
alphaspirit - Fotolia
2019 Verizon DBIR highlights cyberespionage, nation-state attacks
The 2019 Verizon Data Breach Investigations Report showed significant increases in cyberespionage and nation-state activity. It also painted a gloomy picture for email threats.
Cyberespionage and nation-state actors are taking up increasingly large slices of the threat landscape pie, according to the 2019 Verizon Data Breach Investigations Report.
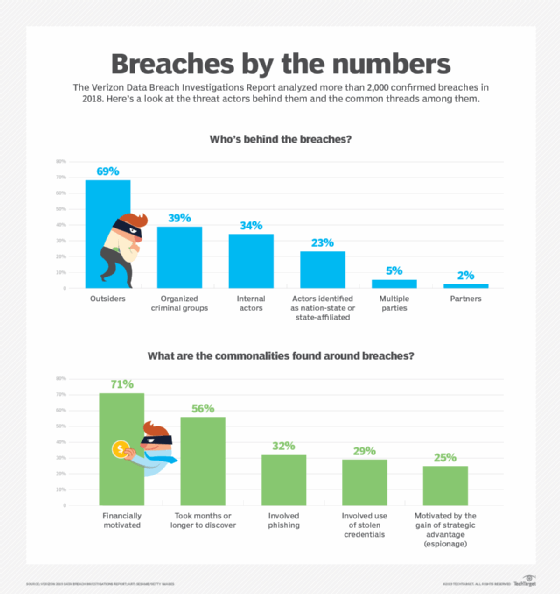
The 2019 Verizon DBIR analyzed 41,686 security incidents, of which 2,013 were confirmed data breaches, with data provided by 73 sources. The report showed a sharp uptick in nation-state attacks last year; 23% of the analyzed breaches were attributed to nation states or state-sponsored actors, compared to just 12% in the 2018 report. The 2019 Verizon DBIR also stated 25% of breaches were motivated by cyberespionage, compared to just 13% of breaches in last year's report.
Verizon defines cyberespionage as attacks motivated by the gain of a strategic advantage, rather than financially motivated attacks.
Dave Hylender, senior risk analyst at Verizon and a contributor to the 2019 DBIR, said the increase of espionage-driven breaches was one of the trends that stood out to him. "That was interesting, because the vast majority of those kinds of breaches [96%] involved nation-state actors," he said.
Hylender said it's unclear whether nation-state attacks are actually increasing or if attribution is simply getting better. The Verizon DBIR showed historical data indicating increases in cyberespionage activity generally coincide with drops in financially motivated attacks. This year's DBIR reported a small drop in financially motivated breaches, from 76% in the 2018 to 71%.
The authors also said historical patterns are affected by changes in data sources for the Verizon DBIR, as well as the presence of large-scale campaigns.
"The ebb and flow of the financial and espionage motives are indicative of changes in the data contributions and the multi-victim sprees," the report stated.
Public sector under siege
The rise of cyberespionage and nation-state activity was bad news for two spaces: the information industry and the public sector.
"An eye-opening 36% of external attackers [for information industry breaches] were of the state-affiliated variety, statistically even with organized crime," the report said.
The Verizon DBIR also noted that cyberespionage "is rampant in the public sector," with the number of espionage-driven breaches for government entities jumping 168% year over year. The authors said while the number of incidents and breaches in the public sector was roughly the same as in last year's report, "the makeup of the breaches has seen some change."
While nation-state groups are often described as sophisticated actors with advanced skills and tools, the Verizon DBIR said 78% of cyberespionage-related incidents involved phishing, compared to just 32% of overall breaches involving phishing.
Malcolm Harkins, chief security and trust officer at BlackBerry Cylance, based in Irvine, Calif., said many breaches are attributed to advanced threat actors, but those attacks often begin with simple phishing email messages.
"It doesn't take an advanced actor to create an email that looks like it came from your boss, your wife or your kid, then take a picture from [a] social media site or something else and send you an email," Harkins said. "And guess what? You're going to click on the damn thing."
The 2019 Verizon DBIR did offer some positive news. Data from simulated phishing exercises, provided by third-party vendors, showed a continued decline in the click rates to just under 3%.
"The numbers on the phishing simulations are encouraging," Hylender said. "But if you've read these reports over the years, then you know it's a tried-and-true attack method.
Email threats
Email has been a widely known and popular vector for threat actors for some time, but the 2019 Verizon DBIR painted a grim picture for the communication channel beyond basic phishing attacks. According to the report, which included "data received from millions of malware detonations," the median organization received more than 90% of their detected malware through email messages.
The Verizon DBIR highlighted that, in 60% of web application attacks, the app in question was the front end to cloud-based email servers. The report also noted that most compromised credentials were to cloud-based mail servers.
"There was an uptick in actors seeking these credentials to compromise a user's email account," the report said.
"That's an indication of where the attackers are going," Hylender said. "And it shows me that [organizations] are not doing enough to protect their credentials."
Once threat actors gain access to email accounts and the underlying email server, he said, they send phishing email messages from those accounts, initiate business email compromise (BEC) campaigns or harvest additional credentials to continue moving laterally though the organization.
Justin Harvey, managing director and global incident response lead for Accenture Security, said he's seen a number of incidents in the last year involving web apps and compromised credentials.
"Because a lot of infrastructure is in the cloud, it's very easy to get access to a lot of those services like SharePoint and OWA [Outlook Web App]," he said. "We have seen people branch out from there by compromising administrators and gaining full access to the environment."
Hylender said while there are sophisticated ways to prevent phishing attacks and protect credentials, he advised organizations to "start with the basics" by implementing two-factor authentication.
Harvey agreed and said most of the email threats and BEC attacks he sees are only successful because users had no multifactor authentication.
"The first order of business, in a lot of these cases, is to get the organization on Office 365, get them on Windows 10 and get on multifactor authentication," he said. "And Microsoft has made that very easy."
Despite concerns about the security of SMS-based 2FA, Harvey said users are better off using it than not having it at all.







