
How to use Windows Server 2022 secured-core server features
Microsoft's latest server operating system attempts to prevent attacks in the data center by locking down access to traditionally vulnerable areas, such as the system firmware.
With its Windows Server 2022 release, Microsoft emphasized security in its secured-core server features to thwart threat actors who target on-premises workloads.
Virtualized Windows Server workloads often come from a cloud provider template, which typically comes configured with customized security baseline settings. In contrast, Windows Server deployments that run on-premises environments might not have the same security configuration, which makes them attractive targets. Microsoft introduced the concept of a secured-core server in Windows Server 2022 to prevent hacking and ransomware attempts. Secured-core servers use the Trusted Platform Module (TPM) and other hardware features to keep an attacker from undermining the Windows Server operating system's integrity. With Windows Admin Center, administrators can adjust and check on the secured-core server settings to make it easier to implement these features.
Several features combine to make up a secured-core server
Microsoft's secured-core server feature follows the defense-in-depth strategy where, if the attacker avoids one defensive measure, then there are several more to prevent the attacker from going further in the infrastructure. This Windows Server 2022 security feature checks to ensure the operating system is not modified and guards data in memory to avoid leaking sensitive information.
A secured-core system combines the software protections in the operating system with the hardware defenses in the server to stop intruders from launching a variety of attacks. A secured-core server consists of several features that can be enabled individually or collectively.
Hypervisor Enforced Code Integrity. HVCI does three things. First, it prevents changes to the Control Flow Guard bitmap to stop memory-based attacks. Second, it checks for valid certificates for trusted processes, such as Credential Guard, before they load into the system memory. Lastly, the modern device drivers need to both support HVCI and have an extended validation certificate. Incompatible drivers or applications can potentially cause the server to display the Blue Screen of Death.
Boot Direct Memory Access (DMA) protection. This feature protects the system against DMA attacks from attached devices, such as a USB drive, during the boot process and runtime by blocking access to system memory.
System Guard. This feature uses attestation to prevent tampering with OS files. This feature detects operating system files that have been modified or replaced by counterfeit files.
Secure Boot. This feature verifies the integrity of the low-level components used in the boot process. This includes the Unified Extensible Firmware Interface (UEFI) firmware drivers, UEFI applications and the operating system.
Virtualization Based Security (VBS). This feature uses hardware virtualization to store security information in a sandboxed area that is inaccessible to running processes.
Trusted Platform Module. This hardware component is part of what Microsoft calls the hardware root of trust. The TPM can either be a chip on the motherboard or part of the firmware that the operating system or applications cannot access. Microsoft requires the 2.0 version of the TPM specification on server hardware. The TPM 2.0 chip verifies the authenticity of the firmware and other software before it allows the operating system to start. The TPM also stores cryptographic keys used with BitLocker.
How to set up the secured-core server
Cybercriminals often target Windows Server workloads that run in the data center because these deployments might not have the most stringent security settings. A perennial issue for Windows Server admins is how difficult it is to set up security configuration. The Windows Admin Center attempts to lower the technical hurdles associated with the setup and monitoring of the secured-core server settings.
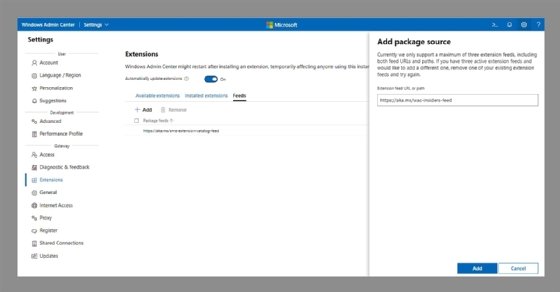
Using the Windows Admin Center to configure the Windows Server 2022 secured-core settings requires enabling what Microsoft calls the "insider's feed" extension. Open the Windows Admin Center, click on Settings, and then click on Extensions on the left side of the screen. Next, click on Feeds, and then click on the Add option. When prompted, enter the https://aka.ms/wac-insiders-feed URL as shown in Figure 1. Click the Add button at the bottom-right to complete the process.
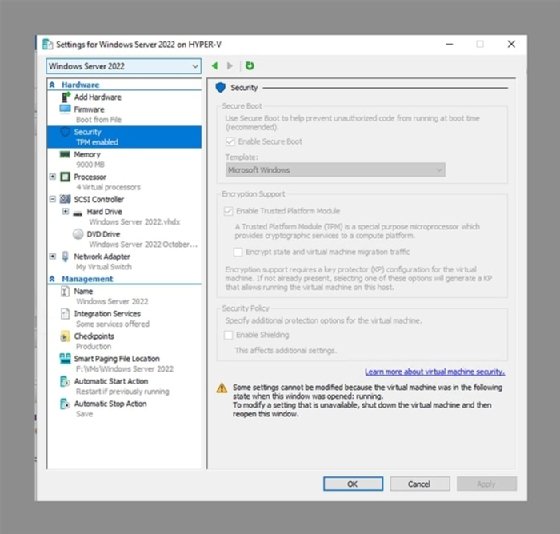
After adding the extension, you can enable the secured-core server features if the system supports TPM 2.0. If you are running Windows Server on a VM, then you will need to enable virtual TPM for the VM. Virtual TPM is supported both on Hyper-V and on VMware. You can see Hyper-V virtual TPM settings in Figure 2.
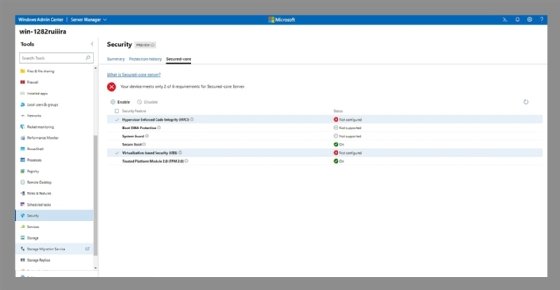
Next, click on the server to turn on the secured-core server feature. Click on the Security option on the left side of the screen and then click on the Secured-core tab near the top of the screen. Select the checkboxes for the desired security features. Not every system will support all the secured-core security features. For example, Figure 3 shows that this server cannot use Boot DMA Protection or System Guard. After making the selections, click the Enable option and reboot the server to complete the process.
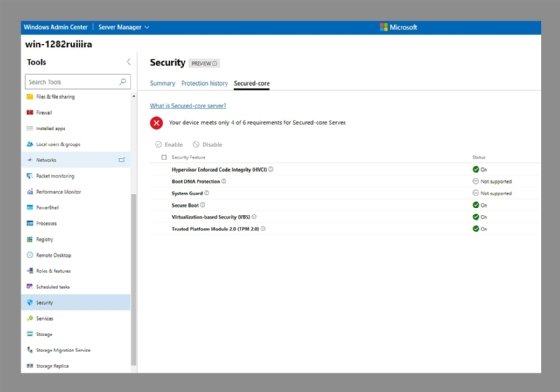
After the server reboots, the Windows Admin Center should show the selected security features have been enabled, as shown in Figure 4.
The new security features in Windows Server 2022 combined with the easier accessibility to configuration features from the Windows Admin Center are part of Microsoft's effort to keep threat actors from causing disruptions and launching ransomware attacks. Certified server hardware with the requisite firmware running Windows Server 2022 can help organizations improve their defensive posture to avoid being a security statistic.







