
How to avoid Microsoft 365 management pitfalls
A migration to the cloud collaboration platform requires a command of the multiple admin portals available to admins to help the organization make the most of its subscription.
Microsoft 365 management involves much more than just configuration tweaks to a user's settings.
As the admin, you have granular control over what a user can -- and cannot -- do in each of the Microsoft 365 services and in the platform's security and compliance section. To maximize the potential of Microsoft 365, the following guidance helps with your understanding in several key areas related to compliance, email operations, configuration in the more popular Microsoft 365 services and licensing.
Why a hybrid arrangement makes Microsoft 365 management complex
Microsoft 365 management gets complicated due to the interaction between on-premises Active Directory (AD) and Microsoft Entra ID, formerly Azure Active Directory. Changes in one environment can affect the other, making tasks like assigning licenses and resetting passwords more complex. As the admin, you need to understand the various options and potential impact when applying changes to local and cloud domains.
Most users in an organization reside within on-premises AD and require synchronizing of related attributes to Microsoft Entra ID to use one set of credentials to use single-sign on.
After synchronization, managing a user becomes more complicated due to a primary account in on-premises AD and a cloud version in Microsoft Entra ID. For example, you assign licenses in the cloud, not on premises. You can also perform password resets in both locations, but this can lead to lockouts and other issues. Further complicating this is the multiple management methods Microsoft provides that you need to understand to work more efficiently and use effectively to avoid issues with accounts both on premises and in the cloud.
How to handle license management in Microsoft 365
Adding, changing, removing and monitoring license usage are all core tasks for the Microsoft 365 administrator.
You must assign licenses to the specific user or users within Microsoft Entra ID with one of several technologies: the Microsoft 365 admin center, Microsoft Entra admin center, Entra ID portal within Azure, PowerShell, Microsoft 365/Azure Command-Line Interface or Microsoft Graph. Choosing the right approach is essential, as users can only access features and services with the corresponding licenses.
Every option provides either direct or inherited assignments used with users in groups. The standard capability requires assigning licenses directly to users, while organizations with Entra ID premium licensing can use group license assignments.
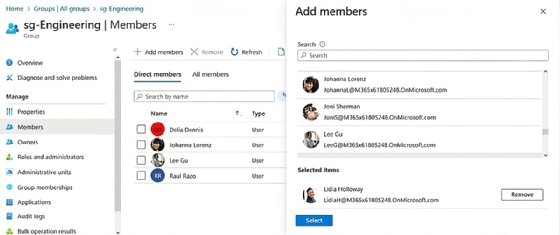
Choosing the correct Microsoft 365 management method depends on your organizational needs. If you manually assign licenses to users, then you can use either approach. If you want to assign licenses as users synchronize from on-premises AD to the cloud, then you can get the required license for the premium features and use group assignments. In group-based licensing, adding a user to a group automatically assigns the appropriate licenses associated with that group. Conversely, removing a user from the group also removes the corresponding licenses from the user, provided they're not part of another group with the same license.
In Microsoft 365, dynamic groups are an Entra ID feature that provides automatic membership management based on user attributes, which can be helpful for license management. When you create a dynamic group, you define rules based on user properties, such as department, location and job title. Entra ID automatically adds or removes users from the group based on these rules. For example, if you create a rule that all users in the sales department should be members of a certain group, any new user added to that department is automatically added to this group.
This feature helps large organizations use an automated approach to license management. Instead of manually assigning licenses to each user or writing complex scripts to automate the process, you can manage licenses at scale using Entra ID's dynamic group membership.
How to manage app-specific settings in Microsoft 365
Nearly all Microsoft 365 applications integrate and rely on core components and features. For example, many of the services integrate with OneDrive for Business and SharePoint Online for easier user adoption and management. However, not every configuration setting affects every application. For example, changing SharePoint Online sharing capabilities does not affect Microsoft Exchange or other services. However, changing the configuration for allowed domains can affect both.
Nearly all configuration settings for applications such as SharePoint Online, Exchange Online and even Microsoft Teams do not reside within Microsoft Entra ID. Most services have their administration portal or section within the main Microsoft 365 admin center or corresponding application portals.
The following are some common user settings in the more popular Microsoft 365 services that you can adjust in the admin portal.
Exchange Online
- Mailbox permissions. These set permissions to allow access to a user's mailbox and what actions they can perform.
- Mobile device policies. These apply various mobile device mailbox policies, including password length and password requirements.
These policies reside directly within Exchange Online. Admins can also work with policies in Microsoft Intune using mobile device management or mobile application management policies.
Microsoft Teams
- Teams policies. These determine the features available to Microsoft Teams users, including meeting policies, messaging policies and app setup policies.
- Guest permissions. These settings control what guests can do in a team.
OneDrive for Business
- Storage quota. This is the amount of storage available to each user.
- Sharing. This sets the sharing capabilities of users, including whether they can distribute files externally and what type of link they can use to share.
- Device access. These settings control which devices can sync with OneDrive.
SharePoint Online
- Sharing. Like OneDrive, this controls the sharing capabilities of SharePoint sites.
- Access control. These settings dictate the IP addresses users can employ to access SharePoint Online and app access.
- External collaboration settings. These control user content sharing with people outside your organization. To configure these settings, you must use the Microsoft Entra admin center or the Entra ID area in the Azure portal.
How to work with Exchange Online mailbox management
You manage Exchange Online mailboxes using the Microsoft 365 admin portal. One of the critical tasks in this area is creating shared mailboxes, which let multiple users send and receive emails from a collective address.
This feature is especially beneficial for departmental communications to give several team members access to the same email conversations, such as a customer service mailbox that all support team members have access to for efficient handling of client inquiries.
Assigning mailbox permissions is another critical task in the Microsoft 365 admin portal. It involves determining who has access to a particular mailbox and their access level. You can assign full access; send-as or send-on-behalf permissions, depending on the organization's needs; and its members' specific roles. With full access, a user can open the mailbox and access all content. With send-as delegate rights, a user can send an email to make it appear it originated from the shared mailbox. Send-on-behalf delegate rights let the user send email on behalf of the shared mailbox, but the recipients see one user sent it on behalf of another.
Email forwarding is another vital function in Exchange Online to automatically redirect emails from one mailbox to another. This feature is useful for routing messages sent to employees who have left the organization or are on extended leave to ensure the team gets all critical communication. Administrators set up the system to forward all incoming mail from the absent employee's address to another active team member's inbox.
How to work with security and compliance
Microsoft 365 provides a powerful suite of security and compliance features that help protect data and maintain compliance with legal and organizational standards. You can manage these features -- data loss prevention (DLP), sensitivity labels, retention policies and e-discovery -- through the Microsoft 365 compliance center.
DLP prevents sensitive data from leaving the organization, such as credit card numbers, Social Security numbers and other types of sensitive information defined by the organization. In the Microsoft 365 compliance center, you create DLP policies that identify this sensitive information and prevent sharing.
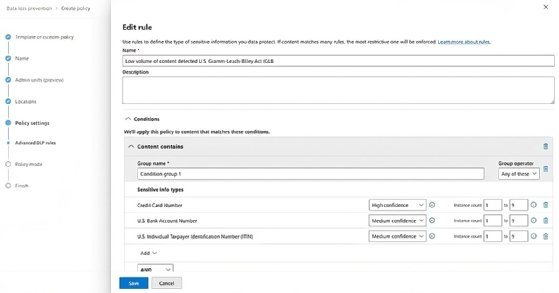
For example, you might have a policy that prevents an email containing credit card information from being sent outside the organization.
Using sensitivity labels in Microsoft 365, organizations classify and protect restricted information across applications. Each label can represent varying sensitivity levels and apply corresponding protections. For instance, a label named confidential could encrypt documents and emails or restrict access to content. You manage and apply sensitivity labels via the Microsoft 365 compliance center, and users can apply these labels to their documents and email in apps such as Word, Excel, PowerPoint and Outlook.
Retention policies in Microsoft 365 manage the information lifecycle and comply with industry regulations to determine how long to keep content and what to do at the end of the lifecycle. You can set up retention policies in the Microsoft 365 compliance center to preserve content for a certain period or delete content after it becomes obsolete. For example, a retention policy could automatically delete email in a user's mailbox older than seven years.
Microsoft 365 e-discovery finds, holds and exports content in response to legal cases or investigations. With e-discovery, you search for content across Microsoft 365, hold that content to prevent it from being modified or deleted, and then export it for further analysis.
Liam Cleary runs his own consulting company that helps customers work with Microsoft 365 and Azure-based technologies. He specializes in internal and external collaboration, document and records management, business process automation and security measure implementation.





