
Getty Images
Data tenancy maturity model boosts performance and security
A data tenancy maturity model can boost an organization's data operations and help improve the protection of customer data. Improvement is tracked through tiers of data tenancy.
Data tenancy done right can be a competitive differentiator to win in the marketplace. Providers who understand their service's data tenancy maturity not only gauge its current achievement but identify areas of improvement.
Safeguarding tenant data is an essential aspect of service offerings. A maturity model is an effective tool for objectively evaluating the performance of a data tenancy capability for a specific data repository. It provides tiered levels of achievement with measures across different viewpoints.
Data tenancy tiers represent levels of achievement and help ascertain where a system falls on a continuous improvement scale.
-
Absent. Characterizes a level of achievement which is unaware and nonexistent.
-
Exploratory. Characterizes a level of achievement which is investigative, informal, unstructured, tactical, ad hoc, lightly documented and siloed.
-
Defined. Characterizes a level of achievement which is consistent, standardized, developed, documented, formalized and aligned with the enterprise.
-
Implemented. Characterizes a level of achievement which is recognizable, adopted, deployed, trained, institutionalized, communicated, managed and enforced.
-
Optimized. Characterizes a level of achievement which is measurable, refined to best practice, automated, frictionless, flexible, proactive, of high quality and strategic.
Viewpoints
Data tenancy is an ecosystem of management and enforcement components working together to isolate data and enable compliance with data requirements. Ecosystem components are an effective lens into data tenancy and serve as viewpoints in the model. The ecosystem illustrated in Figure 1 is a minimum model which can expand to match individual service capabilities.
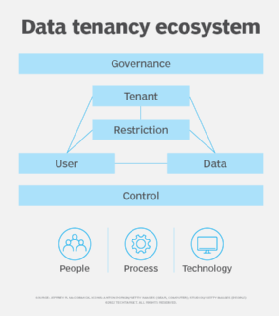
User is an entity which interacts with data including persons, proxies, services, systems, processes and bots. In a SaaS service, users represent respective tenants. A managed service offering will also include service personnel users supporting the product on behalf of the tenant.
User information includes identity, relevant attributes, user-to-tenant binding with respect to authorization, user-to-data binding with respect to access and user-to-restriction binding with respect to constraints.
Tenant is an entity such as a person, organization or process, perhaps in combination other things such as a product, which stores data in repositories and requires data isolation and selective user interaction.
Tenant information includes identity, relevant attributes, profile, data assets, tenant-to-user binding with respect to authorization, tenant-to-data binding with respect to tagging and tenant-to-restriction binding with respect to constraints.
Data includes business data stored in single and multi-tenant datasets such as databases or object stores with attributes uniquely identifying subsets of tenant data. Single tenancy is where a single tenant's data is physically fenced off in a siloed dedicated data asset. Multi-tenancy is where data from multiple tenants is co-mingled in a shared data asset and architected such that the data of each tenant is physically integrated and logically isolated.
Data information includes tenant identified business attributes, data-to-user binding with respect to access, data-to-tenant binding with respect to tagging and data-to-restriction binding with respect to constraints.
Restriction includes the management of data related contractual obligations, regulatory compliance, privacy rights and conditions from other sources. Restrictions fall into the following categories:
- Data access. Only authorized users have access to tenant-level data.
- Data use. Use tenant data for purposes in compliance with restrictions.
- Data sharing. Data is only disseminated or disclosed with authorization or consent.
Restriction information includes requirements, restriction-to-user binding with respect to constraints, restriction-to-tenant binding with respect to constraints and restriction-to-data binding with respect to constraints.
Governance is a process of overseeing data tenancy across all aspects of the architecture. As custodians, providers have the responsibility to steward data tenancy according to contractual obligations, regulatory compliance, privacy rights and conditions from other sources.
Governance oversight includes tenant, user, restriction, data, and control management and enforcement.
Control includes the management and enforcement of safeguards which ensure compliance with data restrictions. Categorize controls as security, privacy or financial. Most controls apply to digital interactions and are enforced with technical means while policy and training cannot codify or enforce other controls.
Measures
People, process and technology measures assess the extent and quality of data tenancy across viewpoints. Evaluate each viewpoint against benchmarks including standards, best practices, reference architectures, policies and requirements.
People is a measure of resources supporting data tenancy. It focuses on the following:
- organizational roles and responsibilities;
- talent management and deployment model;
- practitioner communities and centers of excellence;
- supplemental work force augmenting internal resources; and
- organizational effectiveness.
Process is a measure of methods supporting data tenancy. Areas of focus include the following:
- policies and standards
- compliance
- process management and enforcement
- functional requirements
- process effectiveness
Technology is a measure of architecture supporting data tenancy. It focuses on the following:
- end-to-end architecture
- hardware and software infrastructure
- business alignment
- nonfunctional requirements
- technology effectiveness
Putting it all together
The maturity model shown in Figure 2 provides a graphical view of a fictitious data tenancy evaluation. Documented rationale and details would reinforce the scoring with evidence-based facts.
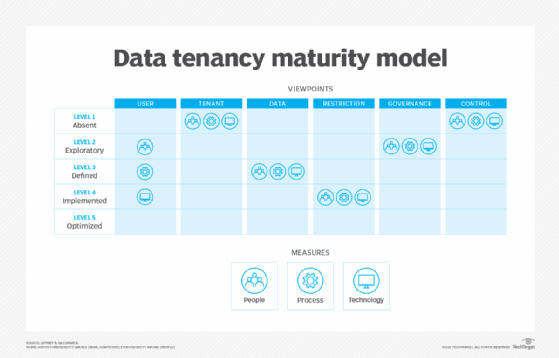
This perspective helps illustrate current data tenancy achievement and where to target improvement to reach a desired maturity. From the model, it is visually evident there are varying degrees of management achievement across viewpoints with no enforcement via controls.
Assessing the achievement of a data tenancy is an important step in understanding how well a service offering delivers this capability in response to requirements. Organizations which excel at this capability will not only protect the data of their customers but enjoy a competitive advantage in the marketplace.







