What is HAProxy?
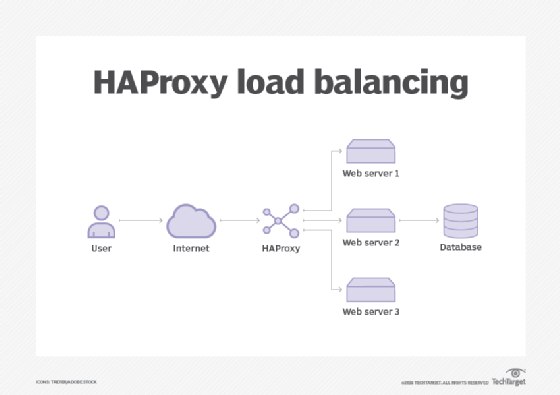
HAProxy is a high-performance, open source load balancer and reverse proxy for TCP and HTTP applications. HAProxy distributes workloads and improves website and application performance. Performance improvements include minimized response times and increased throughput. High-traffic services, such as GitHub and X (formerly Twitter), use HAProxy.
Load balancers distribute workloads across computers, networks, disk drives or central processing units. HAProxy, included in many distributions of Linux, is one of the leading standards in software load balancing.
Although HAProxy is open source, HAProxy Technologies offers a commercial option called HAProxy Enterprise. It includes an enterprise suite of add-ons, expert support and professional services.
HAProxy features
HAProxy includes the following services:
- Layer 4 TCP and Layer 7 HTTP load balancing.
- Protocol support for HTTP, HTTP/2, gRPC and FastCGI.
- Secure Sockets Layer (SSL) and Transport Layer Security termination.
- Dynamic SSL certificate storage.
- Content switching, which enables users to select server pools on request.
- Content inspection, which enables users to block unexpected protocols.
- Transparent proxying, which lets users connect to a server with a client IP address.
- Detailed logging enables users to view real time request data.
- Command-line interface (CLI) for server management enables users to make changes, such as turning servers on or off.
- HTTP authentication.
- Multithreading.
- URL rewrites.
- Health checking.
- Rate limits.
- Scalability to connect to thousands of backends.
HAProxy security
HAProxy users consider the tool secure because it has few vulnerabilities. HAProxy contains features that limit the attack surface in case of a security issue.
HAProxy security features include the following:
- Isolates itself with chroot.
- Drops to nonprivileged users and groups upon startup.
- Avoids disk access after initialization.
HAProxy also makes other systems more secure. For example, HAProxy inspects traffic and monitors a client's behavior over a series of requests, then blocks the client if it seems malicious. Users can configure access control lists that define policies for when to permit access based on metadata found within a request. HAProxy also enables rate limits, as well as IP blocklists and allowlists.







