What is a proxy firewall?
A proxy firewall is a network security system that protects network resources by filtering messages at the application layer. It is also called an application firewall or gateway firewall and is the most secure type of firewall.
How does a proxy firewall work?
A proxy firewall stands between an internal network and the public-facing internet. It has its own Internet Protocol (IP) address, which prevents data packets from directly passing between the internal and external networks. When a user or device on the internal network needs to access the internet, the proxy server establishes the connection to the requested service. Next, it reviews the traffic for security threats and evaluates it against the organization's security policies.
Following these evaluations, and if no threats are detected, it allows the connection. If it does detect a threat, it blocks the user from accessing that web resource -- site or application. Either way, the firewall obscures the details of the internal network and users from the external network, strengthening security and helping to minimize external threats.
Modern proxy firewalls use many tactics to analyze application traffic and filter it on discovering threats. These include deep packet inspection in which incoming data packets are inspected and analyzed before the firewall allows authorized access or blocks unauthorized access.
How are proxy firewalls used?
Proxies can be installed in the network itself -- between the internet and the internal network -- or on each individual computer. They can also be deployed within a hardware device, such as a router or firewall.
In general, a proxy firewall acts as a barrier between authorized users on an internal network and unauthorized users on an external network, like the internet. It can also help accomplish the following:
- Protect critical systems from unauthorized access.
- Ensure that only authorized users have access to the resources of a computer network.
- Filter out unwanted messages and packets on an internet network.
- Protect against network intrusion and espionage.
Another use of proxy firewalls is to restrict access to sensitive, malicious or inappropriate sites. For example, organizations can prevent employees from accessing Facebook or X, formerly Twitter, during working hours, while still allowing them to access their work-related accounts.
Benefits of proxy firewalls
Proxy firewalls are an essential element in a modern cybersecurity infrastructure. By inspecting traffic at the application layer, proxy firewalls help protect organizations against many kinds of threats, such as viruses, malware and phishing attacks. In addition, they can examine the entire network packet, rather than just the network address and port number. Such deep inspections of traffic provide more insights regarding threats, enabling organizations to implement stronger controls.
Another benefit of proxy firewalls is that they provide a high level of anonymity. They thus safeguard internal IP addresses and provide stronger defense against unauthorized or malicious intrusions. Also, by blocking access to specific sites -- deemed unsafe or dangerous by security teams -- they ensure that users on the internal network view only safe content.
Network managers can also deploy proxy firewalls to improve website load times and optimize bandwidth, due to their ability to cache web content and compress data. Caching enables faster retrieval of web content, enhancing users' browsing experiences.
Other benefits of proxy firewalls include the following:
- Logging capabilities. Proxy firewalls include extensive logging capabilities. Logs can be a valuable resource for security administrators when dealing with security incidents.
- Threat assessment. Marcus J. Ranum, who is credited with coming up with the idea of a proxy firewall, describes how programmers can assess the threat levels of application protocols and deploy error and attack detection and validity checking.
- Control and granularity. Proxy firewalls offer more control and granularity than other types of firewalls. This is because they can be configured to apply specific levels of security to individual users and groups. In addition, they provide detailed access logs about user activities to help administrators with auditing.
Disadvantages of proxy firewalls
When deciding how or if to use proxy firewalls, it's important to assess both their benefits and disadvantages.
The disadvantages of proxy firewalls include the following:
- Possible to disable. Many users disable proxy firewalls when they are unable to access certain websites or applications on the internet. This can open security holes that allow threat actors to gain unauthorized access to the organization or its resources.
- Slow performance. Proxy firewalls can slow internet connections. Because they operate as a third party between the internet and an internal computer, they establish an additional connection for each outgoing and incoming packet. This can create a bottleneck in traffic flows and slow down performance.
- Single point of failure. Proxy firewalls can also become a single point of failure in the system, weakening overall security. One way to avoid this problem is to implement strong failover and redundancy tactics.
Proxy firewall vs. proxy server
A proxy firewall is a type of proxy server. However, not all proxy servers are proxy firewalls.
A proxy server acts as an intermediary between client devices and an internet server, passing requests and responses between them. A proxy firewall doesn't have this capability. When a client sends a request to access a website on the internet, it gets routed to the proxy server, which then retrieves the information from the site and forwards it to the device browser. This enables the user to view the requested website. The main purpose of a proxy server is to secure data exchange between users and websites and to prevent threat actors from entering a private network.
It's possible to set up a proxy server as a proxy firewall to analyze and filter incoming network traffic and then allow or deny it depending on safety levels and security rules. If it detects a potential threat, such as malware or viruses, the proxy server blocks the traffic. It can also detect network intrusions and help security teams to enforce security policies.
In addition to its filtering and security capabilities, a proxy server can also cache webpages and compress data to reduce bandwidth demands. It can also be used to hide user information or to help users connect to services that are otherwise blocked by their organization's security team.
Proxy firewall vs. traditional firewall
A proxy firewall acts as a gateway between internal users and the internet. It can be installed on an organization's network or on a remote server that is accessible by the internal network. It provides security to the internal network by monitoring and blocking traffic that is transmitted to and from the internet.
Where a proxy firewall can filter traffic and evaluate and process access requests, a traditional firewall can only filter traffic. It simply acts as a gateway between two networks to block unwanted external traffic and protect computers and networks from unauthorized access and cyberattacks.
A proxy firewall offers enhanced security and user privacy compared to traditional firewalls. This is because proxy firewalls can perform deep inspections on incoming traffic and mask users' IP addresses. Traditional firewalls do not have these capabilities.
Finally, proxy firewalls operate at the application layer to provide stronger protection from external threats. In contrast, traditional firewalls operate at the network or transport layer.
Filtering at the application level
Proxy firewalls filter traffic at the application layer, which is Layer 7 of the Open Systems Interconnection model. The technology is similar to traditional packet filtering firewalls, but proxy firewalls add an extra level of protection by thoroughly inspecting the content of data packets and by masking users' IP addresses.
Proxy firewalls are often used as the first layer of defense in a secure web or application infrastructure. In this regard, they protect the network from external threats, while ensuring that internal web services and applications can be used safely with minimal or no impact on performance.
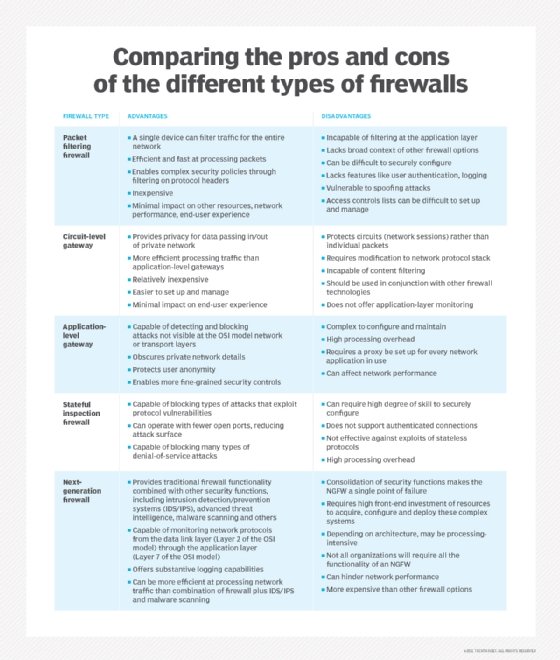
There are many kinds of firewalls, including firewall as a service. Find out about them as part of this guide to secure access service edge.








