Techniques for performing EFS recovery
IT pros face the daunting task of EFS-encrypted data, but Brien Posey offers EFS recovery tricks in this tip.
One particularly challenging problem that many IT pros face sooner or later is that of recovering data that has been encrypted using EFS. In this article, I will give you some EFS recovery tricks to try.
The Microsoft Windows Encrypting File System (EFS) uses encryption keys to encrypt and decrypt data. This seems obvious, but it's an important point. All techniques in this article are based on key recovery. Not all Microsoft encryption solutions are key-based. Some use reversible hashes instead.
Most of the problems that I have encountered with regard to the inability to access encrypted data have to do with encryption keys that were accidentally lost (or user profiles that were accidentally deleted). Thankfully, a lost encryption key does not necessarily mean that the data will remain encrypted forever. There are sometimes ways to recover the data.
Restore a backup
The easiest way to recover EFS encrypted data is to restore a backup from a time before the data was encrypted or from before the encryption keys were lost. If no backup exists, you will have to resort to other methods.
Check the version of Windows that is being used
Older versions of Windows were often plagued with security vulnerabilities. Sometimes it may be possible to use an unpatched vulnerability to your advantage. The best example of this concept is related to a bug in Windows Vista and Windows Server 2008.
When a user opens an EFS encrypted file, the file is decrypted and is stored in a decrypted form until the user closes it. At that time, the file is re-encrypted. When a user opens an encrypted file on Windows Vista or Windows Server 2008, the file's contents are written to a temporary file named EFS0.tmp (incremental file names are used if multiple encrypted files are open). This temporary file is deleted when the encrypted file is closed. However, a bug in unpatched versions of the operating system causes the temporary file not to be zeroed out when it's deleted. As such, it is possible to use any recovery utility for deleted files to recover unencrypted versions of encrypted files. The actual details of this vulnerability can be found at the Microsoft Support site.
Use a data recovery agent
Your best option for recovering an encrypted file involves the use of a data recovery agent. When a user encrypts a file or folder, a data recovery agent's keys are added to the encrypted file. This is an automated process. If the computer is not joined to a domain, the recovery agent is the local administrator account. If the computer is domain-joined, the recovery agent is the domain administrator account. Keep in mind, however, that the computer's domain membership at the time of encryption is what really matters. For example, if a user encrypts a file and the computer is later joined to a domain, the local administrator account will remain the data recovery agent. The domain administrator will not have recovery privileges.
Thankfully, Microsoft does not make you guess who has the ability to access encrypted files. Every version of Windows since Windows 2000 has included a command-line tool called Cipher.exe that can be used to encrypt, decrypt or extract information about EFS encrypted files. If you want to know who has permission to open an encrypted file, navigate to the folder containing the file and enter the following command: Cipher /C. You can see an example of this command's output in Figure A.
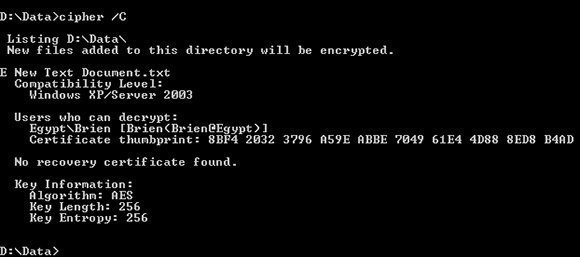
Figure A. You can use the Cipher command to determine who has access to encrypted files.
As you can see in the figure, the Cipher command will tell you who has the ability to decrypt the files. Keep in mind that some versions of Windows will hide the local administrator account, so if you don't see the administrator account listed, it doesn't mean that the administrator cannot decrypt the files. Once you know who the data recovery agent is, you only need to log into the computer using that account, open an elevated Command Prompt window, navigate to the folder containing the encrypted file, and enter the following command: Cipher /D *.* There are ways of doing this without knowing the username and password, but this article assumes that someone knows the password for the recovery account.
You can see what the decryption process looks like in Figure B.
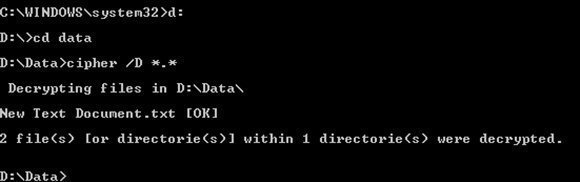
Figure B. You can use the Cipher /D command to decrypt encrypted files.
Conclusion
Microsoft makes it relatively easy to retrieve EFS encrypted files. However, EFS recovery becomes nearly impossible if a clean copy of Windows is installed on top of a previous copy, because doing so can wipe out the encryption keys that are used to decrypt the files.





