
Kurhan - stock.adobe.com
HIPAA compliance checklist: The key to staying compliant in 2020
Putting together a HIPAA compliance program can be fraught with difficulty. Review best practices and a HIPAA compliance checklist to avoid common pitfalls and pass an audit.
In November 2019, an agreement was reached between Sentara Hospitals and the Office for Civil Rights around the hospital failing to meet HIPAA data breach notification requirements. The settlement resulted in the health group paying an approximate $3,700 fine per patient. While only a small number of patients were affected, the hospital learned the hard way that failure to comply with HIPAA could cost more than $2.175 million.
This is just one of many recent reminders that HIPAA compliance must be taken seriously. However, when a company's main business is healthcare and not IT, it can be difficult to fully understand the technical and administrative safeguard requirements around protected data, regardless of the resources available today.
Here, get insight on HIPAA's two fundamental rules, read up on the major elements of a HIPAA compliance program and review a HIPAA compliance checklist to ensure regulation requirements are satisfactorily met.
HIPAA Privacy Rule
One of the most fundamental guidelines within HIPAA is its Privacy Rule. The intent is to standardize the way protected health information (PHI) and individuals' health records are disclosed, modified and acquired. The guidelines apply to health plan providers, clearinghouses and other groups that exchange health information, as well as hosting providers and healthcare organizations' data centers.
The HIPAA Privacy Rule sets limits and conditions on what can be disclosed without patient authorization and ensures individuals' right to their health information, including the following:
- the right to see one's own health records;
- the ability to have corrections made to one's health information;
- the right to receive a notice that tells how one's own health information may be used and shared;
- the ability to decide if one's health information can be used or shared for certain purposes, such as marketing; and
- the right to get a report on when and why health information was shared for certain purposes.
Most healthcare organizations today use electronic medical record (EMR) or electronic health record (EHR) systems that export and share data with patients and other entities. Unfortunately, a lack of connectivity among healthcare organizations makes it difficult to easily share records, causing many to resort to letting patients download their health data and take it with them either in a physical or digital copy -- opening the data up to other security and privacy risks.
HIPAA Security Rule
The HIPAA Security Rule defines requirements around securing health data. The rule applies to any organization that interacts with electronic patient information, including hospitals, clinics, imaging centers, and claims processing and clearinghouses, as well as any vendor that comes in contact with it, such as EMR hosting providers and third-party IT vendors.
The HIPAA Security Rule has three standards that require compliance:
- physical safeguards around physical access to devices and systems that store PHI;
- technical safeguards to protect networked systems and devices to ensure the protection of any PHI data stored and transmitted through them; and
- administrative safeguards that address policies and procedures needed to ensure data protection steps are known and being followed by employees.
While these safeguards are mandatory, many IT departments find them difficult to interpret. This has resulted in additional resources, tools and costs, which have only added to the confusion. Fortunately, NIST provides a detailed guide to help organizations understand the various HIPAA requirements and rules, as well as how to implement them.
Fundamentals of a HIPAA compliance program
The difficulty most organizations have in complying with HIPAA results from the lack of well-thought-out IT governance. In other words, many companies do not establish clear organizational responsibility to ensure PHI security. According to HIPAA requirements, an individual must be assigned the responsibility of HIPAA compliance. Furthermore, NIST suggests the individual be authorized to establish controls and accept business risk. This means management must have ownership of both sensitive information and the policies defined to protect it. Once a clear business owner is established, HIPAA compliance requires coordination of a cross-disciplinary group, including business and technical management, legal departments and HR to ensure policies are defined appropriately, implemented correctly, disseminated to employees and enforced. While technology plays a significant role in compliance, organization and governance can either support or undermine the best technical controls.
HIPAA, like all regulations, requires transparency, and all activities associated with regulated data and systems are subject to audit. By establishing the appropriate policies and organizational structure, companies can put controls and the associated checks and balances in place to comply. Simply put, the overall goal is to ensure electronic PHI (ePHI) is:
- only accessible to those who have a business need;
- stored and processed on systems that are strictly controlled and backed up;
- monitored during all access; and
- only moved to authorized locations and encrypted in storage and while transmitted on unprotected networks.
These requirements reflect four security principles:
- identity and access management (IAM)
- system and environment configuration
- monitoring
- information flow control and encryption
These practices are central to HIPAA compliance and give rise to many critical process and technical controls, including network configuration, data loss detection and backup. The key idea to remember is that each of these important elements of compliance is part organizational process and part technology -- technology, by itself, cannot succeed.
Let's take a closer look.
1. IAM
A good example of the need for process and technology is ensuring appropriate access controls. The organizational process requires information owners, custodians and supervisors be involved in approving access to ePHI. While there is no explicit requirement for a technological remedy to this problem, many organizations address the need by deploying IAM tools. Without IAM, it is difficult to maintain the discipline necessary -- and the records of requests and approvals -- to ensure that only appropriate users have access. IAM systems can also automate account and privilege recertification, a requirement in HIPAA and many other regulations.
Conversely, lack of discipline and formality in IAM are some of the most common reasons for compliance failures. Interestingly, even if there is no inappropriate access allowed, the lack of formality in and of itself is a compliance violation.
2. System and environment configuration controls
Systems that store protected data must follow strict configuration guidelines. The underlying principle in controlling configuration is that organizations need to know the state of their critical systems in the regulated environment at any time. This involves more than just monitoring; it requires control. The requirement for tight systems control suggests that an organization should isolate each of them, configure them strictly for their purpose, maintain strict vulnerability controls and software version controls, and ensure systems are administered securely.
There are several organizational and design processes involved in achieving these goals. First, the organization must establish responsibility for managing the systems and networks. Second, it must establish a clear demarcation separating systems containing ePHI from those that do not. This isolation reduces the number of systems to tightly manage, cuts down on the monitoring burden and demonstrates good practices to an auditor. Third, it must establish strong vulnerability management practices for the environment.
Once organizational processes are in place, technology can be a real boon. Firewalls can establish boundaries, and vulnerability management systems can track OS and application versions and deploy fixes, while change control systems can keep tabs on all administrative activities affecting the regulated environment.
3. Monitoring
An important part of maintaining control over PHI is knowing who has and who has had access to the information. HIPAA requires all PHI access to be monitored. This means systems and applications that provide access need to be instrumented to capture access events. Further, an organization needs to look at its captured log information regularly.
Establishing that someone is responsible for monitoring and log review is of primary importance; deploying technology is secondary. One additional requirement is that the responsible party be separate from those entrusted to use or manage the systems. One need only look at the failures in compliance to understand why monitoring is so important. Many organizations look at logs only as a forensic tool, inspecting them solely after a suspected breach has occurred. This approach does not meet the intent of the Security Rule. The goal should be to know, at any time, who exercised the privilege to access sensitive data.
While smaller organizations may be able to manage log and event review with manual processes, event correlation and consolidation tools can help facilitate this difficult job. They can combine events from multiple systems, applications and environments, enabling the enterprise to concentrate on critical activities that might otherwise be lost in the noise.
4. Information flow control and encryption
The fourth element of compliance involves ensuring protected information only moves to safe locations and only moves when authorized. It is just as critical for data to be protected in motion as at rest.
Of course, there must be assigned responsibilities for controlling data and a process for authorizing its movement. HIPAA also requires deployment and administration of a variety of technologies. Organizations should assemble a data catalog detailing the type, sensitivity and assigned owner of all PHI. Processes should be defined to track where information moves. The procedures can aid in identifying when encryption will be necessary and provide guidance when employing technologies where appropriate. Tools like data loss prevention (DLP) can catch information with a defined signature if it moves over the network to some unauthorized location. DLP tools can also detect when data has been copied to unapproved devices. While good for key management, encryption products, too, can help meet in-place data encryption requirements.
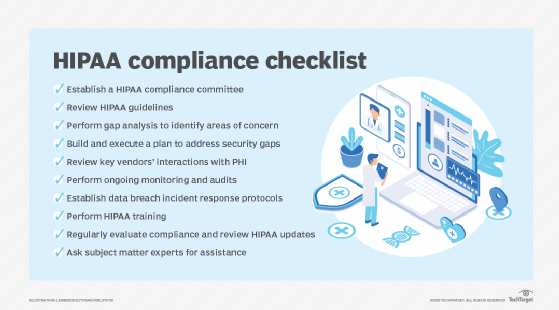
HIPAA compliance checklist
Complying with HIPAA must be carefully thought out and executed. This HIPAA compliance checklist will help get organizations on their paths to satisfactorily meeting regulations and rules:
Achieving HIPAA compliance is no easy task. Keeping in mind the fundamental elements of compliance, however, can make goals understandable and help organizations meet the challenge more effectively. Remember to establish the organizational processes first, and then employ technology to facilitate them. Processes and technology practices can be refined in time, but organizations must be sure that they clearly define who's responsible, what needs to be protected and how it needs to be protected.






