
Getty Images
Azure Arc setup tips for on-premises server management
Admins should explore their patching options now that Microsoft deprecated WSUS. Azure Arc offers integration with Azure to give the operations team a unified management approach.
Following the WSUS deprecation notice, enterprises that have yet to shift their patch management process will want to take a closer look at alternatives, such as the Azure Arc and the Azure Update Manager service.
Patch management is a critical task to keep Windows Server environments secure, stable and performant. In September 2024, Microsoft signaled to customers that it will no longer add new features to Windows Server Update Services (WSUS) and recommended exploring other avenues. Microsoft offers several options to keep Windows Server up to date with the latest software. One tool that has been gaining traction since its introduction in November 2019 is Azure Arc, a tool for admins to manage on-premises and cloud infrastructure via the Azure control plane. Azure Arc also extends Azure services, such as Azure Monitor and Azure Policy, to Windows Server workloads in the data center. This tutorial will cover the Azure Arc setup process and run through the patch deployment of an on-premises server.
Why Azure Arc is an effective tool for patching
Larger organizations often rely on either WSUS or on a third-party patch management tool. These utilities can scale to handle many servers, while also providing rich reporting capabilities to help organizations assess their patch management status.
Although WSUS does a good job of keeping Windows machines up to date with the latest fixes, it is primarily designed for on-premises patch management. Companies that host workloads both on premises and in the Azure cloud might use a patch management tool in their data center and another within Azure. However, there is a convenient way to use the Azure Update Manager to handle patch management both in the cloud and on-premises.
The key to using Azure Arc with on-premises servers is to "Arc-enable" the servers, as Microsoft calls it. Azure Arc is a service designed to manage physical servers and VMs both on-premises and in Azure and other clouds. Azure Arc can also handle Kubernetes clusters and databases.
Arc-enabling a server or VM just requires installing the Azure Connected Machine agent onto the server. There's no need to set up a VPN or establish direct connectivity to Azure, as long as the machine has Internet access.
Microsoft makes the Azure Arc control plane available for free. This means that you can use Azure Arc to tag resources and to enable search and indexing for those resources. The free Azure Arc plan also lets you take advantage of Role Based Access Control (RBAC) permissions and you can use templates to automate various tasks. If an organization is using VMware vCenter or System Center Virtual Machine Manager, then you can use the Azure Arc control plane to inventory your resources and to perform lifecycle management for your VMs. To use Azure Update Manager in Arc-enabled VMs costs $0.162 per server per day or $5 per server per month for months with 31 days.
Microsoft does not charge when a customer uses Azure Update Manager in the following scenarios:
- the Arc-enabled VM has Extended Security Updates (ESUs);
- the subscription that hosts the Arc-enabled VM also has Microsoft Defender for Servers Plan 2; or
- the Arc-enabled VM uses Windows Server licenses with either active Software Assurance license or Windows Server pay-as-you-go.
While Microsoft allows free access to the Azure Arc control plane, any Azure cloud services exposed through SCVMM or VMware vCenter will incur standard Azure usage charges. The same holds true for Azure services consumed through Arc-enabled Kubernetes clusters. Microsoft also charges a fee for Extended Security Updates (ESUs) for legacy systems and using Azure Arc to manage SQL Server instances.
How to connect Azure Arc to a server using the Azure portal
Configuring servers to use Azure Arc involves deploying the Azure Connected Machine agent to the VMs, using the Azure portal, Azure CLI or PowerShell.
First, log in to the Azure portal and open the Azure Arc service. Click the Add Resources button, then click on the Add/Create button under the Machines section. Choose the Add a Machine option after the prompt to begin the onboarding process.
Next, the console will prompt to specify the type of resource to onboard. For the purposes of this article, choose Add a Single Server with Installer. (Azure Arc also provides options to onboard multiple servers at once, including Linux VMs.) Azure Arc will download an installer file in your browser. Copy the installer file to the server you want to manage with Azure Arc.
Next, go to the VM to manage and launch the executable. The installer will start a wizard for the installation process, which will require signing into Azure and choosing the subscription. When complete, Azure Arc can now manage the VM via the Azure Connected Machine agent.
How to manage patches for Arc-enabled servers
After onboarding the server to Azure Arc, configure that server to receive updates. Start by opening the Azure Update Manager service in the Azure portal, then select the Resources tab and click Machines. The Arc-enabled server should be listed on the Machines tab.
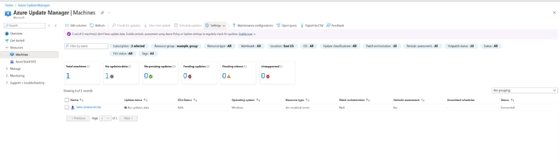
The screenshot shows a console message that "1 out of 1 machine(s) don't have update data." To enable automatic updates for the machine, click the Enable Now link located at the end of the message. Alternatively, click the Check for Updates button to start an immediate update check for the VM.
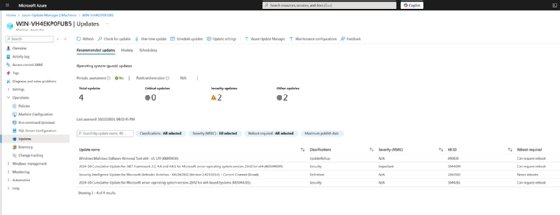
After the update assessment, the Azure Update Manager dashboard may show a message about pending updates. Click the message to see the results. The options are to either install the updates immediately or schedule them during a maintenance window. Note that there might be delays when forcing an immediate update. During testing, it took 30 minutes from the start of the update until the dashboard updated the VM's status. IT administrators will need to account for this delay when verifying update compliance and to avoid unnecessary troubleshooting.
How to connect a server to Azure Arc with PowerShell
Instead of the Azure portal, PowerShell is another option for admins who prefer this method. To start, install the Az.ConnectedMachine module with this command:
Install-Module -Name Az.ConnectedMachine
Next, use the Connect-AZAccount command to log into Azure. Lastly, install the Azure Connected Machine agent with this command:
Connect-AzConnectedMachine -ResourceGroupName myResourceGroup -Name myMachineName -Location <region>
The command downloads the Connected Machine agent, installs it on the server, creates the Azure Arc-enabled server resource and associates it with the agent. The onboarding process takes a few minutes to complete.
This concludes the setup necessary to use Azure Arc for patch management. However, for other tasks that require secure remote access, Azure Arc allows connections to Arc-enabled machines using Remote Desktop Protocol (RDP) and the Windows Admin Center extension in Azure or SSH with either Azure CLI or PowerShell.
How to use the reporting feature in Azure Arc
While the Azure Update Manager dashboard provide information regarding the patch management status of Arc-enabled machines, Azure Arc can generate more detailed reports.
To start, expand the console's Monitoring container and then click on the Reports tab. Next, click on the Overview report in the Azure Update Manager section.
At the Reports screen, select the subscription from the menu. By default, the report will span the entire tenant, so it's helpful to filter by region, resource type and time range. You can save the report by clicking on the Save icon.
You can filter the report by location, resource type, or time range. Azure Workbooks connect to Azure Arc for even more granular information related to patching, including compliance status across the infrastructure, security update install success rates and update deployment history.






