pose a serious threat to security and compliance needs. What can IT administrators do to mitigate this risk?
Android has an open ecosystem, which means it's fairly easy for users to install apps from different locations. Still, Android smartphones are generally shipped to end users with an approved default OS. The device manufacturer has validated the OS to work within specified parameters and integrate some degree of security controls.
With root access privileges, a user can bypass certain security and operating constraints that are in place on their Android device. While this can give the user extra freedom and control over their phone, it also unlocks new risks. When an employee accesses corporate data or connects to the enterprise network on such a device, it can threaten the security of the organization at large.
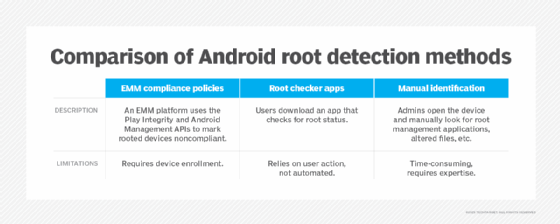
To find and remediate rooted devices, Android administrators can use enterprise mobility management (EMM) software and other tools.
How can IT use EMM to detect rooted Android devices?
There are a few ways that IT admins can pinpoint rooted Android phones. For organizations that have enrolled Android devices in an EMM platform, it's possible to identify rooted endpoints through the following processes:
- Checking for rooting indicators. EMMs can search for commonly used root management applications such as Magisk or SuperSU. They can also look for signs of altered system file permissions.
- Building tag verification. Default Android OSes from manufacturers generally have some form of tags for release keys. These indicate that an official developer digitally signed the release. Custom or rooted OSes don't have that tag. Instead, they have test keys or other unsigned code.
- Play Integrity API attestation. Google's Play Integrity API is a framework of security tools that can help determine if a device is running a modified or rooted version of Android.
Once an EMM identifies a rooted Android device, most platforms have some core capabilities to help limit risk. Admins can set up automatic compliance policies so that after detecting a rooted device, the EMM can take actions to keep it from affecting enterprise security. Measures include blocking enrollment in the network and revoking or restricting access to corporate resources.
How to set up rooted device detection in an EMM
Different management platforms might have specific workflow steps for identifying rooting. However, all EMMs that meet Google's Android Enterprise Recommended requirements have the built-in capability to detect and address rooting. The following example shows the detection setup process in Microsoft Intune, which is representative of many EMM workflows.
1. Create a compliance policy
First, navigate to Devices > Compliance policies.
Click Create Policy and select Android as the platform. Then, choose a policy name.
Under Device Health, locate the Rooted devices setting. Set it to Block to mark rooted devices as noncompliant.
2. Assign the policy
After creating the policy, assign it to the applicable user groups or device groups. To do this, select Assignments and choose the appropriate groups.
Save and then deploy the policy. The EMM will then analyze the devices during their next check-in.
3. Set up conditional access
This step can vary based on the EMM tool, but fundamentally, it's all about defining what should happen to devices that appear to be rooted.
Create a new policy, naming it "Block rooted devices."
Under Grant, select Require device to be marked as compliant to ensure only compliant devices can access resources.
Assign the policy to relevant users or groups and enable it.
How can IT detect rooting on unmanaged Android devices?
For Android phones that are not corporate-owned or managed by EMM, admins need to take different approaches to root detection.
Unmanaged Android phones are not, by default, open to the same level of inspection as EMM-enrolled devices. This means that automatic compliance checking and root detection might not always be available.
Options for root detection on these endpoints include the following:
- Root checker applications. There are many root checker apps available in the Google Play Store that can be used on a per-device basis to identify if a phone has been rooted.
- Network-based detection. IT can enable network security devices, including firewalls, to look for suspicious activity coming from Android devices. Rooted devices often have different network behaviors due to modified security frameworks, alternative application sources or compromised certificate usage. Network security monitoring tools can detect these rooting indicators.
- Performance issues and unusual behavior. If an Android user notices unexpected app crashes, unexplained data usage or unfamiliar apps on their smartphone, the device might be rooted.
- Disabled security features and updates. Failed software updates or disabled security settings often indicate that an Android phone has been rooted.
How to fix a rooted Android phone
The steps to unroot an Android device are straightforward for both managed and unmanaged devices.
After returning the device to its standard OS configuration, admins should make sure EMM security controls are in place. To prevent future threats involving rooting on unmanaged devices, implement tools and policies to protect the corporate network as well.
Unrooting an Android phone as an administrator
If the system has been rooted with Magisk, admins can push the Magisk uninstaller to the device.
If it's unclear what tool was used, deploy a stock firmware package to the compromised device. This should return the device to the default operating permissions. Admins can also do this as an extra step after pushing the appropriate uninstaller, just to be certain that the remediation is effective. Make sure a backup is available, as this method deletes user files.
Unrooting an Android phone as an end user
Users can follow similar steps to remediate an unmanaged device that was rooted with Magisk. Simply run the Magisk uninstaller and reboot.
If the system was rooted with SuperSU, open the SuperSU app and go to Settings. Select Full unroot. After the app automatically closes, reboot the device.
If the user doesn't know how the root occurred, or if other unrooting methods don't work, they should download the OEM firmware from the device vendor. This method also deletes user files, so it's important to check the available backup options beforehand.
Sean Michael Kerner is an IT consultant, technology enthusiast and tinkerer. He has pulled Token Ring, configured NetWare and been known to compile his own Linux kernel. He consults with industry and media organizations on technology issues.







