
cutimage - Fotolia
The CISO's guide to Kubernetes security and deployment
Container orchestration platform Kubernetes provides tools needed to deploy scalable applications with efficiency. Learn what steps CISOs must take to secure a Kubernetes environment.
Cloud computing provides access to powerful and flexible resources and services, but security challenges remain. These challenges can compromise cloud aspects such as Kubernetes clusters in unique ways, as cloud infrastructure continues to stray from legacy, on-premises applications.
The chief information security officer is responsible for safeguarding company data. CISOs must ensure stakeholders and customers feel confident that leadership adheres to established best practices and continually works to improve security posture. To achieve and maintain a robust security posture for the Kubernetes environment, new strategies must be combined with established security concepts.
To start, think about securing Kubernetes from two perspectives: features vs. habits.
A guide to Kubernetes security features
There are built-in Kubernetes features that can be used to set up and maintain a secure deployment.
There are several ways of authenticating to the Kubernetes API service, depending on the managed Kubernetes service used. Keep in mind that authentication will occur both for users and services. In general, CISOs should be aware that some authentication methods expose too much. An easy way to think about safe authentication methods is as follows:
- A more secure method is using OpenID Connect tokens based on OAuth 2.0, an open and modern form of authentication.
- Less secure methods include x509 certificates and static passwords. These are less secure, legacy forms of authentication.
Role-based access control (RBAC) manages who can access the Kubernetes API and what permissions they have. It's an improvement over the legacy attribute-based access control, because it's simpler to implement and easier to audit and maintain.
Some key things to consider when assigning permissions with RBAC include the following:
- Who really needs access? Only provide admin access when necessary.
- Some services may not need access to the Kubernetes API at all. Disable their access.
Just like in a virtual private network, the network policies within the Kubernetes clusters are important for dictating the traffic allowed to reach the clusters. These policies control the traffic within clusters and should be examined closely.
Remember to secure Kubernetes resources at the pod level, as well. This can be done using pod security contexts, which enable CISOs to set access control for any pods and the containers within the selected pods.
Kubernetes Secrets store sensitive data, such as passwords, API keys or authorization tokens. Items stored in secret objects help minimize their accidental exposure, as opposed to storing them in a more conventional way, such as in a container image.
Kubernetes security habits
As businesses adopt containers and container orchestrators at rapid rates, steps must be taken to safeguard the infrastructure. Follow these four best practices to improve security posture of containers and environments as a whole.
Divide workloads by need. Sensitive information should be run on its own resources, separated from others, so it's more isolated from exposure points to reduce infiltrations.
Use namespaces to separate resources. Much like the above concept of separating workloads by function, use namespaces to separate resources within Kubernetes. These types of logical separations create isolation between resources to lessen the potential for malicious activity.
Enable logging. Audit logging is not only useful for compliance needs. During a security incident, having it enabled is an effective best practice. The trail of logs can be monitored and referred to in case forensics needs to be conducted.
Don't forget to secure at the container level. Use the concepts used to safeguard Kubernetes clusters to secure actual containers, as well. The specifics will be based on the containers used, such as Docker or Rancher. Remember that all resources need to be considered to minimize any weak links in your chain.
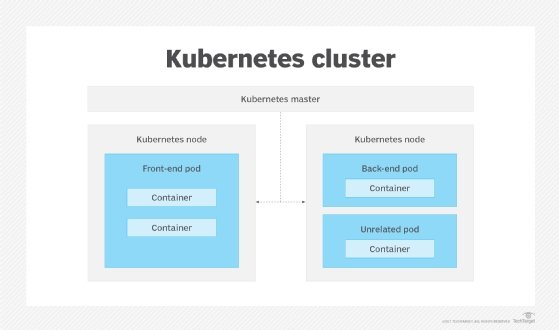
Extra tips to optimize Kubernetes deployment
In addition to Kubernetes security features and habits, there are a few notable measures CISOs should take that can improve deployment at an organization.
Keep Kubernetes deployment up to date. Like with any software security professionals manage, be sure to maintain updates as part of the security process. This helps CISOs stay current with the latest fixes found by Kubernetes and the Cloud Native Computing Foundation (CNCF).
Use expert resources such as the Center for Internet Security (CIS). Explore the CIS Benchmark for Kubernetes, a set of controls by industry experts to help maintain a hardened environment. There is no need to reinvent the wheel when there are dedicated professionals who work to make compliance accessible.
Keep talent up to date and motivated with certifications. CNCF provides useful certifications for Kubernetes administrators. These help ensure employees are current on the Kubernetes environment and also provide incentives and value to them as part of their professional development.
CISOs who already use Kubernetes gain efficiency and scalability from managing development teams that create Kubernetes-based applications and services. As a starting point, follow the recommendations stated above in this guide to Kubernetes security to get deployment in a secure state. As threats evolve, CISOs need to continually refine and change to stay safe and relevant in this dynamic environment.
About the author: Joe Nemer is a researcher and technical writer for Cloud Academy, an enterprise cloud training platform.




