
Getty Images/iStockphoto
Understanding Android certificate management
Discover how to effectively manage digital certificates on Android devices, including installation methods, EMM tools and best practices for enterprise security.
In today's increasingly mobile organizations, with employees accessing corporate resources from anywhere, the risk of data breaches and unauthorized access is on the rise.
Digital certificates help reduce these risks by providing strong authentication and encryption mechanisms. As a result, they play an essential role in the security framework of Android devices by establishing a trusted connection between devices, applications and servers.
Mobile administrators need to understand how certificate management works within the Android ecosystem to maintain security, efficiency and UX in the enterprise.
What is a digital certificate?
A digital certificate is an electronic document or password file that authenticates the identity of users, apps or devices in a network. It is a basic part of public key infrastructure (PKI) that helps secure communications and authenticate entities. It also helps maintain data integrity when different entities share information.
Key terms related to digital certificate management include the following:
- Certificate authority (CA). A trusted entity that issues and manages digital certificates for websites, email services, organizations and users. CAs check the identities of certificate applicants and sign these certificates with their private keys to confirm they are genuine. Examples of major CA providers include DigiCert, GlobalSign, GoDaddy and Entrust.
- CA certificate. A certificate issued by a CA to intermediate authorities or end entities.
- Root certificate. A self-signed certificate at the top of the PKI hierarchy issued by a root CA. It signs other certificates, such as intermediate or end-entity certificates.
How do certificates work on Android?
As with other OSes, the certificate lifecycle in Android involves three phases: issuance, distribution and validation.
When a user, device or other entity submits a certificate request, a CA issues a digital certificate. This certificate should include the requester's public key and identity information, signed with the CA's private key to prove authenticity.
Next, a management platform distributes and uses the certificate for secure communications across the organization's IT environment. This might be an MDM, enterprise mobility management (EMM) or unified endpoint management platform. Google refers to all management platforms for Android devices in the enterprise as EMMs, so the rest of the article also uses EMM as an umbrella term.
Lastly, devices and systems validate certificates by checking the CA's signature against trusted root certificates. Android devices come preloaded with trusted root certificates from well-known certificate authorities, such as GlobalSign, Sectigo and Let's Encrypt.
The exact steps to view a list of all certificates installed on an Android device depend on the device model and OS version. On most Samsung devices, users should navigate to Settings, then select Biometrics and security > Other security settings > View security certificates (Figure 1).
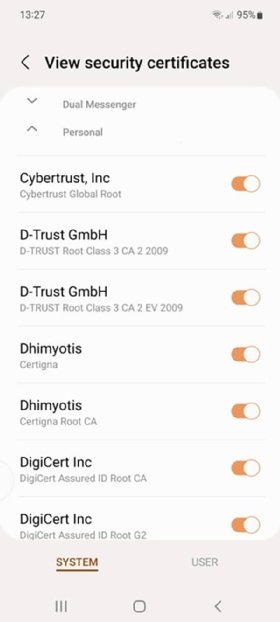
Android keeps digital certificates in the following storage locations:
- System CA store. This store is located in /system/etc/security/cacerts. It contains preinstalled trusted root certificates that come with the Android OS.
- User CA store. This store is located in /data/misc/user/0/cacerts-added. It contains user-installed certificates.
- Work profile certificate store. This store is for devices with Android Enterprise work profiles and maintains separate certificate stores for them.
Types of digital certificates in Android management
Common types of digital certificates include Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates, code signing certificates, email certificates, client certificates and root and intermediate certificates.
Android device management typically involves the following types of digital certificates:
- Device certificates. These authenticate devices in enterprise environments. A user might need a device certificate to connect to the corporate VPN or Wi-Fi. This ensures that only authorized devices can access sensitive resources.
- User certificates. IT assigns these certificates to individual users to grant secure access to resources such as email and cloud apps.
- Root and CA certificates. These are installed on devices to validate other certificates. Android devices have preloaded root certificates to verify SSL/TLS certificates for secure websites.
- Application certificates. These authenticate applications and verify they haven't been tampered with.
- EMM profile certificates. These authenticate EMM profiles on Android devices. For example, organizations can use EMM profile certificates on devices to adjust access privileges based on location without requiring device re-enrollment.
How to manage certificates on Android devices
Certificate management involves installing, updating and removing certificates from devices. Organizations must establish clear procedures for each phase of the certificate lifecycle to prevent security gaps and service disruptions.
The processes vary depending on the Android version and device model, so users might need to consult manufacturer documentation for the most appropriate steps. The following instructions reflect the process for most Samsung devices.
Installing certificates on Android
Users can install certificates through two methods.
The first option is to go to Settings > Biometrics and security > Other security settings > Install from device storage (Figure 2). Then, download the certificate online. When downloading a certificate from a web browser, Android prompts for installation and naming. If an admin completes this process, they should deploy the certificate through EMM tools using Device Policy Manager APIs.
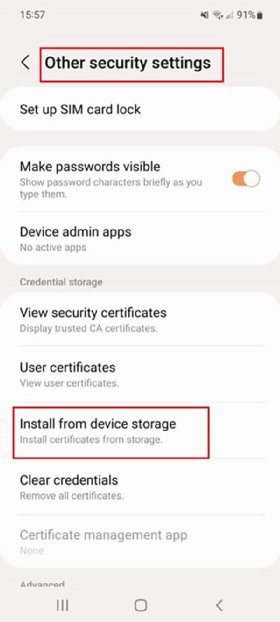
The other method requires the user to obtain the certificate file through download or transfer and then add it to the mobile device through email, EMM or USB. Open the file and follow the prompts to install it. The last step is to assign the certificate to a specific use case, such as Wi-Fi or VPN.
Updating certificates on Android
Updates are necessary when certificates expire or security requirements change. There are two main approaches to updating certificates on Android devices.
The first method is to use EMM tools to push certificate updates automatically. This approach is preferred for enterprise environments as it ensures all devices receive updates simultaneously without user intervention. The EMM platform can detect expiring certificates and deploy replacements before disruption occurs.
The second method is manual updating, which follows a similar process to installation. Navigate to Settings > Biometrics and security > Other security settings > View security certificates. Locate and select the certificate that needs updating, then click Replace. When a prompt appears, select the new certificate file from device storage. After verification, the system replaces the old certificate with the updated version while maintaining the same configuration settings.
Disabling certificates on Android
To disable certificates, open Settings. Navigate to Biometrics and security > Other security settings > View security certificates. Then, locate the certificate and turn it off (Figure 3).

EMM platforms also enable IT to remotely revoke certificates from lost or compromised devices.
Android certificate management best practices for IT
Security, efficiency and UX should be top priority when managing Android certificates.
For security, implement certificate-based encryption for all corporate communications. This keeps sensitive data, such as emails, file transfers and VPN traffic, safe from interception. To improve efficiency, automate certificate deployment and renewal, which also helps reduce the risk of human error. Maintain a positive UX by minimizing the number of authentication prompts users receive, and ensure corporate certificates don't compromise users' data in BYOD environments.
Beyond these core priorities, IT should be aware of the following issues:
- Certificate expiry. Expired certificates can interrupt VPN or email access. Automating the renewal process can help prevent this issue.
- Misconfiguration. Incorrect certificate setup can cause connectivity problems, requiring careful policy enforcement.
- OS versions. Certificate management might vary between different Android versions, which can complicate deployment.
Nihad A. Hassan is an independent cybersecurity consultant, digital forensics and cyber OSINT expert, online blogger and author with more than 15 years of experience in information security research. He has authored six books and numerous articles on information security. Nihad is highly involved in security training, education and motivation.







